Ferramentas
Visão geral
Um conjunto de ações utilitárias para manipulação de dados que potencializam os recursos do playbook.
Ações
Pesquisa de DNS
Descrição
Realiza uma busca DNS usando um resolvedor de DNS especificado.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Servidor DNS | Endereço IP | N/A | Sim | Especifique um ou mais servidores DNS separados por vírgulas. |
Exemplo
Neste cenário, estamos usando o endereço DNS público do Google 8.8.8.8 para pesquisar entidades de domínio externo.
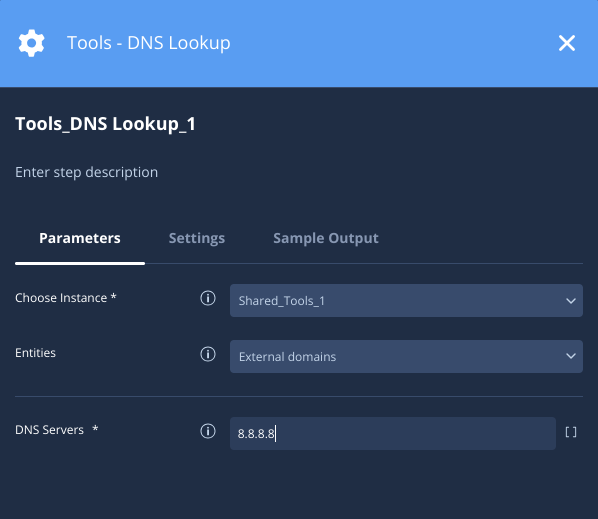
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "Entity": "WWW.EXAMPLE.ORG", "EntityResult": [{"Type": "A", "Response": "176.9.157.114", "DNS Server": "8.8.8.8"}] }
Add Or Update Alert Additional Data
Descrição
Adiciona ou atualiza campos nos dados extras do alerta. Os resultados vão aparecer em um campo chamado "OFFENSE_ID" na visão geral de alertas.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Campos JSON | JSON | N/A | Sim | Você pode inserir texto livre (para uma variável), uma string que representa um dicionário JSON (pode ser aninhado) |
Exemplo
Nesse cenário, estamos adicionando detalhes do ataque MITRE aos alertas, que serão mostrados na visão geral de alertas.
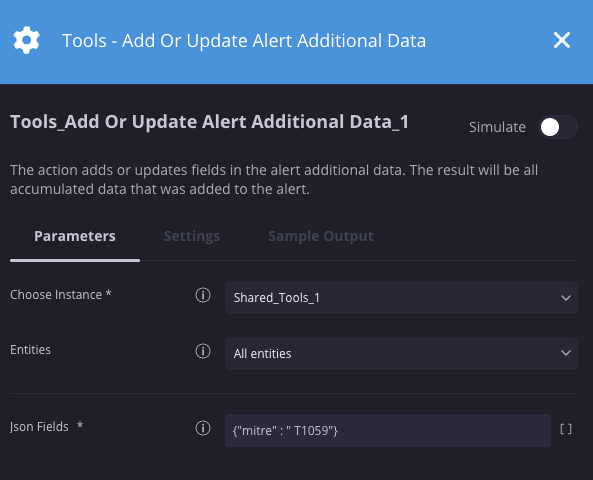
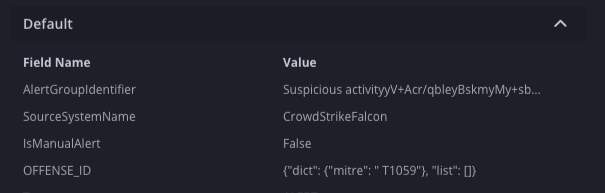
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Nº de itens no dicionário 2 -
Resultado JSON
{ "dict": {"mitre": " T1059"}, "list": [] }
Anexar o playbook a todos os alertas de caso
Descrição
Anexa um playbook ou bloco específico a todos os alertas em um caso.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Nome do playbook | String | N/A | Sim | Especifique o nome do playbook ou do bloco que será adicionado a todos os alertas em um caso. |
Exemplo
Neste cenário, estamos anexando um playbook chamado "Phishing playbook" a todos os alertas em um caso.
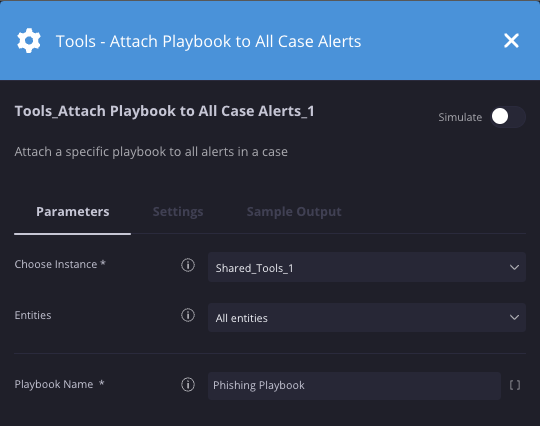
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
Anexar um playbook a um alerta
Descrição
Anexa um playbook ou bloco específico ao alerta atual.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Nome do playbook | String | N/A | Sim | Especifique o nome do playbook ou do bloco que será adicionado a todos os alertas em um caso. |
Exemplo
Nesse cenário, estamos anexando um bloco chamado "Containment Block" aos alertas atuais no caso.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
Buffer
Descrição
Converter uma entrada JSON em um objeto JSON.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| ResultValue | String | N/A | Não | Valor de marcador de posição que será retornado como o valor ScriptResult. |
| JSON | JSON | N/A | Não | JSON que será exibido no criador de expressões. |
Exemplo
Nesse cenário, o valor de entrada JSON será mostrado no criador de expressões JSON para ser usado em outras ações.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Valor de entrada do parâmetro ResultValue sucesso -
Resultado JSON
{ "domain" : "company.com", "domain2" : "company2.com" }
Receber detalhes do certificado
Descrição
Recupera detalhes do certificado de um determinado URL.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| URL para verificar | URL | expired.badssk.com | Sim | Especifique o URL de onde os detalhes do certificado serão recuperados. |
Exemplo
Neste cenário, estamos recuperando detalhes do certificado do site expired.badssl.com.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "hostname": "expired.badssl.com", "ip": "104.154.89.105", "commonName": "*.badssl.com", "is_self_signed": false, "SAN": [["*.badssl.com", "badssl.com"]], "is_expired": true, "issuer": "EXAMPLE CA", "not_valid_before": "04/09/2015", "not_valid_after": "04/12/2015", "days_to_expiration": -2762 }
Receber valor de contexto
Descrição
Recupera o valor de uma chave de contexto em um caso ou alerta.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Escopo | Lista suspensa | Alerta | Sim | Especifique o escopo dos valores de chave, seja em um caso, alerta ou global. |
| Chave | String | N/A | Sim | Especifique a chave. |
Exemplo
Nesse cenário, estamos extraindo um valor de contexto de uma chave chamada "impact" em um caso. Essa ação é usada com a ação "Definir valor de contexto", que adiciona os pares de chave-valor ao caso ou alerta.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Valor do contexto Alta
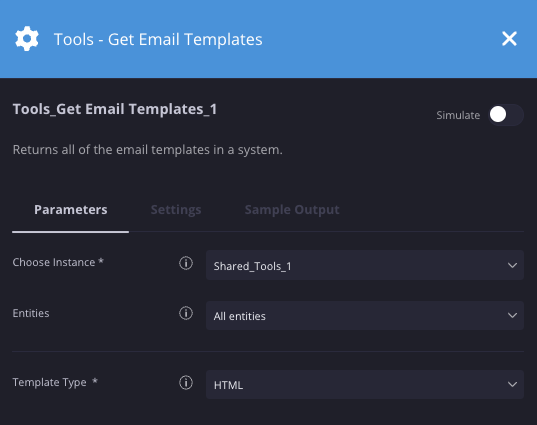
Receber modelos de e-mail
Descrição
Retorna todos os modelos de e-mail no sistema.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Tipo de modelo | Lista suspensa | Padrão | Sim | Especifique o tipo de modelo a ser retornado, padrão ou HTML. |
Exemplo
Nesse cenário, estamos retornando todos os modelos de e-mail baseados em HTML.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Resultado em JSON com código HTML Resultado em JSON mostrado abaixo -
Resultado JSON
