Menjalankan aturan terhadap data historis
Saat Anda membuat dan mengaktifkan aturan baru, aturan tersebut akan mulai menelusuri deteksi berdasarkan peristiwa yang diterima oleh akun Google Security Operations Anda secara real time. Retrohunt memungkinkan Anda menggunakan aturan yang dipilih untuk menelusuri deteksi di seluruh data yang ada di Google SecOps. Retrohunt dijadwalkan saat ada resource yang tersedia untuk dijalankan. Perkirakan varians dalam waktu proses retrohunt.
Untuk memulai retrohunt, selesaikan langkah-langkah berikut:
Buka Dasbor Aturan.
Klik ikon opsi Aturan untuk suatu aturan, lalu pilih Yara-L Retrohunt.
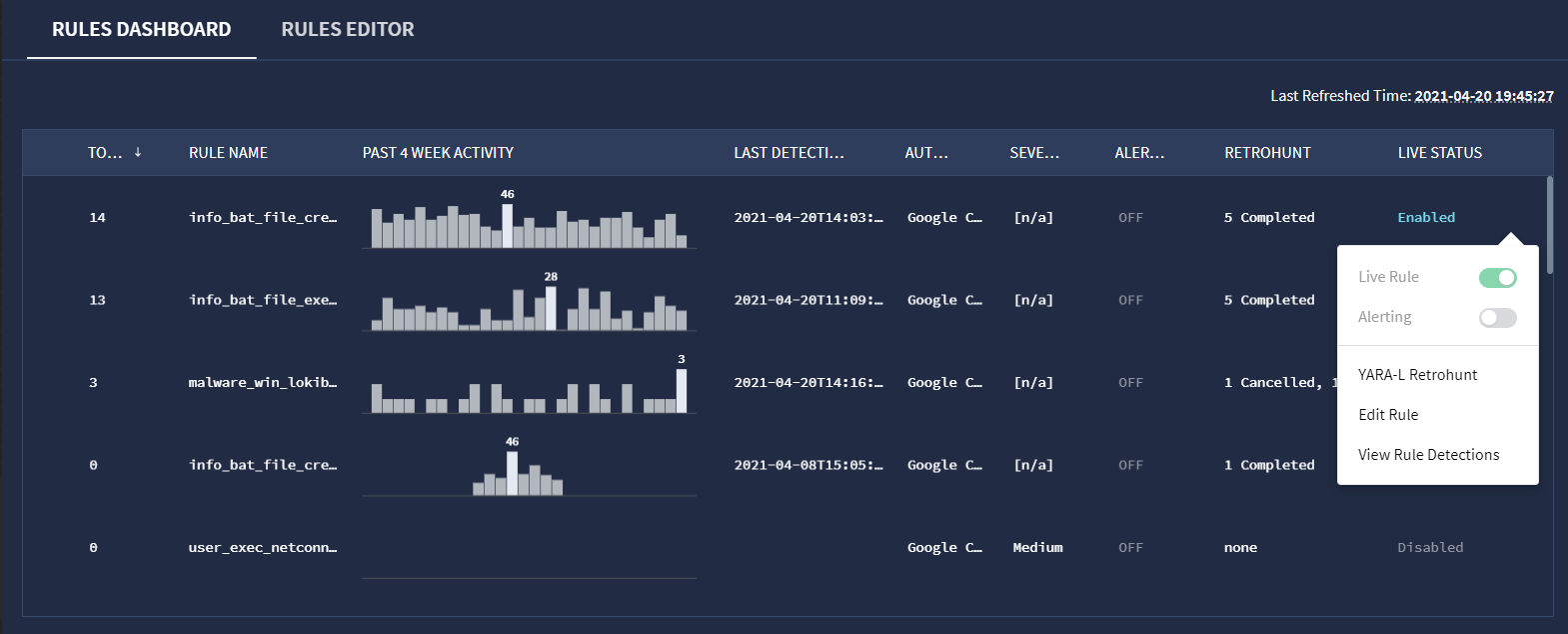 Opsi Retrohunt YARA-L
Opsi Retrohunt YARA-LDi jendela YARA-L Retrohunt, pilih waktu mulai dan akhir untuk penelusuran Anda. Defaultnya adalah satu minggu. Jendela ini menampilkan rentang tanggal dan waktu yang tersedia. Untuk aturan multi-peristiwa, rentang penelusuran retrohunt harus lebih besar dari atau sama dengan ukuran periode kecocokan.
Klik RUN.
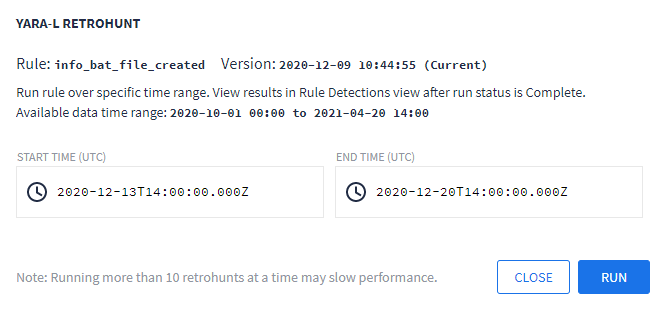
Jendela dialog Retrohunt Yara-L
Anda dapat melihat progres retrohunt yang dijalankan dari tampilan deteksi aturan untuk aturan tersebut. Jika membatalkan retrohunt yang sedang berlangsung, Anda tetap dapat melihat deteksi yang berhasil dilakukan saat dijalankan.
