This page applies to Apigee and Apigee hybrid.
View
Apigee Edge documentation.
![]()
What is Apigee Adapter for Envoy?
Apigee Adapter for Envoy is an Apigee-managed API gateway that uses Envoy to proxy API traffic. Envoy is a popular, open source edge and service proxy designed for cloud-native applications. You can run Apigee Adapter for Envoy on premises or in a multi-cloud environment.
With Apigee Adapter for Envoy, you get a relatively small footprint API gateway application running close to your backend applications. Apigee Adapter for Envoy relies on Apigee for:
- API authentication and authorization (with API keys and OAuth)
- Quota management
- API analytics
Watch videos:
This video offers an overview and demo of Google Cloud's Apigee Adapter for Envoy.
This video describes using the Apigee Adapter for Envoy with Service Mesh.
Installation options
You can use the Apigee Adapter for Envoy in the following context:
- As a native service. See Native Envoy example for Apigee and hybrid .
- As a service deployed to the Istio service mesh integrated with Apigee hybrid. See Apigee hybrid example with Kubernetes.
Apigee Adapter for Envoy
The following figure shows the high level architecture for Apigee Adapter for Envoy. This architecture consists of management plane components deployed on Google Cloud Platform and data plane components running remotely on premises or in a cloud provider environment. The data plane includes the Envoy proxy and Apigee Remote Service. The role of each component is described following the figure.
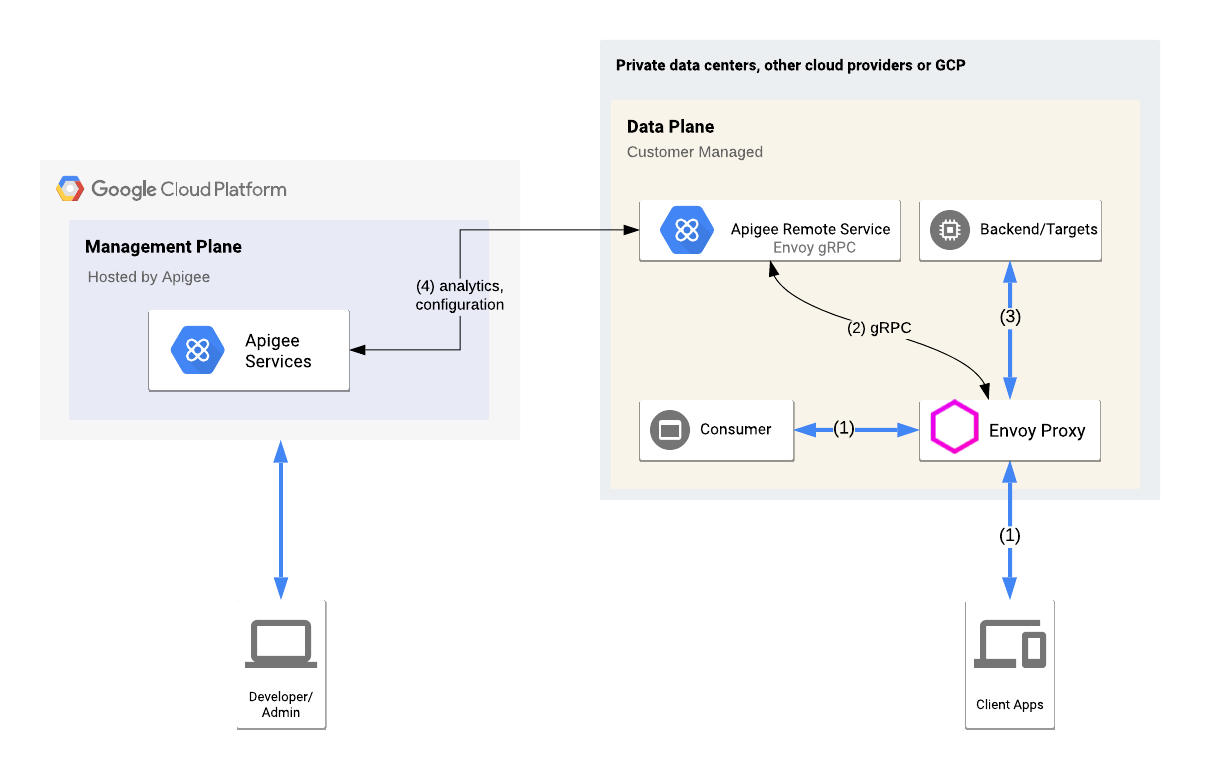
- A consumer or client app accesses an API endpoint exposed by the Envoy proxy.
- The Envoy proxy passes the security context (using HTTP headers) to the Apigee Remote Service. The Apigee Remote Service acts as a policy decision point (PDP) and advises Envoy to allow or deny access to the API consumer for the request.
- If the call is allowed, the Envoy proxy forwards the request to the backend.
- The Apigee Remote Service asynchronously polls the management plane and downloads proxy, API product, and other configuration that it needs to operate.
Why use Apigee Adapter for Envoy?
Moving the API management component close to backend target applications can reduce network latency. While you can install Apigee on-premises in a private cloud, a full deployment of Apigee is necessarily large and complex to support its full feature-set and data-heavy features like key management, monetization, and analytics. This means that deploying Apigee on premises in each data-center is not always desirable.
Benefits of using Apigee Adapter for Envoy include:
-
Reduced latency of API traffic for services that run in close proximity.
- Use of the full suite of Apigee Analytics metrics, dashboards, and APIs.
- Keeps API traffic within the enterprise-approved boundaries for security or compliance purposes.
- Asynchronous communication with Apigee allows API traffic data to be captured and sent to Apigee without affecting latency.
- The adapter can tolerate temporary communication interruptions with the management
plane. Over time, however, an interruption can lead to loss of functionality. The adapter requires
communication with the management plane for:
- Generating OAuth tokens
- Verifying API keys (connection is required for the first verification, after which it is cached)
- Enforcing quotas
- Sending analytics data to the management plane
