Menyelidiki file
Anda dapat menggunakan Google Security Operations untuk menelusuri data Anda untuk menemukan file tertentu berdasarkan nilai hash MD5, SHA-1, atau SHA-256-nya.
Jika informasi tambahan tersedia untuk hash file yang ditemukan dalam akun Google SecOps pelanggan, informasi tambahan ini akan ditambahkan ke peristiwa UDM terkait secara otomatis. Anda dapat menelusuri peristiwa UDM ini secara manual menggunakan Penelusuran UDM atau menggunakan aturan.
Melihat hash file
Untuk melihat hash file, Anda dapat:
Melihat file langsung di tampilan Hash file
Membuka tampilan Hash file dari tampilan lain
Melihat file langsung di tampilan Hash file
Untuk membuka tampilan Hash file secara langsung, masukkan nilai hash di kolom penelusuran Google SecOps, lalu klik Search.
Google SecOps memberikan informasi tambahan tentang file, termasuk berikut ini:
Mesin partner yang mendeteksi: Vendor keamanan lain yang telah mendeteksi file tersebut.
Properti/metadata: Properti file yang diketahui.
Nama file yang dikirimkan ke VT/ITW: Malware in-the-wild (ITW) berbahaya yang diketahui dan dikirimkan ke VirusTotal.
Membuka tampilan Hash file dari tampilan lain
Anda juga dapat membuka tampilan Hash file saat menyelidiki aset dalam tampilan lain (misalnya, tampilan Aset) dengan menyelesaikan langkah-langkah berikut:
Membuka tampilan investigasi. Misalnya, pilih aset untuk melihatnya dalam Tampilan aset.
Di Linimasa di sebelah kiri, scroll ke peristiwa apa pun yang terkait dengan proses atau modifikasi file, seperti Koneksi Jaringan.
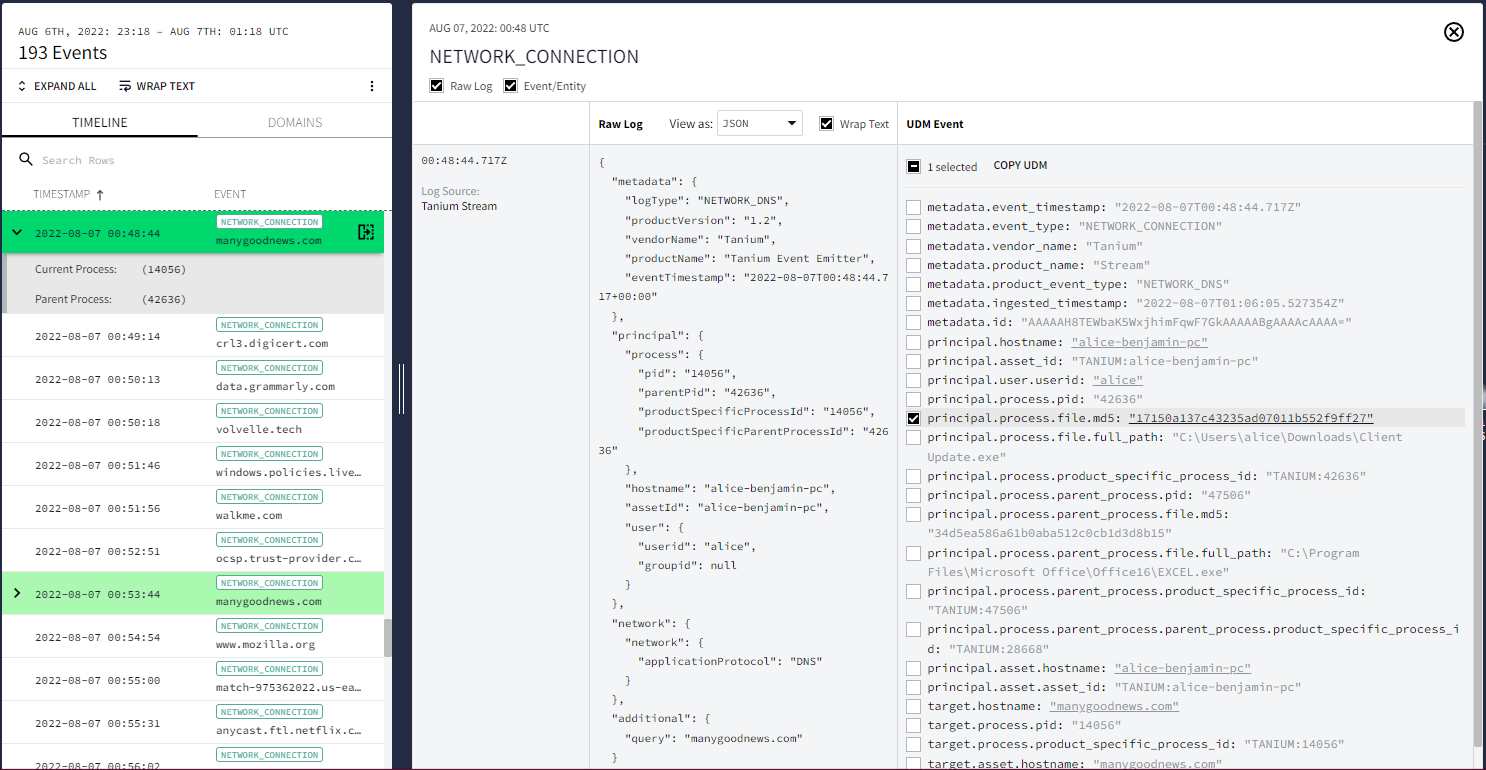 Memilih Peristiwa di tampilan Aset
Memilih Peristiwa di tampilan AsetBuka penampil Log Mentah dan UDM dengan mengklik ikon buka di Linimasa.
Anda dapat membuka tampilan Hash file untuk file dengan mengklik nilai hash (misalnya, principal.process.file.md5) dalam peristiwa UDM yang ditampilkan.
Pertimbangan
Tampilan hash memiliki batasan berikut:
- Anda hanya dapat memfilter peristiwa yang ditampilkan dalam tampilan ini.
- Hanya jenis peristiwa DNS, EDR, Webproxy, dan Pemberitahuan yang diisi dalam tampilan ini. Informasi pertama kali terlihat dan terakhir kali terlihat yang diisi dalam tampilan ini juga dibatasi untuk jenis peristiwa ini.
- Peristiwa generik tidak muncul di tampilan pilihan mana pun. Peristiwa ini hanya muncul di log mentah dan penelusuran UDM.
Perlu bantuan lain? Dapatkan jawaban dari anggota Komunitas dan profesional Google SecOps.

