This page applies to Apigee, but not to Apigee hybrid.
View
Apigee Edge documentation.
![]()
This document describes the use of Private Service Connect (PSC) to configure routing from clients to Apigee, also called "northbound" traffic.
Overview
You can use PSC to connect the Apigee VPC with the VPC that you have peered with Apigee, or with any other VPC that you control. This architectural pattern eliminates the need to create managed instance groups (MIGs) to forward requests from the global load balancer to Apigee. With the PSC routing method, API proxy requests pass through a global external HTTP(S) load balancer that you install in a VPC to a single point of attachment in the Apigee VPC, called a Service Attachment. This configuration lets you send Apigee API proxy requests from any network-enabled machine. See Figure 1.
Note the following supported northbound PSC features:
- You can use PSC with any existing Apigee instance.
- You can attach multiple PSC network endpoint groups (NEGs) to the Envoy-based, Google Cloud global external HTTP(S) load balancer.
- PSC is supported with VPC Service Controls.
You can set an outlier detection traffic policy on the backend service for handling failover scenarios automatically. See the following for more information:
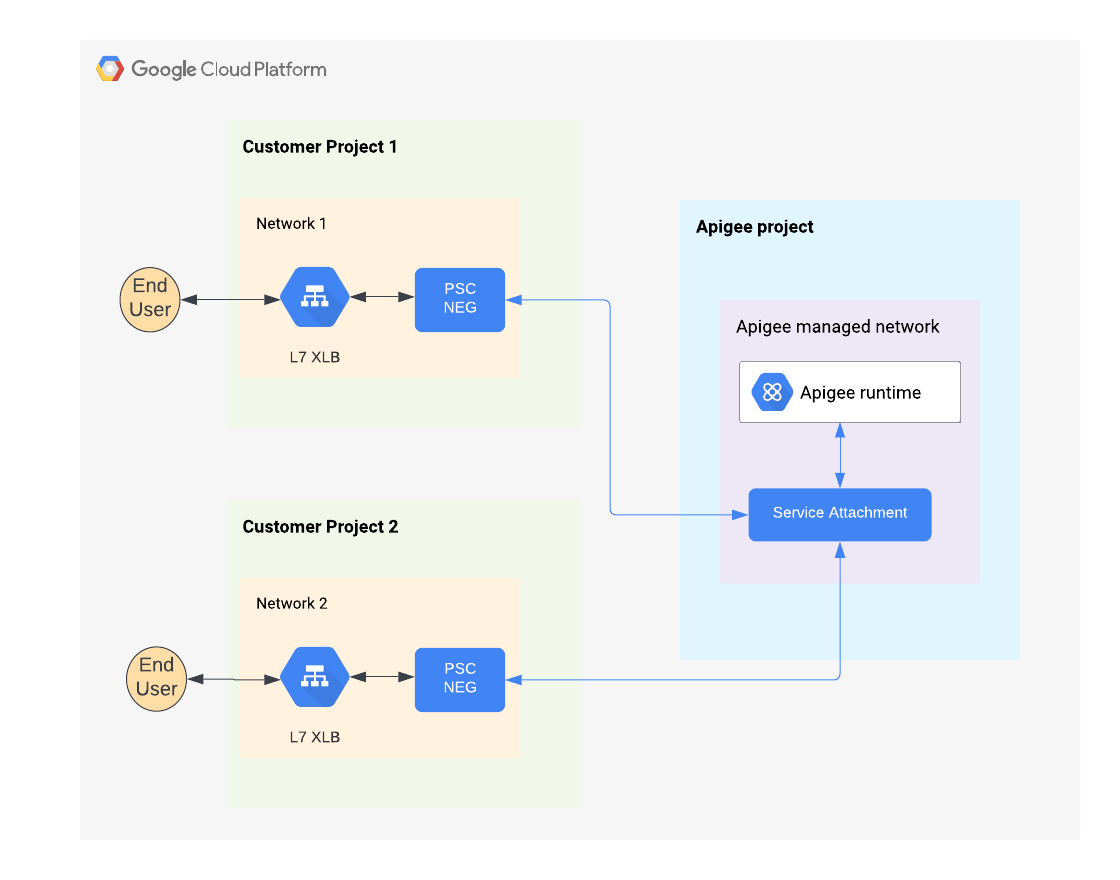
Figure 1: Private service connections
Restrictions
The use of PSC with Apigee currently has the following restrictions:
Updating the consumer accept list for an Apigee instance
On October 10, 2024, the limit on PSC NEG connections allowed per project to an Apigee instance was raised from 20 to 100. For any Apigee instances created before that date, you must perform the steps in this section to update the consumer accept list to take advantage of the new limit. You only need to upgrade each Apigee instance once to receive the new connection limit. See also Private Service Connect (PSC) Limits.
If you need to have more than 1000 PSC NEG connections in total across all of the Cloud projects connected to an Apigee instance, contact Google Cloud Support.
To update the consumer accept list of an Apigee instance to take advantage of the higher connection limit, do the following steps:
Cloud console
For detailed steps, see Edit the accepted projects list.
Apigee API
Edit the existing consumer accept list for your Apigee instance. To use the instances API:
- Get the authentication token for the Apigee API:
TOKEN="$(gcloud auth print-access-token)"
- Get the list of Cloud projects in an instance's consumer accept list:
curl https://apigee.googleapis.com/v1/organizations/PROJECT_ID/instances/INSTANCE_ID \ -H "Authorization: Bearer $TOKEN" -H Content-Type:application/json | jq .consumerAcceptList
- Create a JSON file named
update_consumer_accept_list.jsonthat contains the current list of accepted projects returned by the previous command. For example:{ "consumerAcceptList": [ "dg-runtime-test1", "ne24b79b92c7db623p-tp", "dg-runtime-test2", "jd2fee78402218863p-tp" ] } - Optionally, edit the file to add more projects.
- Update the instance, using the JSON file you created as input. For example:
curl https://apigee.googleapis.com/v1/organizations/PROJECT_ID/instances/INSTANCE_ID?updateMask="consumer_accept_list" \ -X PATCH -H "Authorization: Bearer $TOKEN" -H Content-Type:application/json -d @update_consumer_accept_list.json
Configure PSC routing
We support using PSC for northbound routing from both internal and external clients. For detailed steps, see Step 8: Configure routing of the CLI provisioning instructions.
Multi-region expansion with PSC
You can expand an Apigee organization across multiple regions and use PSC for northbound routing in the new regions. For details, see Expanding Apigee to multiple regions.Deleting an Apigee instance
To delete an Apigee instance that uses PSC, follow these steps:
- Remove and delete the PSC NEG backend from the external load balancer.
- Delete the Apigee runtime instance using the Apigee API. This is a long-running operation that can take up to 20 minutes to complete.
- Optionally retrieve the long-running operation state using the Apigee API.
