Understanding which ports the hybrid runtime plane uses is important for enterprise implementations. This section describes the ports used for secure communications within the runtime plane as well as external ports used for communications with external services.
Internal connections
Communication between the runtime plane and management plane is secured with TLS 1-way and OAuth 2.0. Individual services use different protocols, depending on which service they are communicating with.
The following image shows the ports and communications channels within the hybrid runtime plane:
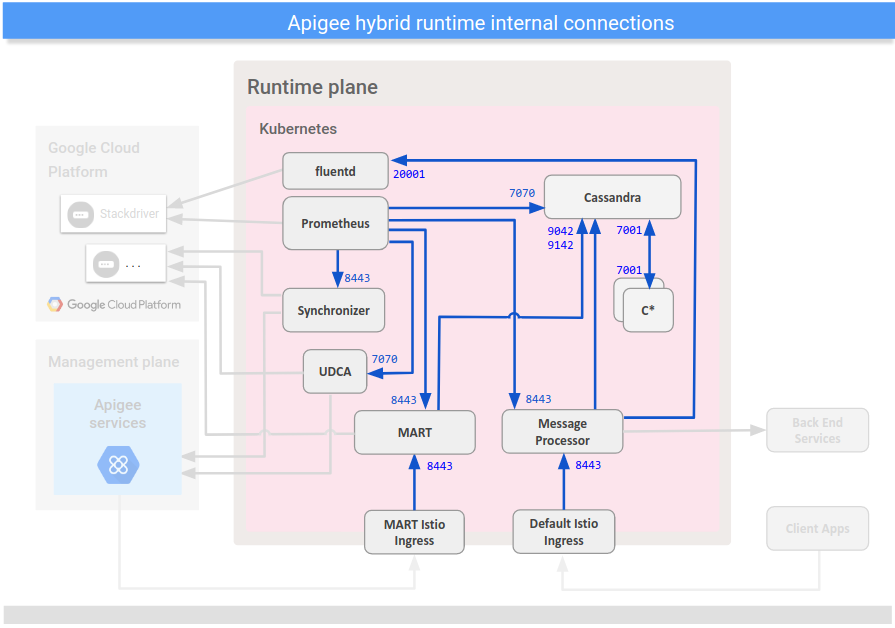
The following table describes the ports and communications channels within the hybrid runtime plane:
| Internal Connections | |||||
|---|---|---|---|---|---|
| Source | Destination | Protocol/Port(s) | Security Protocol | Description | |
| MART | Cassandra | TCP/9042 TCP/9142 |
mTLS | Sends data for persistence | |
| MART Istio Ingress | MART | TCP/8443 | TLS | Requests from the management plane go through the MART Istio Ingress | |
| Default Istio Ingress | Message Processor | TCP/8443 | TLS (Apigee-generated, self-signed cert) | Processes incoming API requests | |
| Message Processor | Cassandra | TCP/9042 TCP/9142 |
mTLS | Sends data for persistence | |
| Message Processor | fluentd (Analytics) | TCP/20001 | mTLS | Streams data to the data collection pod | |
| Cassandra | Cassandra | TCP/7001 | mTLS | Intra-node cluster communications. Note that you can also leave port 7000 open for firewall configuration as a backup option for potential troubleshooting. | |
| Prometheus | Cassandra | TCP/7070 (HTTPS) | TLS | Scrapes metrics data from various services | |
| MART | TCP/8843 (HTTPS) | TLS | |||
| Message Processor | TCP/8843 (HTTPS) | TLS | |||
| Synchronizer | TCP/8843 (HTTPS) | TLS | |||
| UDCA | TCP/7070 (HTTPS) | TLS | |||
External connections
To appropriately configure your network firewall, you should know the inbound and outbound ports used by hybrid to communicate with external services.
