Asigna usuarios en la plataforma de Google SecOps
En este documento, se explica cómo aprovisionar, autenticar y asignar usuarios con identificación segura a la plataforma de Google Security Operations. En ella, se describe el proceso de configuración con Google Workspace como proveedor de identidad (IdP) externo, aunque los pasos son similares para otros IdP. Cuando usas el proveedor de identidad de Cloud Identity, debes configurar el servicio con grupos de correo electrónico en lugar de grupos de IdP. Para obtener más información, consulta Asigna usuarios en la plataforma de Google SecOps con Cloud Identity.
Configura atributos de SAML para el aprovisionamiento
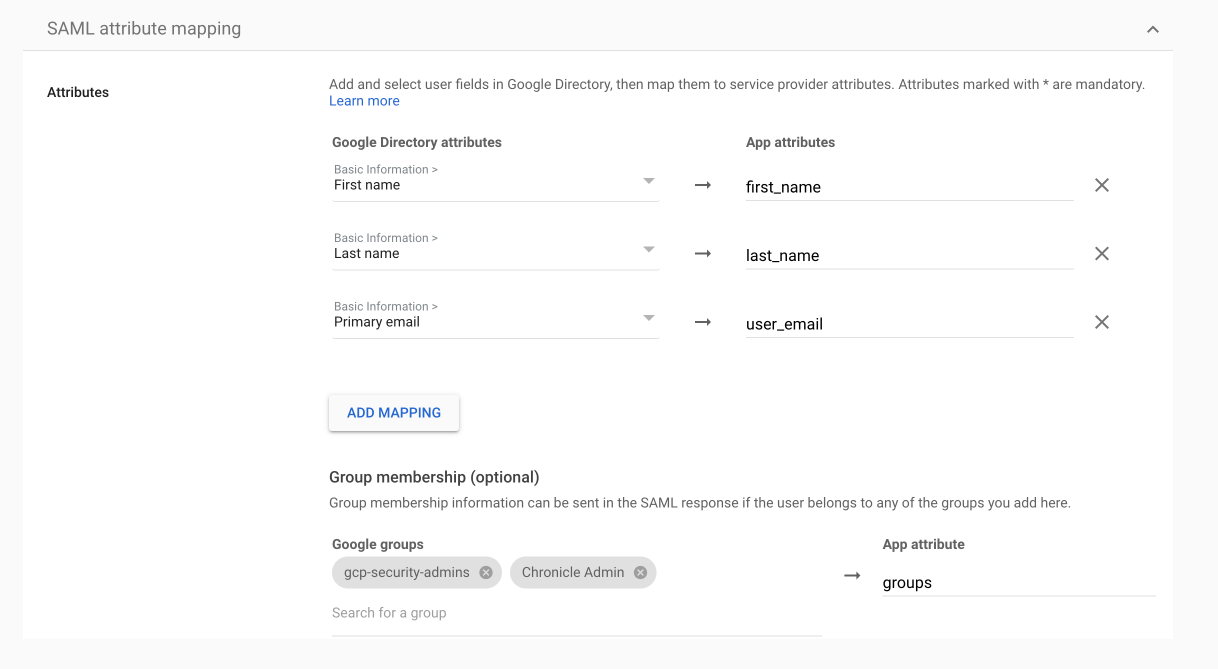
Para configurar los atributos y grupos de SAML en el IdP externo, haz lo siguiente:- En Google Workspace, ve a la sección de asignación de atributos de SAML.
- Agrega los siguientes atributos obligatorios:
first_namelast_nameuser_emailgroups- En Grupos de Google, ingresa los nombres de los grupos del IdP. Por ejemplo,
Google SecOps administratorsoGcp-security-admins. Anota estos nombres de grupos, ya que los necesitarás más adelante para la asignación en la plataforma de SecOps de Google. (En otros proveedores externos, como Okta, se conoce como IdP Groups).
Configura el aprovisionamiento del IdP
Para configurar el aprovisionamiento del IdP, sigue los pasos que se indican en Configura el IdP y Crea un proveedor de grupos de Workforce Identity.