{ "templates": [{"type": 1, "name": "test 1", "content": "<html>\n <head>\n <style type=\"text/css\"> .title\n\n { color: blue; text-decoration: bold; text-size: 1em; }\n .author\n { color: gray; }\n\n </style>\n </head>\n\n <body>\n <span class=\"title\">La super bonne</span>\n {Text}\n [Case.Id]\n </h1> <br/>\n </body>\n\n </html>", "creatorUserName": "f00942-fa040-4422324-b2c43e-de40fdsff122b9c4", "forMigration": false, "environments": ["Default"], "id": 3, "creationTimeUnixTimeInMs": 1672054127271, "modificationTimeUnixTimeInMs": 1672054127279}] }
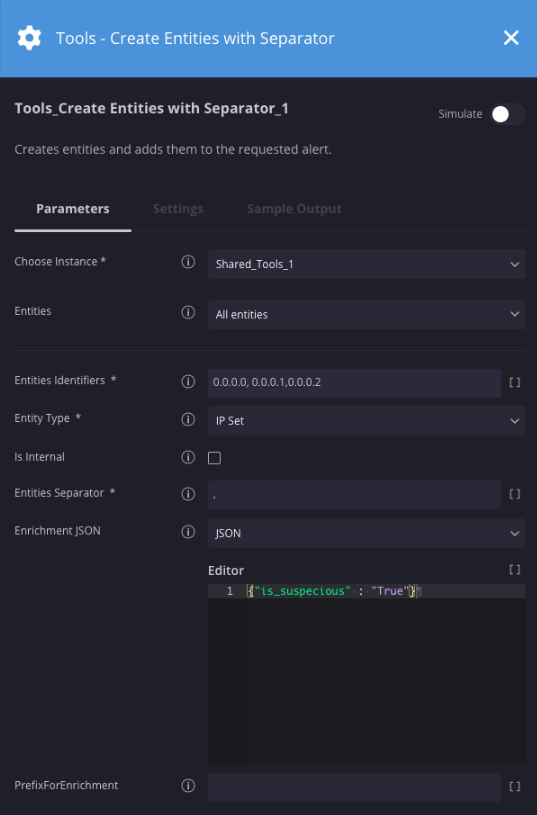
Criar entidades com separador
Descrição
Cria entidades e as adiciona ao alerta.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Identificadores de entidades | String | N/A | Sim | Especifique a entidade ou as entidades que serão adicionadas ao alerta. |
| Tipo da entidade | String | N/A | Sim | Especifique o tipo de entidade. |
| É interno | Caixa de seleção | Não selecionado | Não | Verifica se a entidade fornecida faz parte de uma rede interna. |
| Separador de entidades | String | , | Sim | Especifique o delimitador usado no campo de identificadores de entidades. |
| JSON de enriquecimento | Menu suspenso | JSON | Não | Especifique os dados de enriquecimento no formato JSON. |
| PrefixForEnrichment | String | N/A | Não | Especifique o prefixo a ser adicionado aos dados de enriquecimento. |
Exemplo
Neste cenário, vamos criar três entidades de IP e enriquecê-las com um campo chamado "is_suspicious".
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "created": ["0.0.0.0", "0.0.0.1", "0.0.0.2"], "enriched": ["0.0.0.0", "0.0.0.1", "0.0.0.2"], "failed": [] }
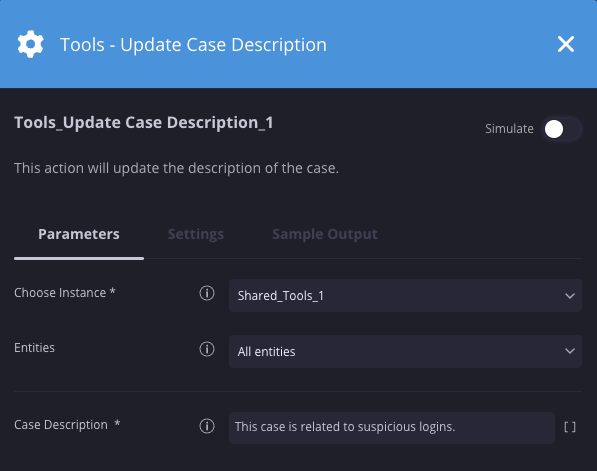
Atualizar descrição do caso
Descrição
Atualiza a descrição de um caso.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Descrição do caso | String | N/A | Sim | Especifique a descrição atualizada. |
Exemplo
Nesse cenário, atualizamos a descrição do caso para "Este caso está relacionado a logins suspeitos".
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
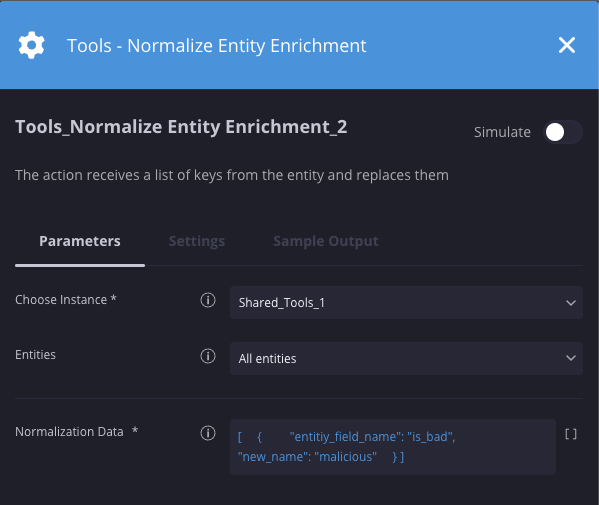
Normalizar o enriquecimento de entidades
Descrição
Recebe uma lista de chaves da entidade e as substitui.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Dados de normalização | JSON | N/A | Sim | Especifique o JSON no seguinte exemplo de formato: [ { "entity_field_name": "AT_fields_Name", "new_name": "InternalEnrichment_Name" }, { "entity_field_name": "AT_fields_Direct-Manager", "new_name": "InternalEnrichment_DirectManager_Name" }, { "entity_field_name": "AT_Manager_fields_Work-Email", "new_name": "InternalEnrichment_DirectManager_Email" } ] |
Exemplo
Nesse cenário, estamos substituindo a chave da entidade "is_bad" por "malicious".
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Número de entidades enriquecidas 5
Adicionar ao valor de contexto
Descrição
Adiciona um valor a uma propriedade de contexto existente ou cria uma nova propriedade de contexto se ela não existir e adiciona o valor.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Chave | String | N/A | Sim | Especificar a chave da propriedade de contexto |
| Valor | String | N/A | Sim | Especifique o valor a ser anexado à propriedade de contexto. |
| Delimitador | String | N/A | Sim | Especifique o delimitador usado no campo de valor. |
Exemplo
Neste cenário, estamos adicionando os valores "T1595" e "T1140" a uma chave de contexto "MITRE" já existente.
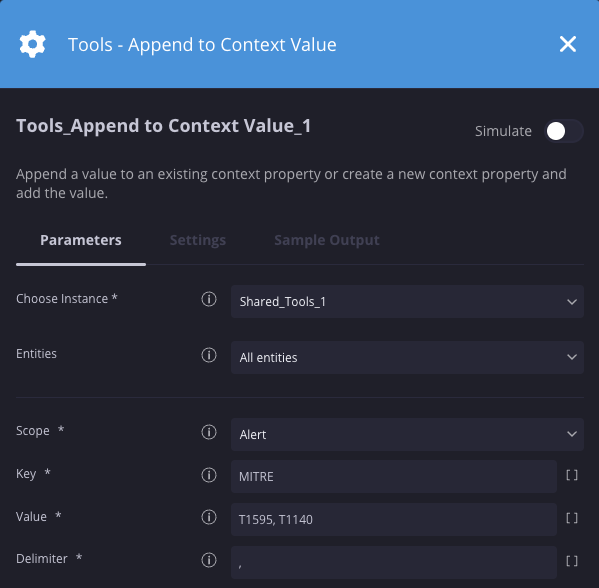
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Valores de contexto T1595, T1140
Criar relações de entidade
Descrição
Cria uma relação entre as entidades fornecidas e as entidades vinculadas. Se as entidades fornecidas não existirem, elas serão criadas.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Identificadores de entidade | String | N/A | Sim | Crie ou use identificadores de entidade ou uma lista de identificadores separados por vírgulas. |
| Tipo de identificadores de entidade | Menu suspenso | Nome do usuário | Sim | Especifique o tipo de entidade. |
| Conectar como | Menu suspenso | Origem | Sim | Conecte identificadores de entidades usando relações de origem, destino ou vinculadas aos identificadores de entidades de destino. |
| Tipo de entidade de destino | Menu suspenso | Endereço | Sim | Especifique o tipo de entidade de destino para conectar os identificadores de entidade. |
| Identificadores de entidade de destino | String | N/A | Não |
Entidades nesta lista separada por vírgulas, de
o tipo de "Tipo de entidade de destino" será vinculado às entidades no parâmetro "Identificadores de entidades". |
| JSON de enriquecimento | JSON | N/A | Não |
Um objeto JSON opcional que contém chave /
pares de valor de atributos que podem ser adicionados às entidades recém-criadas. |
| Caractere separador | String | N/A | Não | Especifique o caractere para separar a lista de entidades em "Identificadores de entidade" e/ou "Identificadores de entidade de destino". O padrão é vírgula. |
Exemplo
Neste cenário, estamos criando uma relação entre um usuário e um URL. Nesse caso, Bola001 acessou um URL de example.com.
