使用 Google Security Operations 查看潜在安全问题
本文档介绍了如何使用 Google Security Operations 调查提醒和潜在安全问题。
准备工作
Google Security Operations 专门用于 Google Chrome 或 Mozilla Firefox 浏览器。
Google 建议您将浏览器升级到最新版本。您可以访问 https://www.google.com/chrome/ 下载最新版 Chrome。
Google SecOps 已集成到您的单点登录解决方案 (SSO) 中。您可以使用企业提供的凭据登录 Google SecOps。
启动 Chrome 或 Firefox。
确保您有权访问公司账号。
如需访问 Google SecOps 应用,其中 customer_subdomain 是客户特定的标识符,请前往:https://customer_subdomain.backstory.chronicle.security。
查看提醒和 IOC 匹配项
在导航栏中,选择检测 > 提醒和 IOC。
点击 IOC 匹配项标签页。
在网域视图中搜索 IOC 匹配项
IOC 网域匹配项标签页中的网域列包含可疑网域列表。点击此列中的某个网域会打开网域视图,如下图所示,提供有关该网域的详细信息。
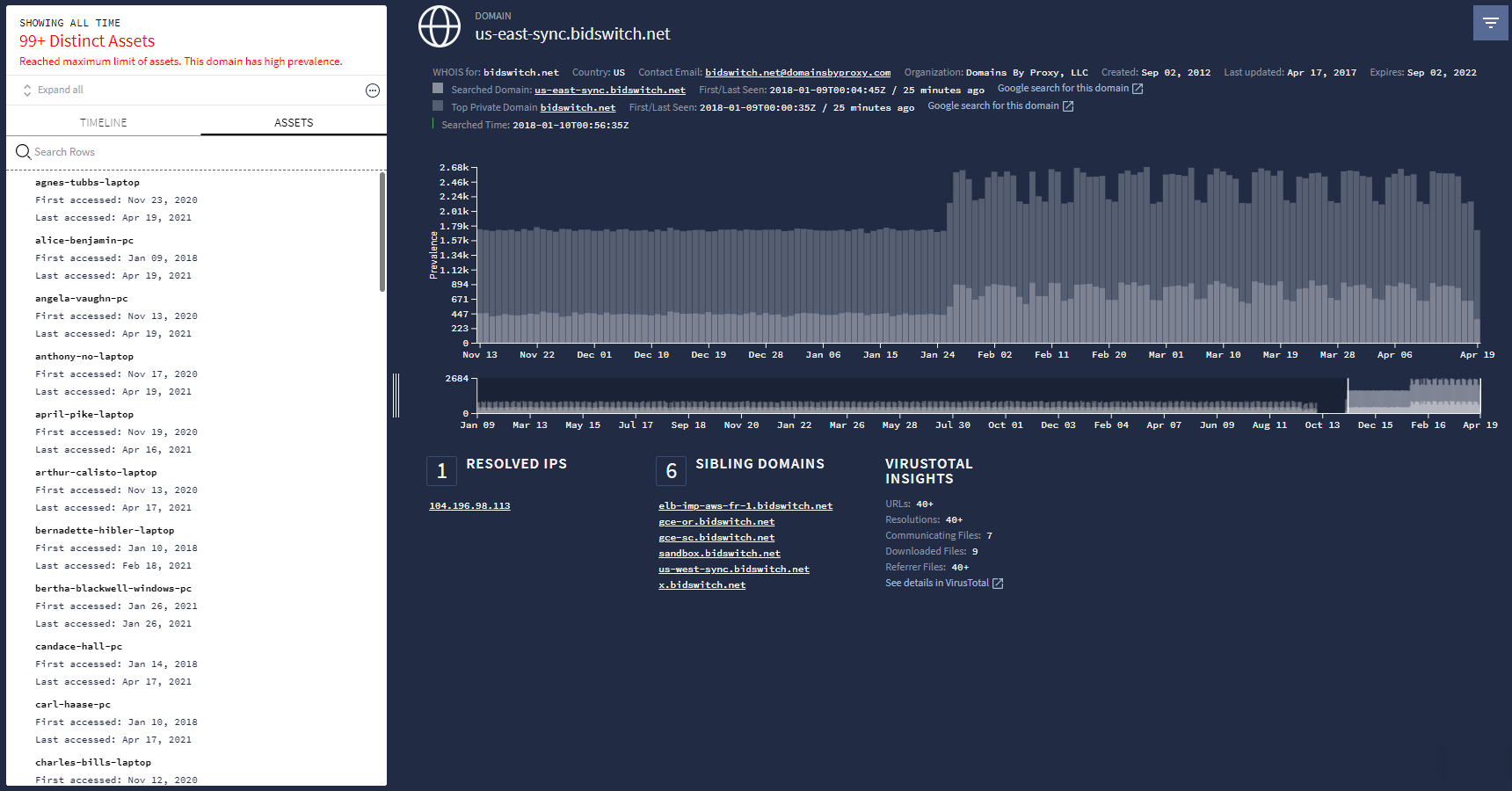 网域视图
网域视图
使用 Google Security Operations 搜索字段
直接从 Google Security Operations 首页启动搜索,如下图所示。
