Akun layanan adalah jenis akun khusus di Google Cloud yang memungkinkan komponen dan aplikasi sistem berinteraksi satu sama lain dan dengan API lainnya. Untuk mengetahui informasi selengkapnya tentang Google Cloud, lihat Tentang layanan Google Cloud.
Apigee hybrid menggunakan akun layanan Google Cloud untuk melakukan berbagai tugas, termasuk:
- Mengirim data log dan metrik
- Menarik permintaan rekaman aktivitas
- Menghubungkan ke API gateway untuk permintaan API administratif
- Menjalankan pencadangan
- Mendownload paket proxy
Meskipun satu akun layanan dapat melakukan semua operasi ini, untuk lingkungan produksi, Apigee merekomendasikan agar Anda membuat beberapa akun layanan, yang masing-masing ditetapkan ke tugas tertentu dan masing-masing memiliki kumpulan izinnya sendiri. Hal ini meningkatkan keamanan dengan memisahkan akses dan membatasi cakupan serta hak istimewa akses setiap akun layanan. Seperti halnya akun pengguna, izin ini diterapkan dengan menetapkan satu atau beberapa peran ke akun layanan.
Akun layanan dan peran yang digunakan oleh komponen campuran
Agar dapat beroperasi dengan benar, Apigee hybrid mengharuskan Anda membuat beberapa akun layanan. Setiap akun layanan memerlukan peran atau peran tertentu yang memungkinkannya menjalankan fungsinya.
Tabel berikut menjelaskan akun layanan untuk komponen campuran. Nama yang diberikan untuk setiap akun layanan adalah nama default. Anda dapat menggunakan nama apa pun yang diinginkan, tetapi nama tersebut harus mudah diidentifikasi dengan tujuan setiap akun.
| Komponen* | Peran | Diperlukan untuk penginstalan dasar? | Deskripsi |
|---|---|---|---|
apigee-cassandra |
Storage Object Adminroles/storage.objectAdmin |
Mengizinkan pencadangan Cassandra ke Cloud Storage, seperti yang dijelaskan dalam Pencadangan dan pemulihan. | |
apigee-logger |
Logs Writerroles/logging.logWriter |
Mengizinkan pengumpulan data logging, seperti yang dijelaskan dalam Logging. Hanya diperlukan untuk penginstalan cluster non-GKE. | |
apigee-mart |
Apigee Connect Agentroles/apigeeconnect.Agent |
Mengizinkan autentikasi layanan MART. Peran Agen Apigee Connect memungkinkannya berkomunikasi dengan aman dengan proses Apigee Connect, seperti yang dijelaskan dalam Menggunakan Apigee Connect. | |
apigee-metrics |
Monitoring Metric Writerroles/monitoring.metricWriter |
Mengizinkan pengumpulan data metrik, seperti yang dijelaskan dalam Ringkasan pengumpulan metrik. | |
apigee-runtime |
Tidak ada peran yang diperlukan | Memungkinkan runtime campuran Apigee terhubung ke layanan Google dan layanan kustom di Google Cloud, seperti Autentikasi Google, Google Cloud Trace, dan Jaeger. | |
apigee-synchronizer |
Pengelola Synchronizer Apigeeroles/apigee.synchronizerManager |
Memungkinkan sinkronisasi mendownload paket proxy dan data konfigurasi lingkungan. Juga memungkinkan pengoperasian fitur rekaman aktivitas. | |
apigee-udca |
Agen Apigee Analyticsroles/apigee.analyticsAgent |
Memungkinkan transfer data status deployment, analisis, dan rekaman aktivitas ke platform manajemen. | |
apigee-watcher |
Apigee Runtime Agentroles/apigee.runtimeAgent |
Apigee Watcher mengambil perubahan terkait host virtual untuk organisasi dari sinkronisasi dan membuat perubahan yang diperlukan untuk mengonfigurasi ingress istio. | |
| * Nama ini digunakan dalam nama file kunci akun layanan yang didownload. | |||
Sebagai alternatif, untuk lingkungan non-produksi, pengujian, dan demo, Anda dapat menggunakan satu akun layanan dengan semua peran yang ditetapkan. Tindakan ini tidak direkomendasikan untuk lingkungan produksi.
| Komponen* | Peran | Diperlukan untuk penginstalan dasar? | Deskripsi |
|---|---|---|---|
apigee-non-prod |
Apigee Analytics Agent, Apigee Connect Agent, Apigee Organization Admin, Apigee Runtime Agent, Apigee Synchronizer Manager, Cloud Trace Agent, Logs Writer, Monitoring Metric Writer, Storage Object Admin | Atau semua SA yang diperlukan di atas | Satu akun layanan untuk lingkungan demo atau pengujian. Lihat Penginstalan, Bagian 2, Langkah 5: Membuat akun layanan. |
Selain membuat akun layanan yang tercantum dalam tabel ini, Anda akan menggunakan setiap kunci pribadi akun untuk membuat token akses sehingga Anda dapat mengakses Apigee API. Alat
create-service-account akan otomatis mendownload file kunci ke direktori
di komputer lokal Anda saat membuat atau memperbarui akun layanan.