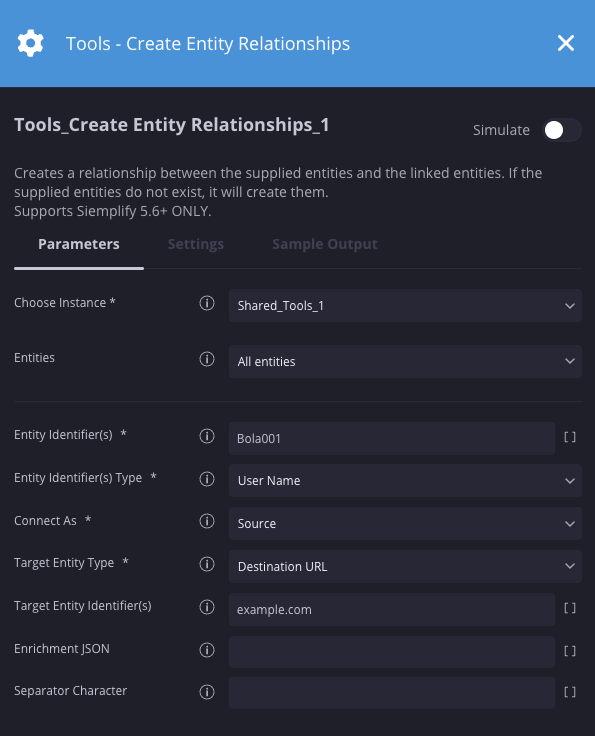
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "Entity": "Bola001", "EntityResult": {} }
Extrair domínio do URL
Descrição
Enriquece todas as entidades com um novo campo "siemplifytools_extracted_domain" que contém o domínio extraído do identificador da entidade. Se a entidade não tiver um domínio (hash de arquivo, por exemplo), ela não vai retornar nada. Além das entidades, o usuário pode especificar uma lista de URLs como parâmetro e processá-los sem enriquecer, naturalmente.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Separador | String | , | Sim | Especifique a string do separador que será usada para separar os URLs. |
| URLs | String | N/A | Não | Especifique um ou mais URLs para extrair o domínio. |
| Extrair subdomínio | Caixa de seleção | N/A | Não | Especifique se você também quer extrair o subdomínio. |
Exemplo
Nesse cenário, estamos extraindo o domínio do URL especificado.
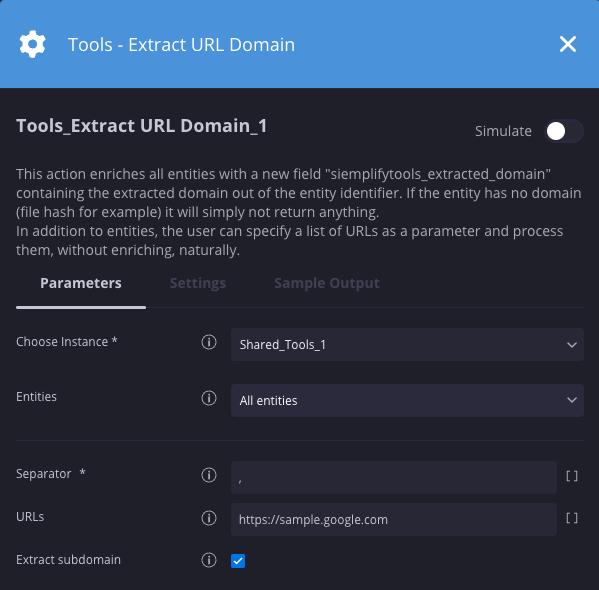
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Número de domínios extraídos 1 -
Resultado JSON
{ "Entity": "https://sample.google.com", "EntityResult": {"domain": "sample.google.com", "source_entity_type": "DestinationURL"} }
Verificar subconjunto da lista
Descrição
Verifica se os valores em uma lista existem em outra.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Original | String | N/A | Sim | Especifique a lista de itens a serem verificados. Lista JSON ou separada por vírgulas. |
| Subconjunto | Lista | N/A | Sim | Especifique a lista de subconjuntos. Lista JSON ou separada por vírgulas. |
Exemplo
Neste cenário, estamos verificando se os valores 1, 2 e 3 existem na lista original de 1, 2, 3, 4 e 5, resultando em um valor verdadeiro.
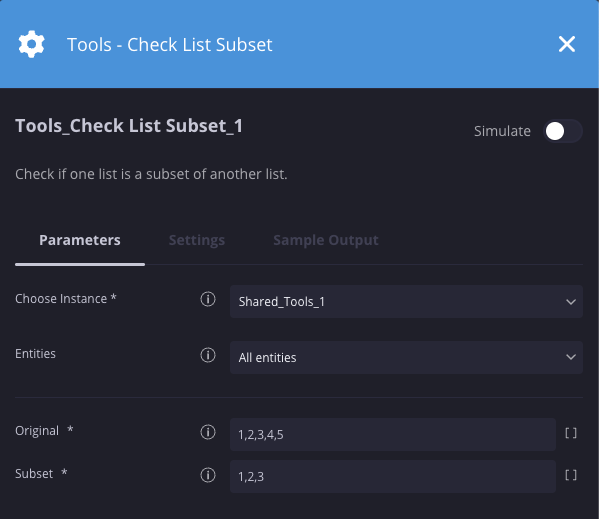
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
Adicionar informações de pontuação de alerta
Descrição
Adiciona uma entrada ao banco de dados de pontuação de alertas. A pontuação de alerta é baseada na proporção: 5 baixa = 1 média. 3 Médias = 1 Alta. 2 Alta = 1 Crítica. Tag opcional adicionada ao caso.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Nome | String | N/A | Sim | Especifique o nome da verificação que está sendo realizada no alerta. |
| Descrição | String | N/A | Sim | Especifique a descrição da verificação que está sendo realizada no alerta. |
| Gravidade | String | Informativa | Sim | Especifique a gravidade. |
| Categoria | String | N/A | Sim | Especifique a categoria da verificação realizada. |
| Origem | String | N/A | Não | Especifique a parte do alerta de que a pontuação foi derivada. Exemplo: Files, user, Email. |
| Tag do caso | String | N/A | Não | Especifique as tags a serem adicionadas ao caso. |
Exemplo
Nesse cenário, definimos a pontuação de alerta como alta devido a um resultado suspeito do VirusTotal.
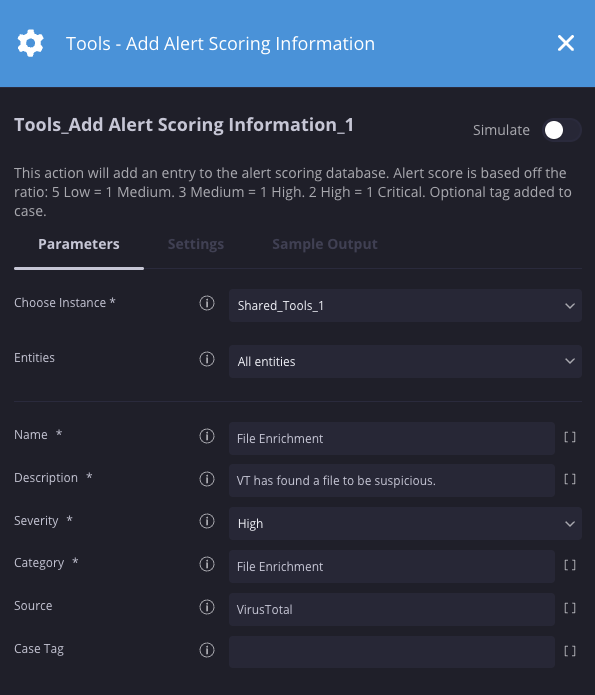
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo Alert_score Informativo, baixo, médio, alto, crítico Alta -
Resultado JSON
{ "category": "File Enrichment", "score_data": [{"score_name": "File Enrichment", "description": "VT has found a file to be suspicious", "severity": "High", "score": 3, "source": "VirusTotal"}], "category_score": 3 }
Get Siemplify Users
Descrição
Retorna a lista de todos os usuários configurados no sistema.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Ocultar usuários desativados | Caixa de seleção | Selecionado | Não | Especifique se os usuários desativados devem ser ocultados dos resultados. |
Exemplo
Nesse cenário, estamos retornando todos os usuários do sistema, incluindo os desativados.
