Review potential security issues with Google Security Operations
This document describes how to conduct searches when investigating alerts and potential security issues using Google Security Operations.
Before you begin
Google Security Operations is designed to work exclusively with the Google Chrome or Mozilla Firefox browsers.
Google recommends upgrading your browser to the most current version. You can download the latest version of Chrome from https://www.google.com/chrome/.
Google SecOps is integrated into your single sign-on solution (SSO). You can log in to Google SecOps using the credentials provided by your enterprise.
Launch Chrome or Firefox.
Ensure you have access to your corporate account.
To access the Google SecOps application, where customer_subdomain is your customer-specific identifier, navigate to: https://customer_subdomain.backstory.chronicle.security.
Viewing Alerts and IOC Matches
In the navigation bar, select Detections > Alerts and IOCs.
Click the IOC Matches tab.
Searching for IOC matches in Domain view
The Domain column in the IOC Domain Matches tab contains a list of suspect domains. Clicking on a domain in this column opens Domain view, as shown in the following figure, providing detailed information about this domain.
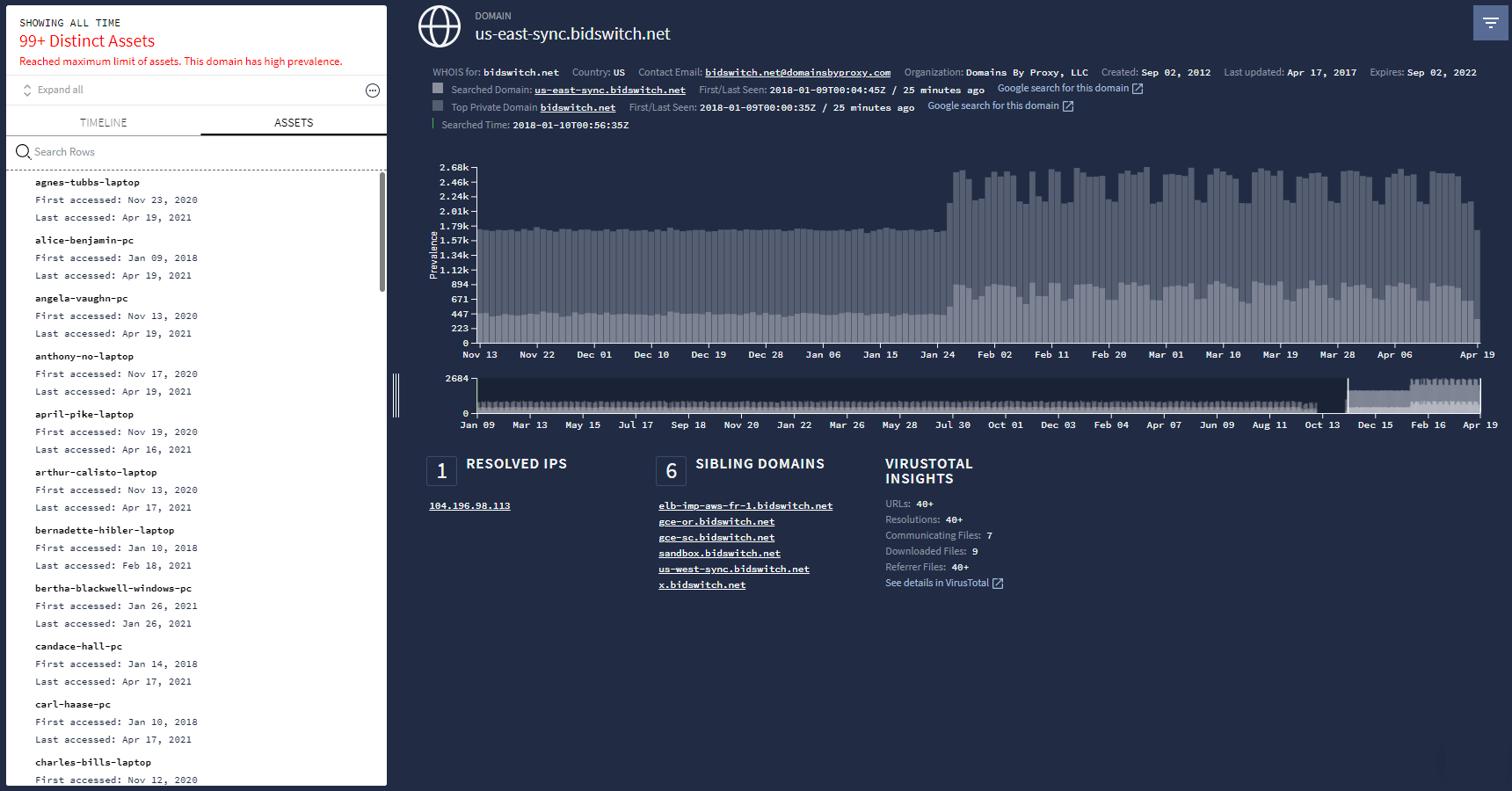 Domain view
Domain view
Using the Google Security Operations Search field
Initiate a search directly from the Google Security Operations home page, as shown in the following figure.
