调查 IP 地址
借助 Google Security Operations,您可以调查特定的 IP 地址,以确定您的企业是否存在任何 IP 地址,以及这些外部系统可能对您的资产产生的影响。Google SecOps IP 地址视图派生自企业转发的同一安全信息和数据,并且可以使用“资产”视图进行检查。确保从网络上的设备(例如 EDR、防火墙、Web 代理等)提取和规范化数据。
从“资产”视图开始,您可以从企业内部开始调查并展开调查。从 IP 地址视图中,您可以从企业外部开始调查,然后查看。
如需访问 Google SecOps 中的 IP 地址视图,请完成以下步骤:
- 在 Google SecOps 着陆页上,于搜索栏中输入 IP 地址。点击搜索。
- 点击结果中的 IP 地址,打开 IP 地址视图。
IP 地址上下文
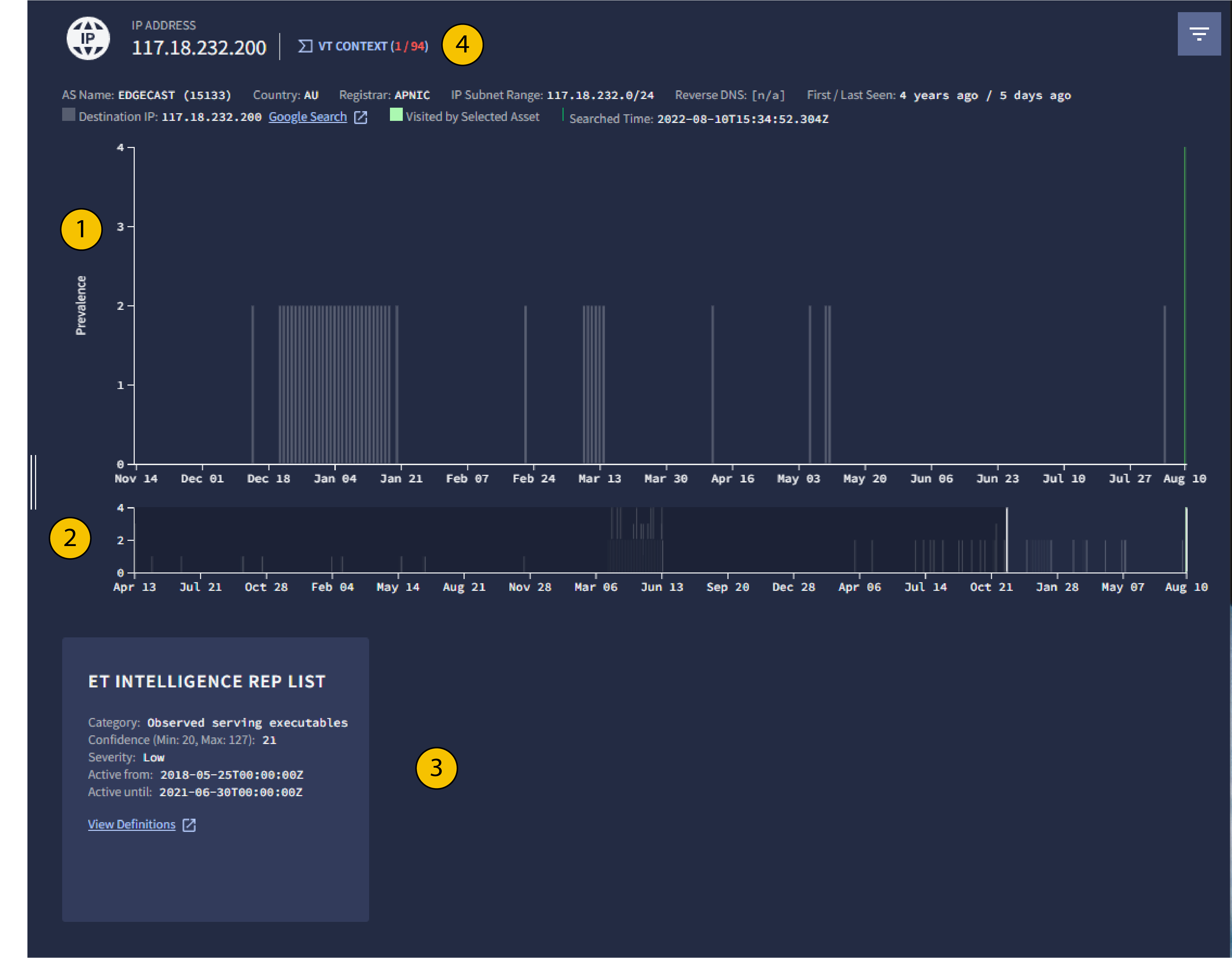 “IP 地址”视图
“IP 地址”视图
1 普及率
Google SecOps 以图形形式呈现了给定 IP 地址的历史普及率。此图表可用于确定之前是否从企业内部访问过该 IP 地址,并指示该 IP 地址是否与针对企业的特定广告系列相关联。
通常,不太常见的 IP 地址(即已关联较少的 IP 地址)可能对您的企业构成更大的威胁。与“资产”视图中的普及率图表不同,此图在图表顶部显示高普及率,在底部显示低普及率。
当您将指针悬停在普及率图表中的某个条形上时,该图表会列出访问过相应 IP 地址的资产。由于 DNS 服务器非常普遍,因此未列出。如果所有资产都是 DNS 服务器,则不会列出任何资产。
2 普及率图表的滑块
调整滑块,以重点关注与特定日期范围相关的事件,如普及率图所示。
3 IP 地址数据洞察
IP 地址分析结果为您提供了更多有关所调查 IP 地址的背景信息。您可以使用它们来确定 IP 地址是良性还是恶意。还可以让您进一步调查指示因素,以确定是否存在更大的危害。
ET 情报代表名单:根据 ProofPoint 的新兴威胁 (ET) 情报代表名单进行检查。列出与特定 IP 地址和网域相关的已知威胁。
ESET 威胁情报:根据 ESET 的威胁情报服务进行检查。
4 VT 情境
点击 VT Context 可查看此 IP 地址的 VirusTotal 信息。
注意事项
IP 地址视图具有以下限制:
- 您只能过滤此视图中显示的事件。
- 此视图中仅填充了 DNS、EDR、Webproxy 事件类型。此视图中填充的首次看到和上次看到信息也仅限于这些事件类型。
- 通用事件不会显示在任何精选视图中。它们仅会出现在原始日志和 UDM 搜索中。
需要更多帮助?从社区成员和 Google SecOps 专业人士那里获得解答。