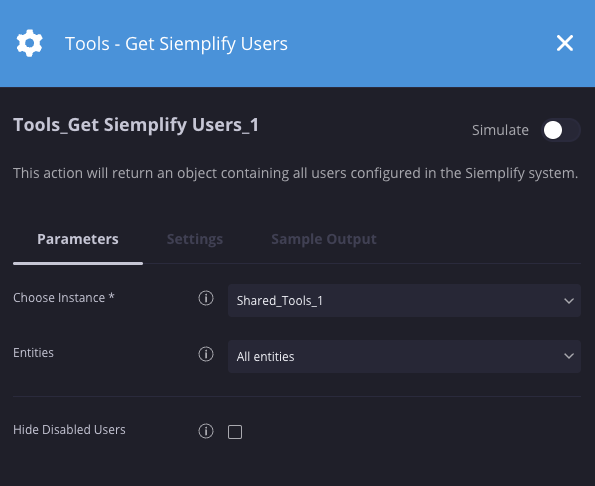
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "siemplifyUsers": [{"permissionGroup": "Admins", "socRole": "@Administrator", "isDisabled": false, "loginIdentifier": "sample@domain.com", "firstName": "John", "lastName": "Doe", "permissionType": 0, "role": 0, "socRoleId": 1, "email": "sample@domain.com", "userName": "0b3423496fc2-0834302-42f33d-8523408-18c087d2347cf1e", "imageBase64": null, "userType": 1, "identityProvider": -1, "providerName": "Internal", "advancedReportsAccess": 0, "accountState": 2, "lastLoginTime": 1679831126656, "previousLoginTime": 1678950002044, "lastPasswordChangeTime": 0, "lastPasswordChangeNotificationTime": 0, "loginWrongPasswordCount": 0, "isDeleted": false, "deletionTimeUnixTimeInMs": 0, "environments": ["*"], "id": 245, "creationTimeUnixTimeInMs": 1675457504856, "modificationTimeUnixTimeInMs": 1674957504856 }
Verificar campos de entidades no texto
Descrição
Pesquise um campo específico de cada entidade no escopo (ou vários campos usando regex) e compare com um ou mais valores. Os valores comparados também podem passar por regex. Uma correspondência é encontrada se um dos valores de regex de postagem do enriquecimento de entidade estiver em um ou mais valores pesquisados.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| SearchInData | JSON | [ { "Data": "[Event.from]", "RegEx": "(?<=@)[^.]+(?=\\.)" } ] | Sim | JSON que representa as strings em que você quer pesquisar usando este formato: [ { "Data": "", "RegEx": "" } ] |
| FieldsInput | JSON | [ { "RegexForFieldName": "", "FieldName": "body", "RegexForFieldValue": "" }, { "RegexForFieldName": ".*(_url_).*", "FieldName": "", "RegexForFieldValue": "" }, { "RegexForFieldName": "", "FieldName": "body", "RegexForFieldValue": "HostName: (.*?)" } ] | Sim |
Um JSON que descreve quais campos devem ser testados para ["RegexForFieldName": "",
"FieldName": "Nome do campo a ser pesquisado", "RegexForFieldValue": “”}] |
| ShouldEnrichEntity | String | domain_matched | Não |
Se definido como <VAL>, também vai colocar um valor de enriquecimento na entidade para ser reconhecida como "correspondente" ao valor.
A chave será <VAL> |
| IsCaseSensitive | Caixa de seleção | Não selecionado | Não | Especifique se o campo diferencia maiúsculas de minúsculas. |
Exemplo
Neste cenário, estamos verificando se uma entidade com o nome de campo "malicious" está no texto especificado.
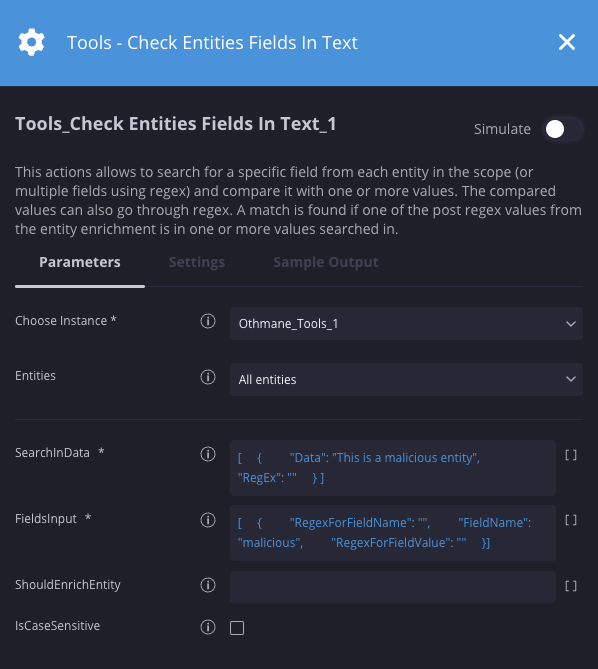
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Número de descobertas 0 -
Resultado JSON
{ "Entity": "EXL88765-AD", "EntityResult": [{"RegexForFieldName": "", "FieldName": "malicious", "RegexForFieldValue": "", "ResultsToSearch": {"val_to_search": [[]], "found_results": [], "num_of_results": 0}}] }
Receber instâncias de integração
Descrição
Retorna todas as instâncias de integração de um ambiente.
Parâmetros
Nenhum parâmetro aplicável.
Exemplo
Nesse cenário, todas as instâncias de integração em todos os ambientes serão retornadas.
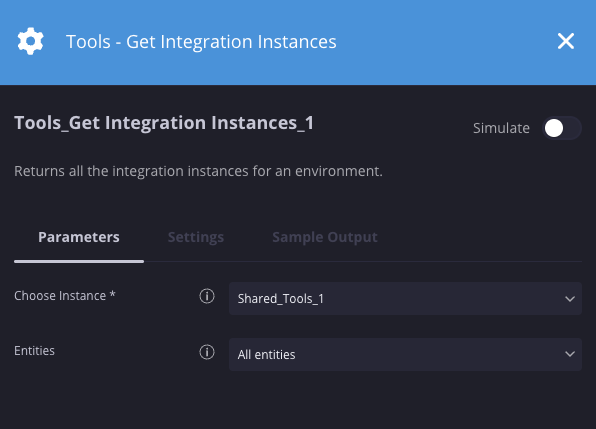
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "instances": [{"identifier": "27dee746-1857-41b7-a722-b99699b8d6c8", "integrationIdentifier": "Tools", "environmentIdentifier": "Default", "instanceName": "Tools_1", "instanceDescription": "test", "isConfigured": true, "isRemote": false, "isSystemDefault": false},{...........}] }
Manual de atraso V2
Descrição
Interrompe temporariamente a conclusão de um playbook por um período especificado.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Segundos | Número inteiro | 0 | Não | Especifique a quantidade de segundos para atrasar o playbook. |
| Minutos | Número inteiro | 1 | Não | Especifique a quantidade de minutos para atrasar o playbook. |
| Horas | Número inteiro | 0 | Não | Especifique a quantidade de horas para atrasar o playbook. |
| Dias | Número inteiro | 0 | Não | Especifique o número de dias para atrasar o playbook. |
| Expressão Cron | String | N/A | Não | Determina quando o playbook deve continuar usando uma expressão cron. Será priorizado em relação aos outros parâmetros. |
Exemplo
Nesse cenário, estamos atrasando o playbook por 12 horas e meia.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
Receber JSON de alerta original
Descrição
Retorna o resultado JSON do alerta original (dados brutos).
