Meninjau potensi masalah keamanan dengan Google Security Operations
Dokumen ini menjelaskan cara melakukan penelusuran saat menyelidiki pemberitahuan dan kemungkinan masalah keamanan menggunakan Google Security Operations.
Sebelum memulai
Google Security Operations dirancang untuk berfungsi secara eksklusif dengan browser Google Chrome atau Mozilla Firefox.
Google merekomendasikan agar Anda mengupgrade browser ke versi terbaru. Anda dapat mendownload Chrome versi terbaru dari https://www.google.com/chrome/.
Google SecOps terintegrasi ke dalam solusi single sign-on (SSO) Anda. Anda dapat login ke Google SecOps menggunakan kredensial yang disediakan oleh perusahaan Anda.
Luncurkan Chrome atau Firefox.
Pastikan Anda memiliki akses ke akun perusahaan Anda.
Untuk mengakses aplikasi Google SecOps, dengan customer_subdomain adalah ID khusus pelanggan Anda, buka: https://customer_subdomain.backstory.chronicle.security.
Melihat Pemberitahuan dan Kecocokan IOC
Di panel navigasi, pilih Detections > Alerts and IOCs.
Klik tab IOC Matches.
Menelusuri kecocokan IOC dalam tampilan Domain
Kolom Domain di tab IOC Domain Matches berisi daftar domain yang dicurigai. Mengklik domain di kolom ini akan membuka tampilan Domain, seperti yang ditunjukkan pada gambar berikut, yang memberikan informasi mendetail tentang domain ini.
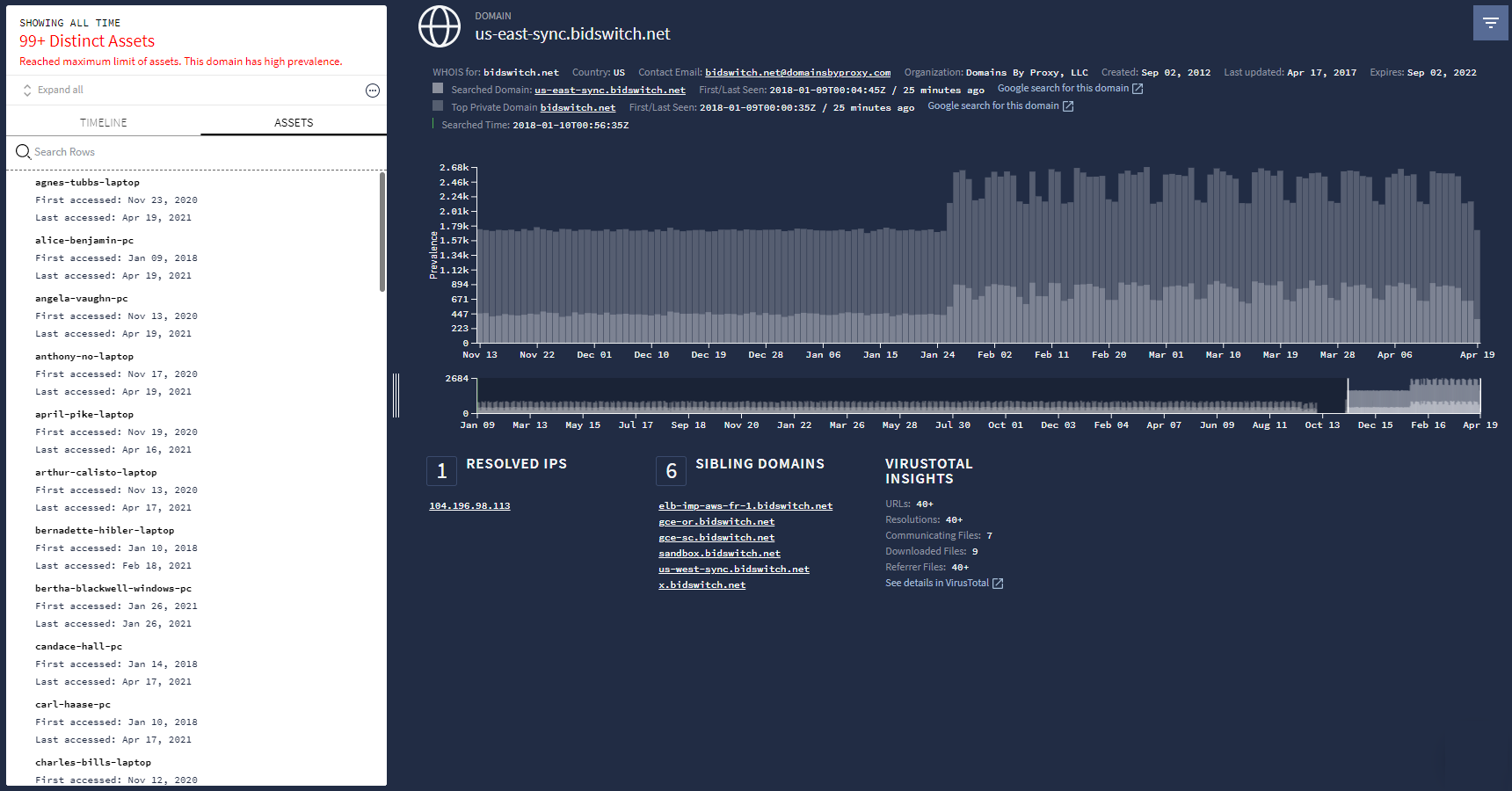 Tampilan Domain
Tampilan Domain
Menggunakan kolom Penelusuran Google Security Operations
Mulai penelusuran langsung dari halaman beranda Google Security Operations, seperti yang ditunjukkan pada gambar berikut.