En el siguiente ejemplo, se muestra el comando de creación de workforce pool para la configuración de la app que se describe en
Configura la federación de identidades de personal:
gcloud iam workforce-pools providers create-saml WORKFORCE_PROVIDER_ID \ --workforce-pool=WORKFORCE_POOL_ID \ --location="global" \ --display-name=WORKFORCE_PROVIDER_DISPLAY_NAME \ --description=WORKFORCE_PROVIDER_DESCRIPTION \ --idp-metadata-path=PATH_TO_METADATA_XML \ --attribute-mapping="google.subject=assertion.subject,attribute.first_name=assertion.attributes.first_name[0],attribute.last_name=assertion.attributes.last_name[0],attribute.user_email=assertion.attributes.user_email[0],google.groups=assertion.attributes.groups"
Controla el acceso de los usuarios
Existen varias formas de administrar el acceso de los usuarios a diferentes aspectos de la plataforma:
- Grupos de permisos: Establece niveles de acceso de los usuarios asignándolos a grupos de permisos específicos. Estos grupos determinan qué módulos y submódulos pueden ver o editar los usuarios. Por ejemplo, un usuario puede tener acceso a las páginas Cases y Workdesk, pero no a Playbooks ni a Settings. Para obtener más información, consulta Cómo trabajar con grupos de permisos.
- Roles de SOC: Definen el rol de un grupo de usuarios. Puedes asignar usuarios a roles del SOC para optimizar la administración de tareas. En lugar de asignar casos, acciones o guías a personas, se pueden asignar a un rol del SOC. Los usuarios pueden ver los casos que se les asignaron, su rol o roles adicionales. Para obtener más información, consulta Trabaja con roles.
- Entornos o grupos de entornos: Configura entornos o grupos de entornos para segmentar los datos en diferentes redes o unidades de negocios, que suelen utilizar las empresas y los proveedores de servicios de seguridad administrados (MSSP). Los usuarios solo pueden acceder a los datos dentro de los entornos o grupos que se les asignaron. Para obtener más información, consulta Cómo agregar un entorno nuevo.
Cómo asignar y autenticar usuarios
La combinación de grupos de permisos, roles de SOC y entornos determina el recorrido del usuario de Google SecOps para cada grupo de IdP en la plataforma de Google SecOps.
- Para los clientes que usan un proveedor externo, asigna cada grupo de IdP definido en la configuración de SAML en la página IdP Group Mapping.
- En el caso de los clientes que usan el proveedor de identidad de Cloud Identity, asigna grupos de correo electrónico en la página Group Mapping. Para obtener más información, consulta Cómo asignar usuarios en la plataforma de Google SecOps con Cloud Identity.
Puedes asignar grupos de IdP a varios grupos de permisos, roles de SOC y entornos. Esto garantiza que los diferentes usuarios asignados a diferentes grupos de IdP en el proveedor de SAML hereden todos los niveles de permisos requeridos. Para obtener más información, incluido cómo Google SecOps administra esto, consulta Varios permisos en la asignación de grupos de IdP.
También puedes optar por asignar grupos de IdP a parámetros de control de acceso individuales. Esto permite un nivel de asignación más detallado y puede ser útil para los clientes grandes. Para obtener más información, consulta Cómo asignar grupos de IdP a parámetros de control de acceso.
De forma predeterminada, la plataforma de Google SecOps incluye un grupo de IdP de administradores predeterminados.
Para asignar grupos de IdP, sigue estos pasos:
- En Google SecOps, ve a Configuración > Configuración de SOAR > Avanzada > Asignación de grupos de IdP.
- Asegúrate de tener disponibles los nombres de los grupos del IdP.
- Haz clic en Agregar Agregar y comienza a asignar los parámetros para cada grupo de IdP.
- Cuando termines, haz clic en Agregar. Cada vez que un usuario accede a la plataforma, se agrega automáticamente a la página Administración de usuarios, que se encuentra en Configuración > Organización.
Cuando los usuarios intentan acceder a la plataforma de Google SecOps, pero su grupo de IdP no se asignó, para que no se rechace a los usuarios, recomendamos habilitar la Configuración de acceso predeterminada y establecer permisos de administrador en esta página. Una vez que se complete la configuración inicial del administrador, te sugerimos que ajustes los permisos del administrador a un nivel más mínimo.