Parâmetros
Nenhum parâmetro aplicável
Exemplo
Nesse cenário, o JSON bruto original do alerta é retornado.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "CreatorUserId": null, "Events": [{"_fields": {"BaseEventIds": "[]", "ParentEventId": -1, "deviceEventClassId": "IRC Connections", "DeviceProduct": "IPS_Product", "StartTime": "1667497096184", "EndTime": "1667497096184"}, "_rawDataFields": {"applicationProtocol": "TCP", "categoryOutcome": "blocked", "destinationAddress": "104.131.182.103", "destinationHostName": "www.ircnet.org", "destinationPort": "770", "destinationProcessName": "MrlCS.sob", "destinationUserName": "XWTTRYzNr1l@gmail.com", "deviceAddress": "0.0.0.0", "deviceEventClassId": "IRC Connections", "deviceHostName": "ckIYC2", "Field_24": "B0:E7:DF:6C:EF:71", "deviceProduct": "IPS_Product", "deviceVendor": "Vendor", "endTime": "1667497110906", "eventId": "0aa16009-57b4-41a3-91ed-81347442ca29", "managerReceiptTime": "1522058997000", "message": "Connection to IRC Server", "name": "IRC Connections", "severity": "8", "sourceAddress": "0.0.0.0", "sourceHostName": "jhon@domain.local", "startTime": "1667497110906", "sourcetype": "Connection to IRC Server"}, "Environment": null, "SourceSystemName": null, "Extensions": []}], "Environment": "Default", "SourceSystemName": "Arcsight", "TicketId": "fab1b5a1-637f-4aed-a94f-c63137307505", "Description": "IRC Connections", "DisplayId": "fab1b5a1-637f-4aed-a94f-c63137307505", "Reason": null, "Name": "IRC Connections", "DeviceVendor": "IPS", "DeviceProduct": "IPS_Product", "StartTime": 1667497110906, "EndTime": 1667497110906, "Type": 1, "Priority": -1, "RuleGenerator": "IRC Connections", "SourceGroupingIdentifier": null, "PlaybookTriggerKeywords": [], "Extensions": [], "Attachments": null, "IsTrimmed": false, "DataType": 1, "SourceType": 1, "SourceSystemUrl": null, "SourceRuleIdentifier": null }
Ver a hora atual
Descrição
Retorna a data e a hora atuais.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Formato de data/hora | String | %d/%m/%Y %H:%M | Sim | Especifique o formato da data e da hora. |
Exemplo
Nesse cenário, estamos retornando um valor de data e hora usando o seguinte formato: %d/%m/%Y %H:%M:%S
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Valor de data e hora 03/11/2022 20:33:43
Atualizar pontuação de alerta
Descrição
Atualiza a pontuação de alerta com o valor fornecido.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Entrada | Número inteiro | N/A | Sim | Especifique o valor a ser incrementado ou decrementado (número negativo). |
Exemplo
Nesse cenário, estamos diminuindo a pontuação de alerta em 20.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Valor de entrada -20
Adicionar comentário ao registro de entidade
Descrição
Adiciona um comentário ao registro de cada entidade na pontuação do Explorador de entidades.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Usuário | Menu suspenso | @Administrator | Sim | Especifique que o usuário criou o comentário. |
| Comentário | String | N/A | Sim | Especifique o comentário que será adicionado ao registro da entidade. |
Exemplo
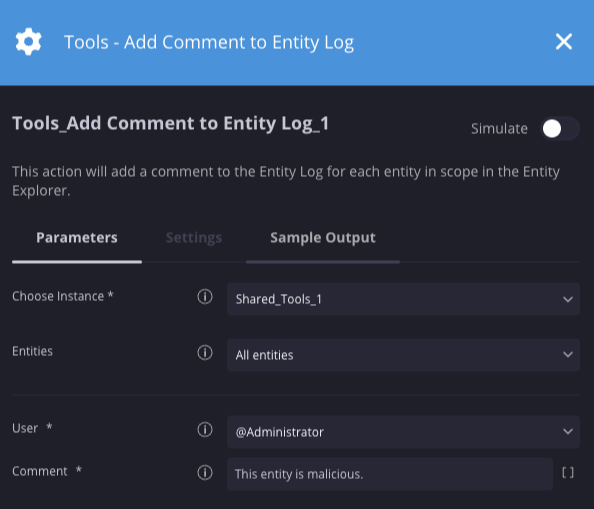
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo N/A N/A N/A
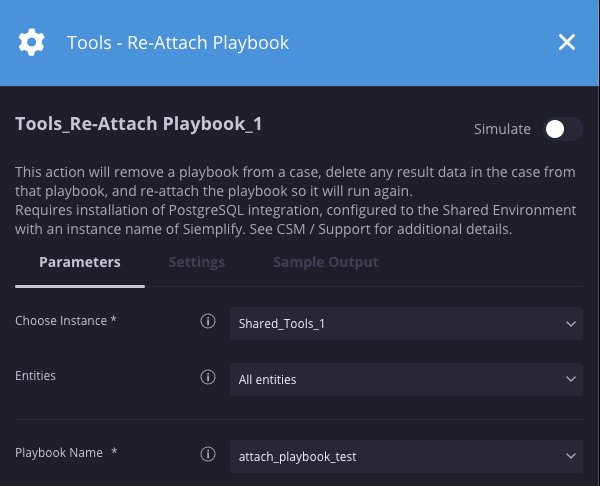
Reanexar playbook
Descrição
Remove um playbook de um caso, exclui todos os dados de resultado do caso desse playbook e anexa o playbook novamente para que ele seja executado de novo. Requer a instalação da integração do PostgreSQL, configurada para o ambiente compartilhado com o nome de instância "Chronicle SOAR". Consulte o CSM / Suporte para mais detalhes.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Nome do playbook | Menu suspenso | N/A | Sim | Especifique o playbook a ser anexado novamente. |
Exemplo
Neste cenário, estamos anexando novamente um manual chamado attach_playbook_test
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso/Configure a instância do Chronicle SOAR da integração do PostgreSQL. Verdadeiro
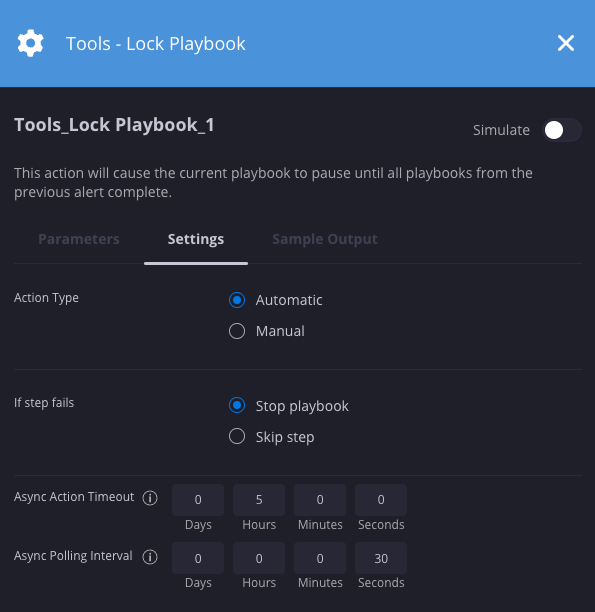
Playbook de bloqueio
Descrição
Pausa o playbook atual até que todos os playbooks do alerta anterior sejam concluídos.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Tempo limite de ação assíncrona | Números inteiros | 1 dia | Não | O tempo limite de ações assíncronas define a duração total permitida para essa ação (soma o tempo de execução de todas as iterações) |
| Intervalo de sondagem assíncrona | Números inteiros | 1 hora | Não | Defina o tempo entre cada tentativa de sondagem durante o tempo de execução de uma ação assíncrona. |
Exemplo
Nesse cenário , pausamos o playbook atual e verificamos a cada 30 segundos se todos os playbooks no alerta anterior do caso foram concluídos.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
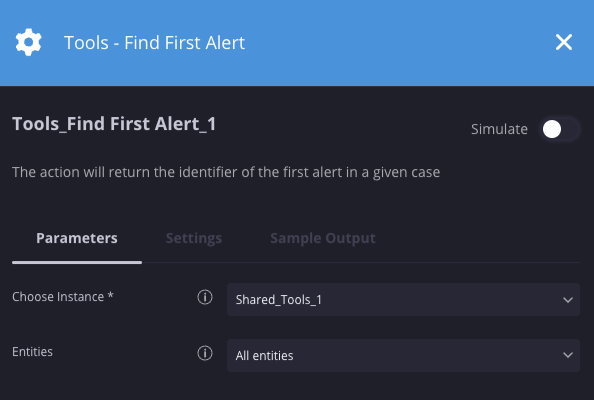
Encontrar o First Alert
Descrição
Retorna o identificador do primeiro alerta em um determinado caso.