Membuat akun layanan
Ada beberapa cara untuk membuat akun layanan, termasuk:
- (Direkomendasikan) Alat
create-service-account - Konsol Google Cloud
- gcloud SDK
Masing-masing dijelaskan di bagian berikut.
Menggunakan alat create-service-account
Alat create-service-account tersedia setelah Anda
mendownload dan memperluas apigeectl di
direktori tools/. Layanan ini membuat akun layanan khusus komponen campuran dan menetapkan
peran yang diperlukan untuk Anda. Alat ini juga otomatis mendownload kunci akun layanan dan
menyimpannya di komputer lokal Anda.
Misalnya, perintah berikut akan membuat semua akun layanan terpisah untuk
lingkungan produksi, menetapkan peran IAM yang sesuai ke setiap akun layanan, dan mendownload
setiap file kunci pribadi akun ke direktori ./service-accounts:
./tools/create-service-account --env prod
Perintah berikut membuat satu akun layanan bernama apigee-non-prod dengan semua peran IAM untuk semua komponen campuran, yang cocok untuk lingkungan demo dan pengujian, tetapi tidak untuk lingkungan produksi:
./tools/create-service-account --env non-prod
Untuk informasi selengkapnya tentang penggunaan create-service-account, lihat
referensi create-service-account.
Menggunakan konsol Google Cloud
Anda dapat membuat akun layanan dengan konsol Google Cloud.
Untuk membuat akun layanan dengan konsol Google Cloud dan membuat kunci untuk akun layanan, lakukan tindakan berikut:
-
Buat akun layanan:
-
Di konsol Cloud, buka halaman Service Accounts.
- Pilih project Anda.
- Klik Buat akun layanan.
-
Di kolom Nama akun layanan, masukkan nama. Konsol Cloud akan mengisi kolom ID akun layanan berdasarkan nama ini.
Apigee merekomendasikan agar Anda menggunakan nama yang mencerminkan peran akun layanan; Anda dapat menetapkan nama akun layanan agar sama dengan nama komponen yang menggunakannya. Misalnya, tetapkan nama akun layanan Logs Writer
apigee-logger.Untuk mengetahui informasi selengkapnya tentang nama dan peran akun layanan, lihat Akun layanan dan peran yang digunakan oleh komponen campuran.
- Opsional: Di kolom Deskripsi akun layanan, masukkan deskripsi untuk akun layanan. Deskripsi membantu mengingatkan Anda tentang tujuan penggunaan akun layanan tertentu.
- Klik Buat dan lanjutkan.
-
Klik kolom Select a role dan pilih peran, seperti yang dijelaskan dalam Akun layanan dan peran yang digunakan oleh komponen campuran. Jika peran Apigee tidak muncul dalam daftar drop-down, muat ulang halaman.
Misalnya, untuk komponen logging, pilih peran Penulis Log.
Jika perlu, masukkan teks untuk memfilter daftar peran menurut nama. Misalnya, untuk hanya mencantumkan peran Apigee, masukkan
Apigeedi kolom filter.Anda dapat menambahkan lebih dari satu peran ke akun layanan, tetapi Apigee merekomendasikan agar Anda hanya menggunakan satu peran untuk setiap akun layanan yang direkomendasikan. Untuk mengubah peran akun layanan setelah Anda membuatnya, gunakan halaman IAM di konsol Cloud.
- Klik Lanjutkan.
Google Cloud akan menampilkan tampilan Beri pengguna akses ke akun layanan ini:
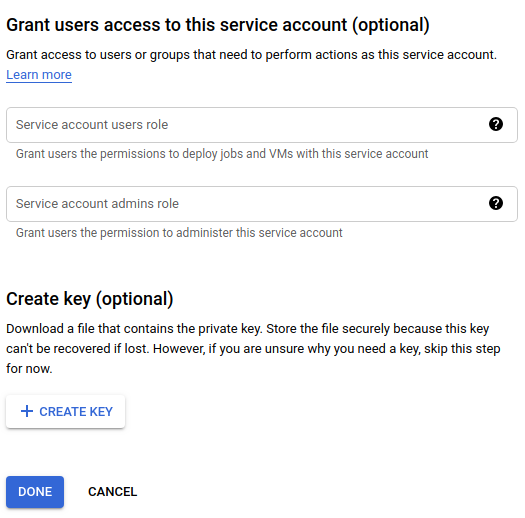
- Di bagian Buat kunci (opsional), klik Buat Kunci.