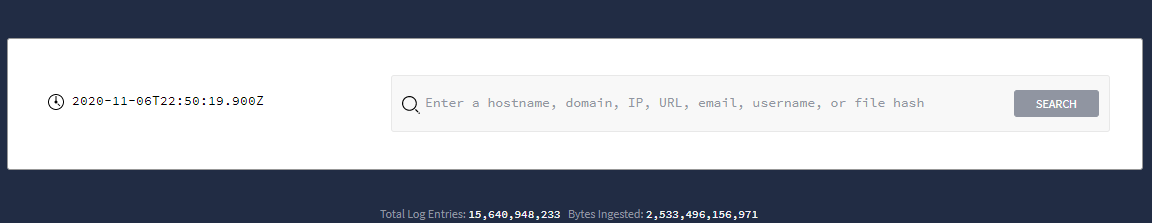 Google Security Operations 搜索字段
Google Security Operations 搜索字段
在此页面上,您可以输入以下搜索字词:
|
(例如 Plato.example.com) |
|
(例如:altostrat.com) |
|
(例如:192.168.254.15) |
|
(例如:https://new.altostrat.com) |
|
(例如:betty-dearo-pc) |
|
(例如:e0d123e5f316bef78bfdf5a888837577) |
您不必指定要输入的搜索字词的类型,Google Security Operations 会为您确定。相应结果会显示在相应的调查视图中。例如,在搜索字段中输入用户名会显示资产视图。
搜索原始日志
您可以选择搜索已编入索引的数据库或搜索原始日志。搜索原始日志是一种更全面的搜索,但它比编入索引的搜索花费的时间更长。
如需进一步确定搜索,您可以使用正则表达式,使搜索条目区分大小写,或选择日志源。您还可以使用开始和结束时间字段选择所需的时间轴。
如需执行原始日志搜索,请完成以下步骤:
输入搜索字词,然后在下拉菜单中选择原始日志扫描,如下图所示。
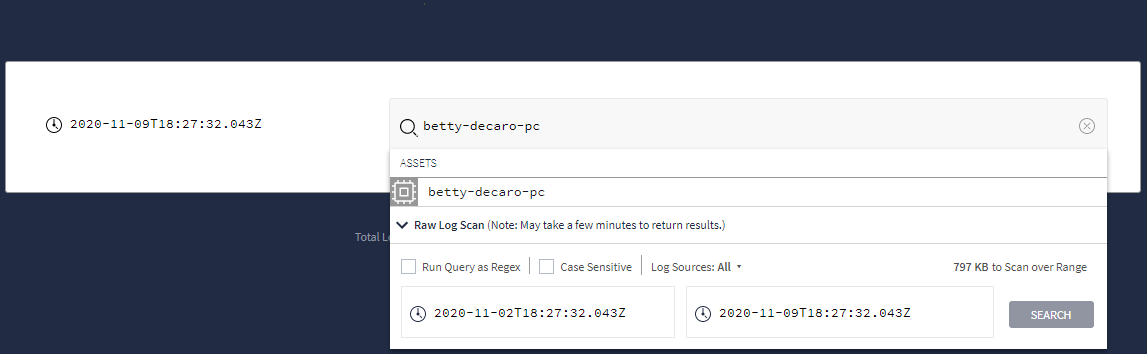 显示原始日志扫描选项的下拉菜单
显示原始日志扫描选项的下拉菜单设置原始搜索条件后,点击搜索按钮。
在原始日志扫描视图中,您可以进一步分析日志数据。