Parâmetros
Nenhum parâmetro aplicável.
Exemplo
Nesse cenário, ele retorna o identificador do primeiro alerta no caso.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Valor do identificador de alerta IRC CONNECTIONS9A33308C-AC62-4A41-8F73-20529895D567
Domínios semelhantes
Descrição
Compara entidades de domínio com a lista de domínios definidos para o ambiente. Se os domínios forem semelhantes, a entidade será marcada como suspeita e enriquecida com o domínio correspondente.
Parâmetros
Nenhum parâmetro aplicável
Exemplo
Nesse cenário, estamos verificando se as entidades de domínio externo são semelhantes aos domínios configurados na lista de domínios nas configurações.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo look_a_like_domain_found Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "Entity" : {"EntityResult" : { "look_a_like_domains" : ["outlooks.com"]}} }
Mudar o nome do caso
Descrição
Muda o nome ou título de um caso.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Novo nome | String | N/A | Não | Especifique o novo nome do caso. |
| Somente se for o primeiro alerta | Caixa de seleção | Não selecionado | Não | Se selecionada, só vai mudar o nome do caso se a ação tiver sido executada no primeiro alerta do caso. |
Exemplo
Nesse cenário, o título de um caso será alterado para "Phishing - E-mail suspeito" somente se ele for executado no primeiro alerta.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
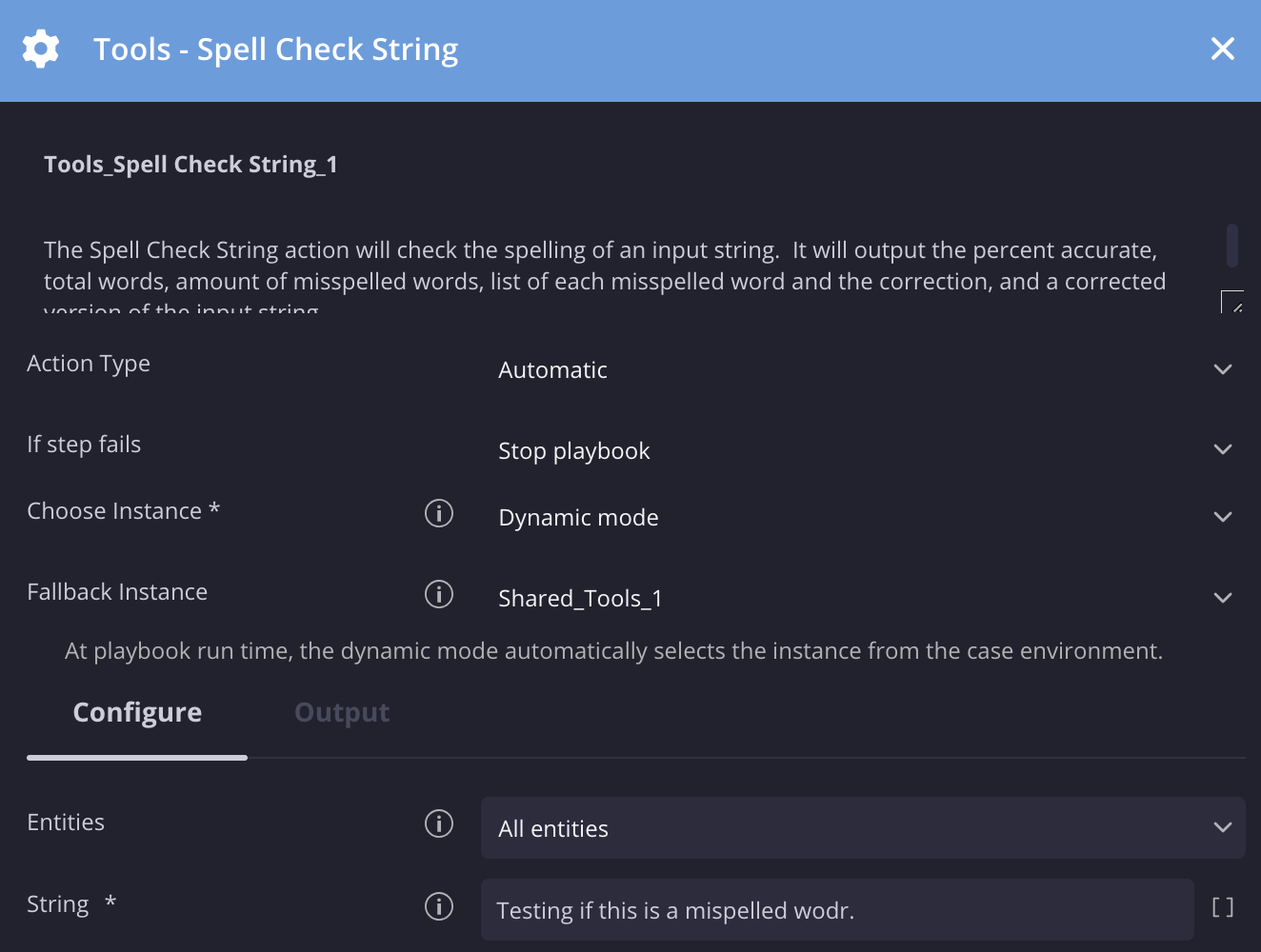
String de verificação ortográfica
Descrição
Verifique a ortografia da string de entrada. Ele vai gerar a porcentagem de precisão, o total de palavras, a quantidade de palavras com erros ortográficos, a lista de cada palavra com erro e a correção, além de uma versão corrigida da string de entrada.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| String | String | N/A | Sim | Especifique a string que será verificada quanto a erros de ortografia. |
Exemplo
Neste cenário, estamos verificando a ortografia da string de entrada "Testing if this is a mispelled wodr.".
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo accuracy_percentage Valor percentual 71 -
Resultado JSON
{"input_string": "Testing if this is a mispelled wodr.", "total_words": 7, "total_misspelled_words": 2, "misspelled_words": [{"misspelled_word": "mispelled", "correction": "misspelled"}, {"misspelled_word": "wodr", "correction": "word"}], "accuracy": 71, "corrected_string": "Testing if this is a misspelled word."}
Texto da pesquisa
Descrição
Procure o parâmetro "Pesquisar por" no texto de entrada ou faça um loop na lista "Pesquisar por Regex" e encontre correspondências no texto de entrada. Se houver uma correspondência, a ação vai retornar "true".
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Texto | String | N/A | Sim | Especifique o texto que será pesquisado. |
| Pesquisar por | String | N/A | Não | Especifique a string a ser pesquisada no campo "text". |
| Pesquisar regex | String | N/A | Não | Lista de expressões regulares que serão usadas para pesquisar a string. A regex precisa estar entre aspas duplas. Aceita listas delimitadas por vírgulas. |
| Diferenciar maiúsculas e minúsculas | Caixa de seleção | N/A | Não | Especifique se a pesquisa diferencia maiúsculas de minúsculas. |
Exemplo
Nesse cenário, estamos verificando se a palavra "malicious" existe no valor do campo "Text".
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo match_found Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "matches": [{"search": "malicious", "input": "This IOC is malicious.", "match": true}] }
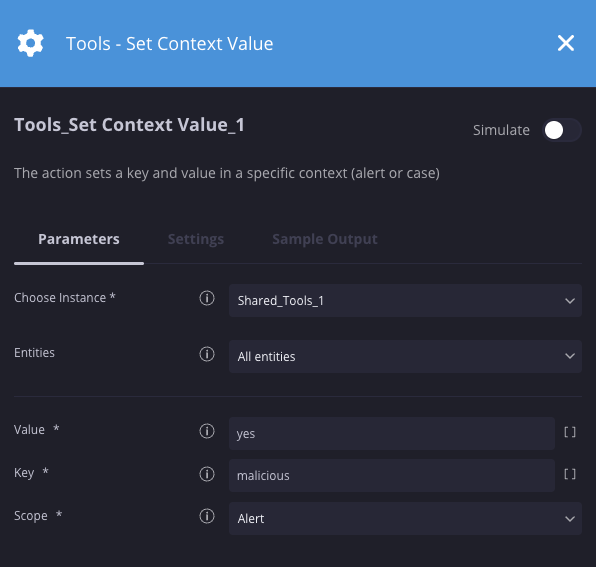
Definir valor de contexto
Descrição
Define uma chave e um valor em um contexto específico. Essa ação é usada com frequência com a ação "Extrair valor do contexto" para recuperar o valor da chave.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Valor | String | N/A | Sim | Especifique o valor do contexto. |
| Chave | String | N/A | Sim | Especifique a chave de contexto. |
| Escopo | Menu suspenso | Alerta | Sim | Especifique o escopo da atribuição de contexto (alerta, caso, global). |
Exemplo
Neste cenário, estamos definindo uma chave de contexto "malicious" com o valor "yes".