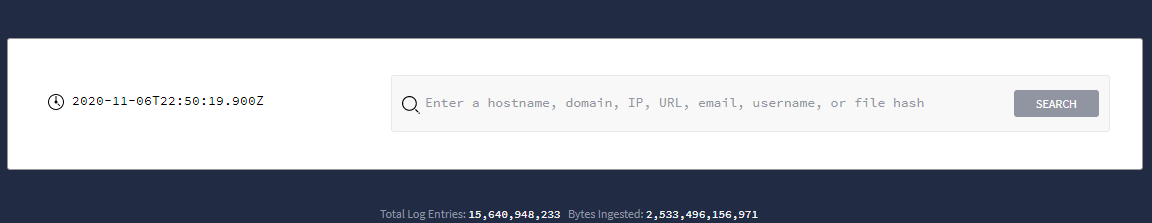 Kolom Penelusuran Google Security Operations
Kolom Penelusuran Google Security Operations
Di halaman ini, Anda dapat memasukkan istilah penelusuran berikut:
|
(misalnya, plato.example.com) |
|
(misalnya, altostrat.com) |
|
(misalnya, 192.168.254.15) |
|
(misalnya, https://new.altostrat.com) |
|
(misalnya, betty-decaro-pc) |
|
(misalnya, e0d123e5f316bef78bfdf5a888837577) |
Anda tidak perlu menentukan jenis istilah penelusuran yang Anda masukkan, Google Security Operations akan menentukannya untuk Anda. Hasilnya ditampilkan dalam tampilan investigasi yang sesuai. Misalnya, mengetik nama pengguna di kolom penelusuran akan menampilkan tampilan Aset.
Menelusuri log mentah
Anda memiliki opsi untuk menelusuri database yang diindeks atau menelusuri log mentah. Menelusuri log mentah adalah penelusuran yang lebih komprehensif, tetapi membutuhkan waktu lebih lama daripada penelusuran yang diindeks.
Untuk lebih mempersempit penelusuran, Anda dapat menggunakan ekspresi reguler, membuat entri penelusuran peka huruf besar/kecil, atau memilih sumber log. Anda juga dapat memilih linimasa yang diinginkan menggunakan kolom waktu Mulai dan Akhir.
Untuk melakukan penelusuran log mentah, selesaikan langkah-langkah berikut:
Ketik istilah penelusuran Anda, lalu pilih Raw Log Scan di menu dropdown, seperti yang ditunjukkan pada gambar berikut.
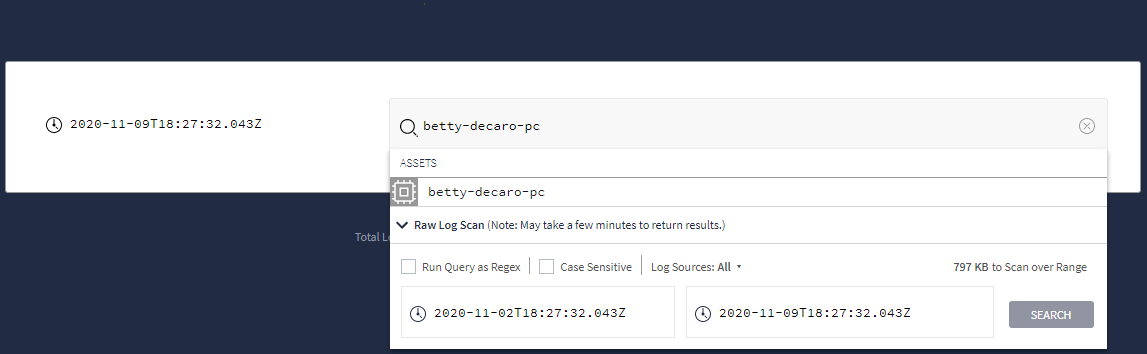 Menu dropdown yang menampilkan opsi Raw Log Scan
Menu dropdown yang menampilkan opsi Raw Log ScanSetelah menetapkan kriteria penelusuran mentah, klik tombol Telusuri.
Dari tampilan Pemindaian Log Mentah, Anda dapat menganalisis data log lebih lanjut.