Google Cloud memberi Anda opsi untuk mendownload kunci JSON atau P12:
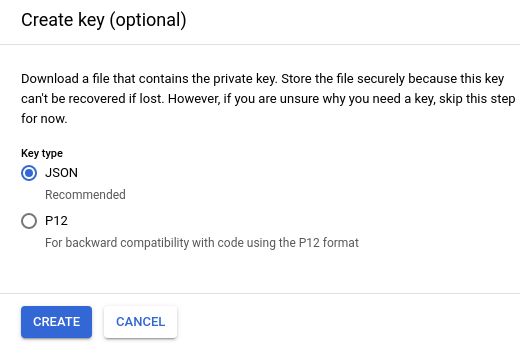
- Pilih JSON (default) dan klik Create.
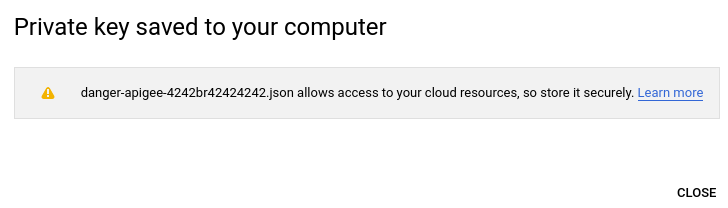
Google Cloud menyimpan file kunci dalam format JSON ke komputer lokal Anda dan menampilkan konfirmasi saat berhasil, seperti yang ditunjukkan contoh berikut:
Anda nantinya akan menggunakan beberapa kunci akun layanan untuk mengonfigurasi layanan runtime campuran. Misalnya, saat mengonfigurasi runtime hybrid, Anda akan menentukan lokasi kunci akun layanan menggunakan properti SERVICE_NAME
.serviceAccountPath.Kunci ini digunakan oleh akun layanan untuk mendapatkan token akses, yang kemudian digunakan akun layanan untuk membuat permintaan terhadap Apigee API atas nama Anda. (Namun, hal ini belum akan terjadi dalam waktu dekat. Untuk saat ini, cukup ingat tempat Anda menyimpannya.)
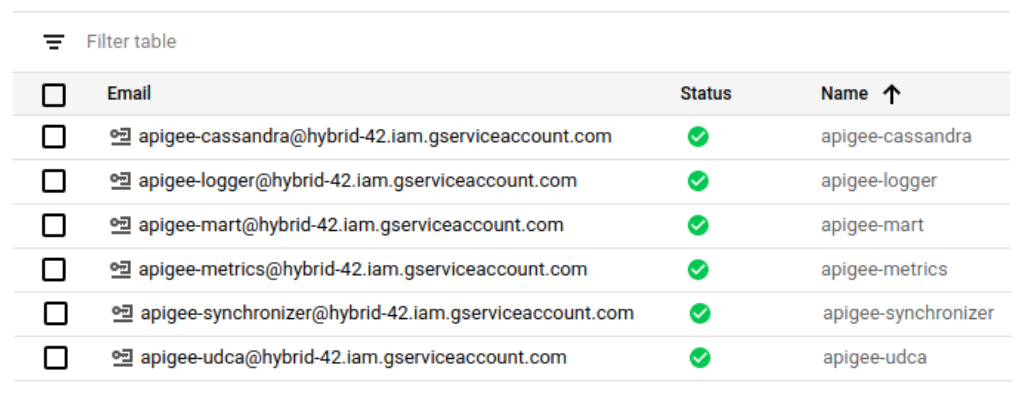
- Ulangi langkah 4 hingga 11 untuk setiap akun layanan yang tercantum dalam
Akun layanan dan peran yang digunakan oleh komponen campuran
(kecuali akun
apigee-mart—yang tidak memiliki peran yang terkait dengannya—jadi jangan tetapkan peran).Setelah selesai, Anda akan memiliki akun layanan berikut (selain akun default, jika ada):
Di konsol Google Cloud, akun layanan ditunjukkan dengan ikon
 .
.
Setelah membuat akun layanan, jika ingin menambahkan atau menghapus peran ke akun tersebut, Anda harus menggunakan tampilan IAM & Admin. Anda tidak dapat mengelola peran untuk akun layanan di tampilan Akun layanan.
Menggunakan API pembuatan akun layanan gcloud
Anda dapat membuat dan mengelola akun layanan dengan Cloud Identity and Access Management API.
Untuk informasi selengkapnya, lihat Membuat dan mengelola akun layanan.
Pemecahan masalah
-