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
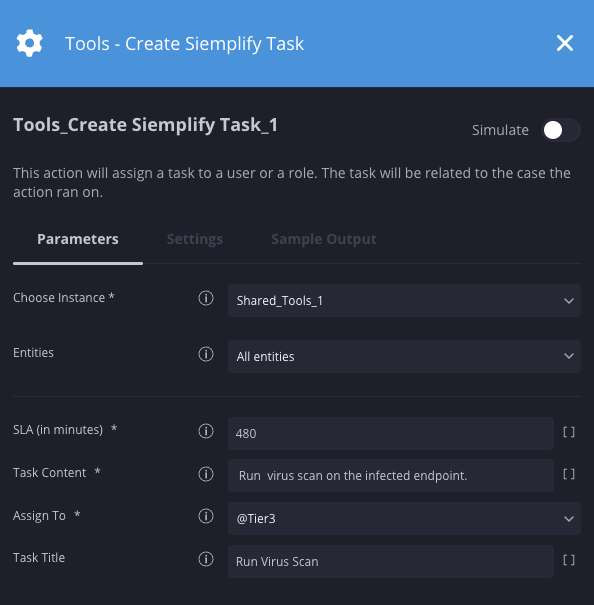
Criar tarefa do Siemplify
Descrição
Atribui uma tarefa a um usuário ou função. A tarefa vai estar relacionada ao caso em que a ação foi executada.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Título da tarefa | String | N/A | Não | Especifique o título da tarefa. |
| SLA (em minutos) | Número inteiro | 480 | Sim | Especifique o tempo em minutos que o usuário/função atribuído tem para responder à tarefa. |
| Conteúdo da tarefa | String | N/A | Sim | Especifique os detalhes da tarefa. |
| Atribuir a | Menu suspenso | N/A | Sim | Especifique o usuário ou a função a que a tarefa será atribuída. |
Exemplo
Nesse cenário, uma tarefa é criada instruindo o nível 3 a executar uma verificação de vírus.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
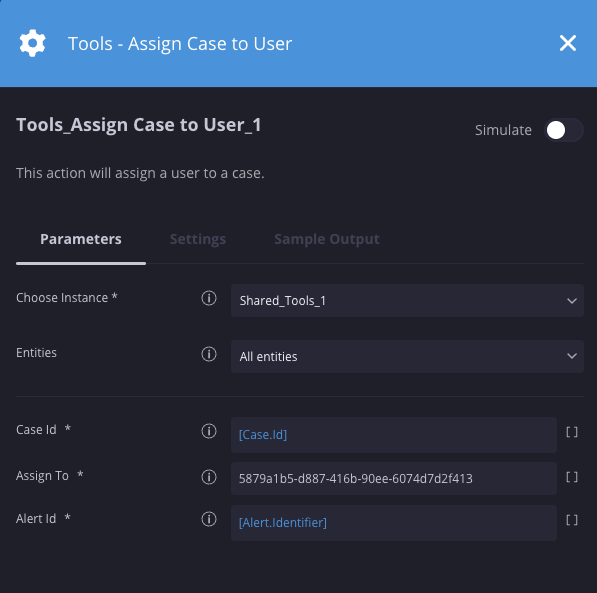
Atribuir caso ao usuário
Descrição
Atribui um caso a um usuário.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| ID do caso | String | N/A | Sim | Especifique o ID do caso. Use [Case.Id] para o caso atual. |
| Atribuir a | String | @Admin | Sim | Especifique o usuário a quem atribuir um caso. Este é o ID do usuário. Use a ação "Get Siemplify Users" para recuperar o ID de um usuário específico. |
| ID do alerta | String | Sim | Especifique o ID do alerta. Use [Alert.Identifier]. |
Exemplo
Nesse cenário, estamos atribuindo o caso atual a um usuário específico usando o ID dele.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
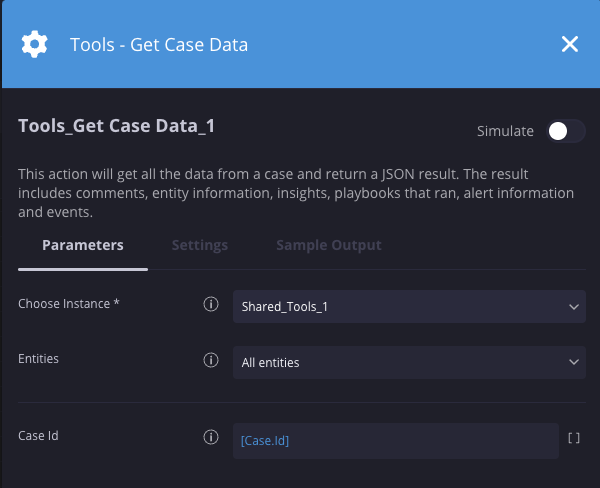
Receber dados do caso
Descrição
Recupera todos os dados de um caso e retorna um resultado JSON. O resultado inclui comentários, informações de entidades, insights, playbooks executados, informações e eventos de alerta.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| ID do caso | Número inteiro | N/A | Não | Especifique o ID do caso a ser consultado. Se deixado em branco, o caso atual será usado. |
Exemplo
Nesse cenário, estamos recuperando detalhes do caso atual.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "wallData": [{"commentForClient": null, "comment": null, "modificationTimeUnixTimeInMsForClient": 0, "creatorUserId": "8f8er8d6-ee8b-478e-9ee592-cc27e9addda13b", "id": 6357, "type": 5, "caseId": 36902, "isFavorite": false, "modificationTimeUnixTimeInMs": 1680717397165, "creationTimeUnixTimeInMs": 1680717397165, "alertIdentifier": "SUSPICIOUS ACTIVITY991C7837-1EE9-4EEA-AE7B-975366CA2EAE"}, {"actionTriggerType": 0, "integration": "Tools", "executingUser": null, "playbookName": "New Playbook", "playbookIsInDebugMode": true, "status": 5, "actionProvider": "Scripts", "actionIdentifier": "Tools_Get Case Data_1", "actionResult": "Action started", "alertIdentifiers": ["SUSPICIOUS ACTIVITY991C7837-1EE9-4EEA-AE7B-975366CA2EAE"], "creatorUserId": null, "id": 7677, "type": 3, "caseId": 0, "isFavorite": false, "modificationTimeUnixTimeInMs": 1680717397401, "creationTimeUnixTimeInMs": 1680717397401, "alertIdentifier": null}], "alerts": [{"ticketId": "d21ebvcxzb88-35vc35-46b4-9edd08-063696d7cc092", "status": 0, "identifier": "SUSPICIOUS ACTIVITY991C7837-1EE9-4EEA-AE7B-975366CA2EAE", "hasWorkflows": true, "workflowsStatus": 1, "sourceSystemName": "CrowdStrikeFalcon", "securityEventCards": [{"caseId": 36902, "eventId": "5fde7844-0099-4c5d-a562-63e2d0deb7e5", "alertIdentifier": "SUSPICIOUS ACTIVITY991C7837-1EE9-4EEA-AE7B-975366CA2EAE", "eventName": "CustomIOAWinLowest", "product": "Falcon", "sources": [{"isValid": true, "identifier": "172.30.202.229", "type": "ADDRESS"}, {"isValid": true, "identifier": "EXLAB2019-AD", "type": "HOSTNAME"}, {"isValid": true, "identifier": "E019-AD$", "type": "USERUNIQNAME"}], "destinations": [], "artificats": [{"isValid": true, "identifier": "MPCMDRUN.EXE", "type": "FILENAME"}, {"isValid": true, "identifier": "60D88450B376694DC55EB8F40B0F79580D1DF399A7BDF", "type": "FILEHASH"}], "port": null, "outcome": null, "time": "2023-03-01T19:51:00Z", "deviceEventClassId": "Indicator of Attack", "fields": [{"isHighlight": true, "groupName": "HIGHLIGHTED FIELDS", "hideOptions": false, "items": [{"originalName": "startTime", "name": "Start Time", "value": "1680615463369"}, {"originalName": "endTime", "name": "End Time", "value": "1680615463369"}]}, {"isHighlight": false, "groupName": "Default", "hideOptions": false, "items": [{"originalName": "cid", "name": "cid", "value": "27fe4e4760b8476b2b6650e5a74"}, {"originalName": "created_timestamp", "name": "created_timestamp", "value": "2023-03-01T19:51:11.387187948Z"}........................ }
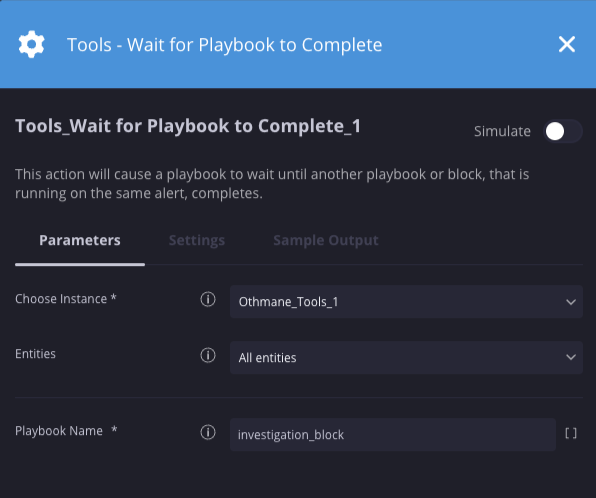
Aguardar a conclusão do manual
Descrição