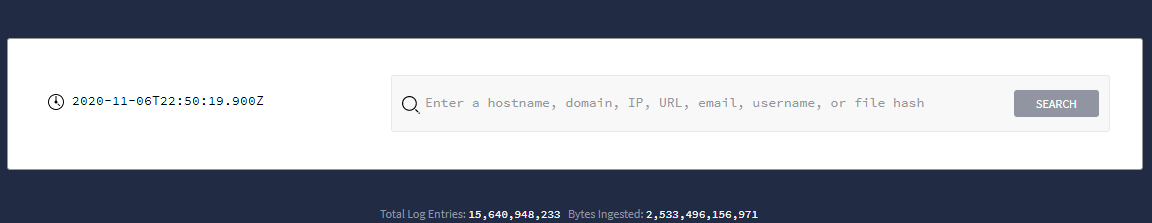 Google Security Operations Search field
Google Security Operations Search field
On this page, you can enter the following search terms:
|
(for example, plato.example.com) |
|
(for example, altostrat.com) |
|
(for example, 192.168.254.15) |
|
(for example, https://new.altostrat.com) |
|
(for example, betty-decaro-pc) |
|
(for example, e0d123e5f316bef78bfdf5a888837577) |
You do not have to specify which type of search term you are entering, Google Security Operations determines it for you. The results are shown in the appropriate investigative view. For example, typing a username in the search field displays Asset view.
Searching raw logs
You have the option of searching the indexed database or searching raw logs. Searching raw logs is a more comprehensive search, but takes longer than an indexed search.
To further pinpoint your search, you can use regular expressions, make the search entry case sensitive, or select log sources. You can also select the timeline you want using the Start and End time fields.
To conduct a raw log search, complete the following steps:
Type in your search term, and then select Raw Log Scan in the dropdown menu, as shown in the following figure.
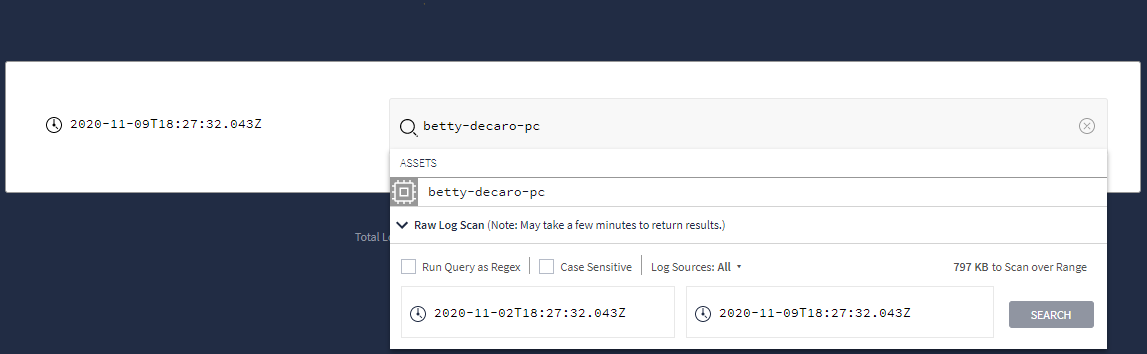 Dropdown menu showing Raw Log Scan option
Dropdown menu showing Raw Log Scan optionAfter setting your raw search criteria, click the Search button.
From Raw Log Scan view, you can further analyze your log data.