Asigna grupos de IdP a parámetros de control de acceso
En esta sección, se describe cómo asignar diferentes grupos de IdP a uno o más parámetros de control de acceso en la página IdP Group Mapping. Este enfoque es beneficioso para los clientes que desean incorporar y aprovisionar grupos de usuarios en función de personalizaciones específicas, en lugar de adherirse a la estandarización de la plataforma SOAR de Google SecOps. Si bien la asignación de grupos a parámetros puede requerir que crees más grupos inicialmente, una vez que se establece la asignación, los usuarios nuevos pueden unirse a Google SecOps sin necesidad de crear grupos adicionales.
Para obtener información sobre varios permisos en la asignación de grupos, consulta Cómo asignar usuarios con varios parámetros de control de acceso.
Borrar usuarios
Si borras grupos desde aquí, asegúrate de borrar los usuarios individuales de la pantalla Administración de usuarios. Para obtener más información, consulta Cómo borrar usuarios de SOAR de Google SecOps.Caso de uso: Asigna campos de permisos únicos a cada grupo de IdP
En el siguiente ejemplo, se ilustra cómo usar esta función para ayudar a incorporar y aprovisionar usuarios según las necesidades de tu empresa.
Tu empresa tiene tres arquetipos de clientes diferentes:
- Analistas de seguridad (contiene a los miembros del grupo Sasha y Tal)
- Ingenieros del SOC (que incluyen a los miembros del grupo Quinn y Noam)
- Ingenieros del NOC (que incluyen a los miembros del grupo Kim y Kai)
Este caso se ilustra en la siguiente tabla:
| Arquetipo | Grupo de permisos | Rol de SOC | Entorno |
|---|---|---|---|
| Analistas de seguridad | Analista | Nivel 1 | Londres |
| Ingenieros de SOC | Analista | Nivel 1 | Manchester |
| Ingenieros del NOC | Básico | Nivel 2 | Londres |
En este ejemplo, se supone que ya configuraste los grupos de permisos, los roles de SOC y los entornos necesarios en Google SecOps.
A continuación, se explica cómo configurar los grupos de IdP en el proveedor de SAML y en la plataforma de Google SecOps:
-
En tu proveedor de SAML, crea los siguientes grupos de usuarios:
- Analistas de seguridad (Sasha y Tal)
- Ingenieros del SOC (incluidos Quinn y Noam)
- Ingenieros del NOC (incluidos Kim y Kai)
- Londres (que contiene a Sasha, Tal, Kim y Kai)
- Manchester (que contiene a Quinn y Noam)
- Ve a Configuración > Configuración de SOAR > Avanzada > Asignación de grupos de IdP.
- Haz clic en Add IdP Group.
- Ingresa los siguientes detalles en el diálogo:
- Grupo de IdP:
Security analysts - Grupo de permisos:
Analyst - Rol de SOC:
Tier 1 - Entorno: dejar en blanco
- Ingresa los siguientes detalles en el siguiente diálogo:
- Grupo de IdP:
SOC engineers - Grupo de permisos:
Analyst - Rol de SOC:
Tier 1 - Entorno: dejar en blanco
- Ingresa los siguientes detalles en el siguiente diálogo:
- Grupo de IdP:
NOC engineers - Grupo de permisos:
Basic - Rol de SOC:
Tier 2 - Entorno: dejar en blanco
- Ingresa los siguientes detalles en el siguiente diálogo:
- Grupo de IdP:
London - Grupo de permisos: deja en blanco
- Rol de SOC: dejar en blanco
- Entorno:
London - Ingresa los siguientes detalles en el siguiente diálogo:
- Grupo de IdP:
Manchester - Grupo de permisos: deja en blanco
- Rol de SOC: dejar en blanco
- Entorno:
Manchester
Para los clientes que usan la función de federación de casos, consulta Cómo configurar el acceso federado a los casos para Google SecOps.
¿Necesitas más ayuda? Obtén respuestas de miembros de la comunidad y profesionales de Google SecOps.