The following image shows the ports used for external communications with the hybrid runtime plane:
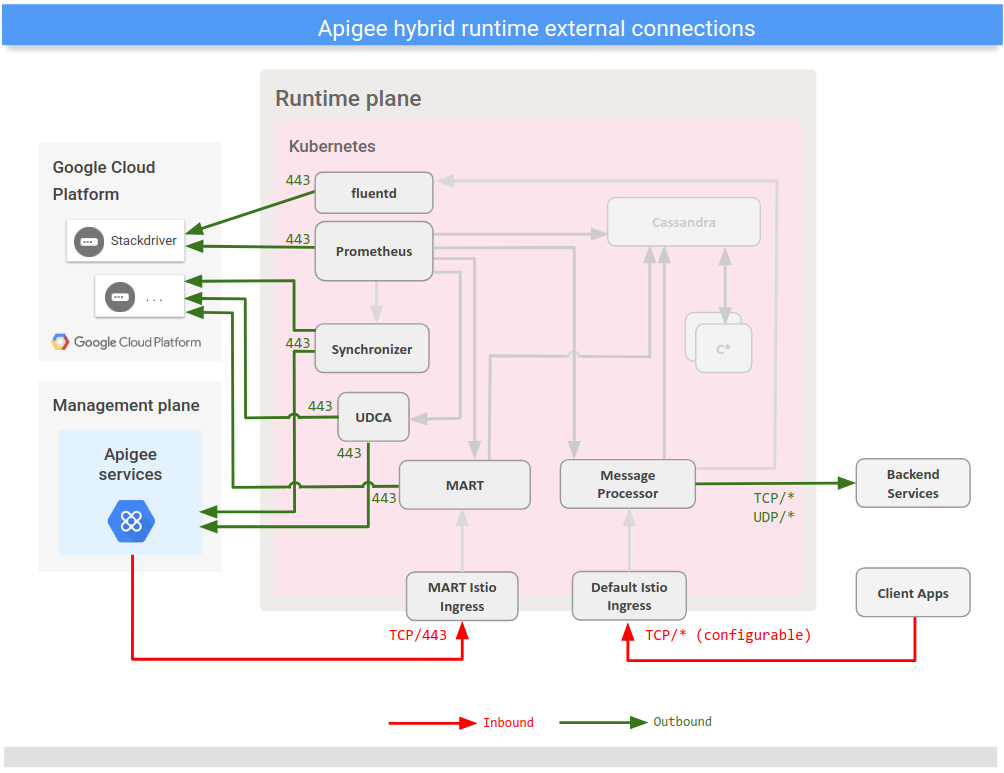
The following table describes the ports used for external communications with the hybrid runtime plane:
| External Connections | |||||
|---|---|---|---|---|---|
| Source | Destination | Protocol/Port(s) | Security Protocol | Description | |
| Inbound Connections (exposed externally) | |||||
| Apigee Services | MART Istio Ingress | TCP/443 | OAuth over TLS 1.2 | Hybrid API calls from the management plane | |
| Client Apps | Default Istio Ingress | TCP/* | None/OAuth over TLS 1.2/mTLS | API requests from external apps | |
| Outbound Connections | |||||
| Message Processor | Backend services | TCP/* UDP/* |
None/OAuth over TLS 1.2 | Sends requests to customer-defined hosts | |
| Synchronizer | Apigee Services | TCP/443 | OAuth over TLS 1.2 | Fetches configuration data; connects to apigee.googleapis.com |
|
| GCP | Connects to iamcredentials.googleapis.com for authorization |
||||
| UDCA (Analytics) | Apigee Services (UAP) | TCP/443 | OAuth over TLS 1.2 | Sends data to UAP in the management plane and to GCP; connects to
apigee.googleapis.com and storage.googleapis.com |
|
| Prometheus (Metrics) | GCP (Stackdriver) | TCP/443 | TLS | Sends data to Stackdriver in the management plane; connects to
monitoring.googleapis.com |
|
| fluentd (Logging) | GCP (Stackdriver) | TCP/443 | TLS | Sends data to Stackdriver in the management plane; connects to
logging.googleapis.com |
|
| MART | GCP | TCP/443 | OAuth over TLS 1.2 | Connects to iamcredentials.googleapis.com for authorization |
|
| * indicates that the port is configurable. Apigee recommends using 443. | |||||
You should not allow external connections for any specific IP addresses associated with
*.googleapis.com. The IP addresses can change since the domain currently resolves to
multiple addresses.