Pausa o playbook atual até que outro playbook ou bloco, que está em execução no mesmo alerta, seja concluído.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Nome do playbook | String | N/A | Não | Especifique o nome do bloco ou playbook que você quer concluir primeiro. |
Exemplo
Nesse cenário, pausamos o playbook atual até que o "bloqueio de investigação" em execução no mesmo alerta seja concluído.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro
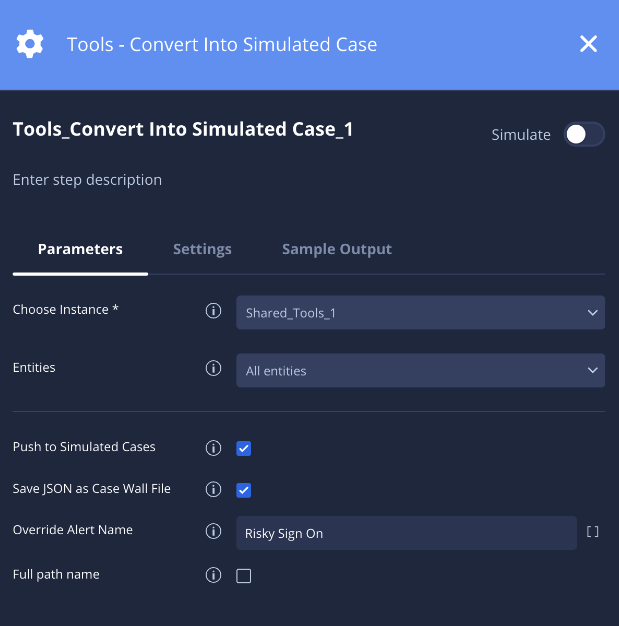
Converter em caso simulado
Descrição
Converte um caso em um caso simulado que pode ser carregado na plataforma.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Enviar para casos simulados | Caixa de seleção | Não selecionado | Não | Se selecionado, o caso será adicionado à lista de casos simulados disponíveis. |
| Salvar JSON como arquivo de parede de casos | Caixa de seleção | Selecionado | Não | Se selecionado, um arquivo JSON que representa o caso será salvo no mural para ser baixado. |
| Substituir nome do alerta | String | Vazio | Não | Especifique um novo nome de alerta a ser usado. Esse parâmetro substitui o Nome do caminho completo, se selecionado. |
| Nome do caminho completo | Caixa de seleção | Não selecionado | Não | Se selecionado, use o nome do alerta como source_product_eventtype
—por exemplo, QRadar_WinEventLog:Security_Remote fail login.
Esse parâmetro será ignorado se a opção Substituir nome do alerta estiver marcada.
|
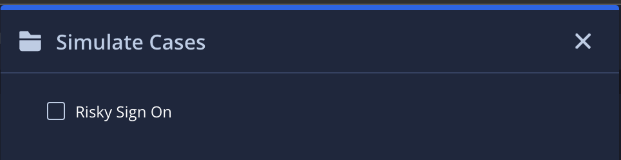
Exemplo
Neste exemplo, um caso é convertido em um caso simulado usando "Login arriscado" como nome do alerta, que será exibido como um dos casos simulados disponíveis na tela inicial.
Resultados da ação
-
Resultado do script
Nome do resultado do script Opções de valor Exemplo ScriptResult Verdadeiro/Falso Verdadeiro -
Resultado JSON
{ "cases": [ { "CreatorUserId": null, "Events": [ { "_fields": { "BaseEventIds": "[]", "ParentEventId": -1, "DeviceProduct": "WinEventLog:Security", "StartTime": "1689266169689", "EndTime": "1689266169689" }, "_rawDataFields": { "sourcetype": "Failed login", "starttime": "1689702001439", "endtime": "1689702001439" }, "Environment": null, "SourceSystemName": null, "Extensions": [] } ], "Environment": "default", "SourceSystemName": "QRadar", "TicketId": "de2e3913-e4d8-4060-ae2b-1c81ee64ba47", "Description": "This case created by SPLUNK query", "DisplayId": "de2e3913-e4d8-4060-ae2b-1c81ee64ba47", "Reason": null, "Name": "Risky Sign On", "DeviceVendor": "WIN-24TBDNRMSVB", "DeviceProduct": "WinEventLog:Security", "StartTime": 1689702001439, "EndTime": 1689702001439, "Type": 1, "Priority": -1, "RuleGenerator": "Remote Failed login", "SourceGroupingIdentifier": null, "PlaybookTriggerKeywords": [], "Extensions": [ { "Key": "KeyName", "Value": "TCS" } ], "Attachments": null, "IsTrimmed": false, "DataType": 1, "SourceType": 1, "SourceSystemUrl": null, "SourceRuleIdentifier": null, "SiemAlertId": null, "__CorrelationId": "7efd38feaea247ad9f5ea8d907e4387c" } ] }
Jobs
Fechar casos com base na pesquisa
Descrição
Esse trabalho vai fechar todos os casos com base em uma consulta de pesquisa. O payload de pesquisa é o payload usado na chamada de API "CaseSearchEverything". Para ver um exemplo desse valor, acesse "Pesquisar" na UI e abra as Ferramentas para desenvolvedores. Pesquise os casos que você quer excluir. Procure a chamada de API "CaseSearchEverything" no DevTools. Copie o payload JSON da solicitação POST e cole em "Payload de pesquisa". O motivo do fechamento precisa ser 0 ou 1. 0 = malicioso, 1 = não malicioso. A causa raiz vem de Configurações -> Dados do caso -> Causa raiz do encerramento do caso.
Parâmetros
| Parâmetro | Tipo | Valor padrão | É obrigatório | Descrição |
| Payload de pesquisa | JSON | N/A | Não | Especifique o payload JSON para pesquisar. Exemplo: {"tags":[],"ruleGenerator":[],"caseSource":[],"stage":[],"environments":[],"assignedUsers":[],"products":[],"ports":[],"categoryOutcomes":[],"status":[],"caseIds":[],"incident":[],"importance":[],"priorities":[],"pageSize":50,"isCaseClosed":false,"title":"","startTime":"2023-01-22T00:00:00.000Z","endTime":"2023-01-22T23:59:59.999Z","requestedPage":0,"timeRangeFilter":1} |
| Fechar comentário | String | N/A | Sim | Especifique um comentário de encerramento. |
| Motivo do encerramento | String | N/A | Sim | Especifique o motivo do encerramento. 0 = malicioso, 1 = não malicioso |
| Causa principal | Número inteiro | N/A | Sim | Especifique a causa raiz. A causa raiz vem de Configurações -> Dados do caso -> Causa raiz do encerramento do caso. |
| Nome de usuário do Chronicle SOAR | String | N/A | Sim | Especifique o nome de usuário do Chronicle SOAR. |
| Senha do Chronicle SOAR | Senha | N/A | Sim | Especifique a senha do Chronicle SOAR. |
Precisa de mais ajuda? Receba respostas de membros da comunidade e profissionais do Google SecOps.