Jika Anda telah menyelesaikan beberapa retrohunt, Anda dapat melihat hasil retrohunt sebelumnya dengan mengklik link rentang tanggal seperti yang ditunjukkan pada gambar berikut. Hasil setiap proses ditampilkan dalam grafik Linimasa dan Deteksi di tampilan Deteksi Aturan.
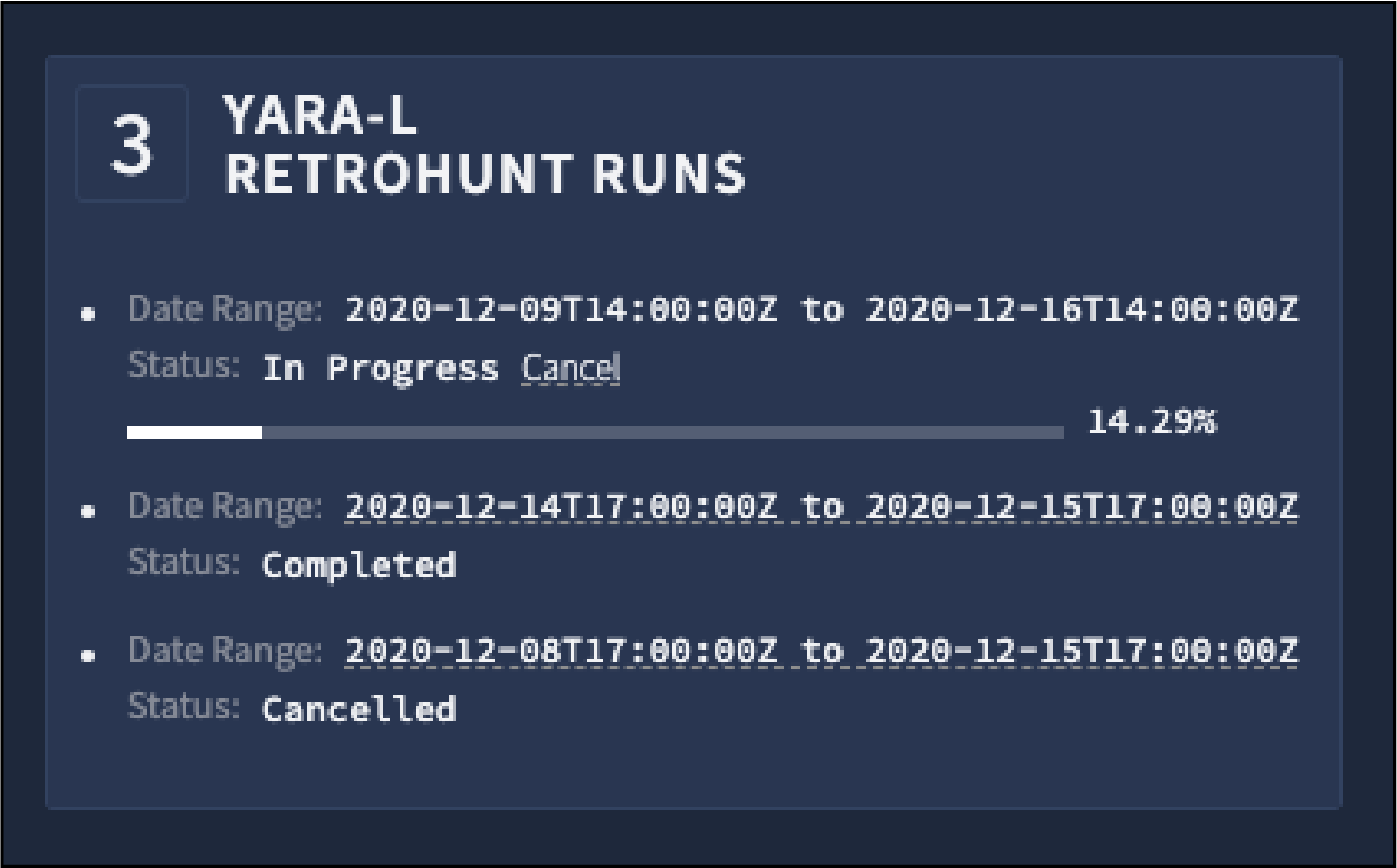
Retrohunt Yara-L berjalan
Jika Anda menggunakan daftar referensi dalam aturan, jalankan retrohunt, lalu hapus item dari daftar tersebut, Anda harus merevisi aturan tersebut ke versi baru untuk melihat hasil baru. Google SecOps tidak menghapus deteksi dari daftar referensi, sehingga memperbarui aturan tidak akan memperbarui hasilnya.
Perlu bantuan lain? Dapatkan jawaban dari anggota Komunitas dan profesional Google SecOps.

