This page describes how to connect Microsoft SharePoint Online to Gemini Enterprise using data federation.
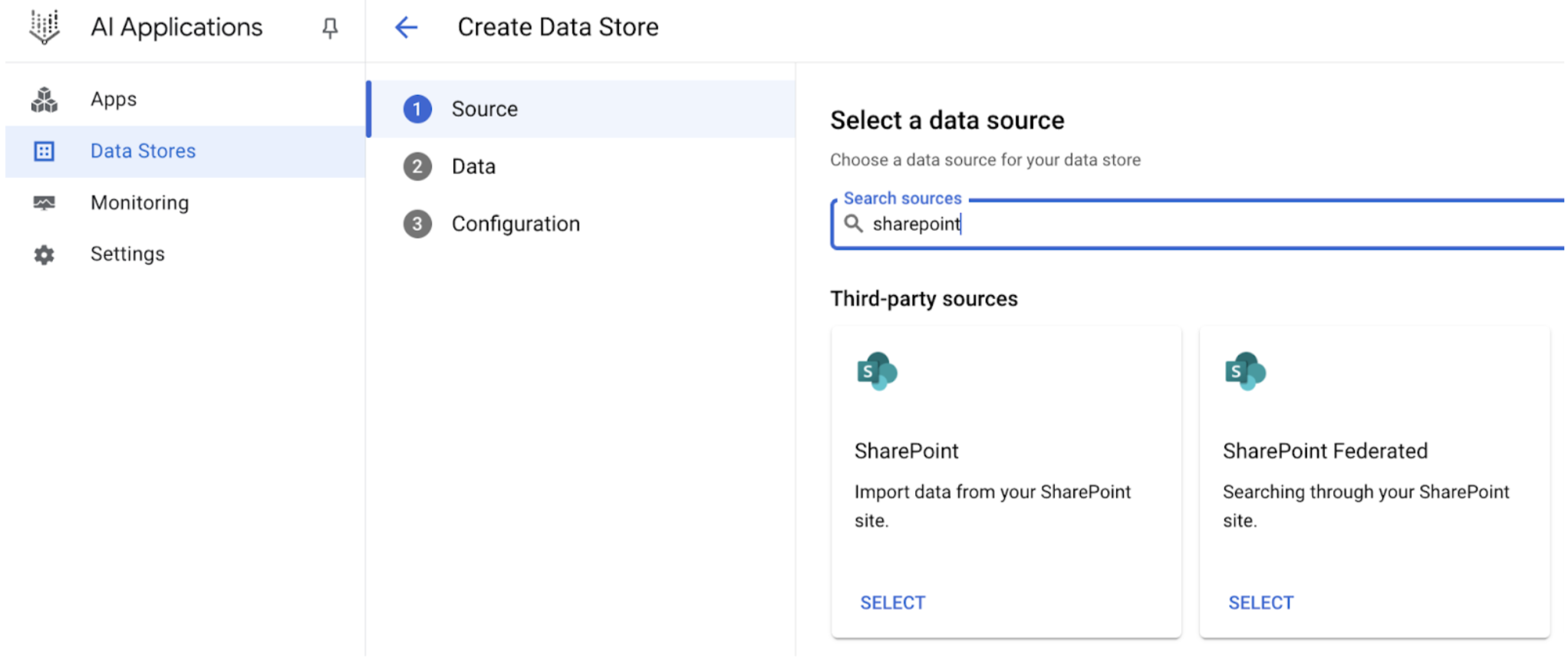
Use the following procedure to search through your SharePoint account using federated search.About data federation
With data federation, Gemini Enterprise directly retrieves information from the third-party data sources using APIs, instead of copying the data into Gemini Enterprise. Using this approach, you can access external data sources immediately, without waiting for ingestion.
Before you begin
Before you can create the connector in Gemini Enterprise, you must set up an Entra application registration to enable secure access to SharePoint.
Register Gemini Enterprise as an OAuth 2.0 application in Entra.
- Navigate to Microsoft Entra admin center.
- In the menu, expand the Applications section and select App registrations.
- On the App registrations page, select New registration.
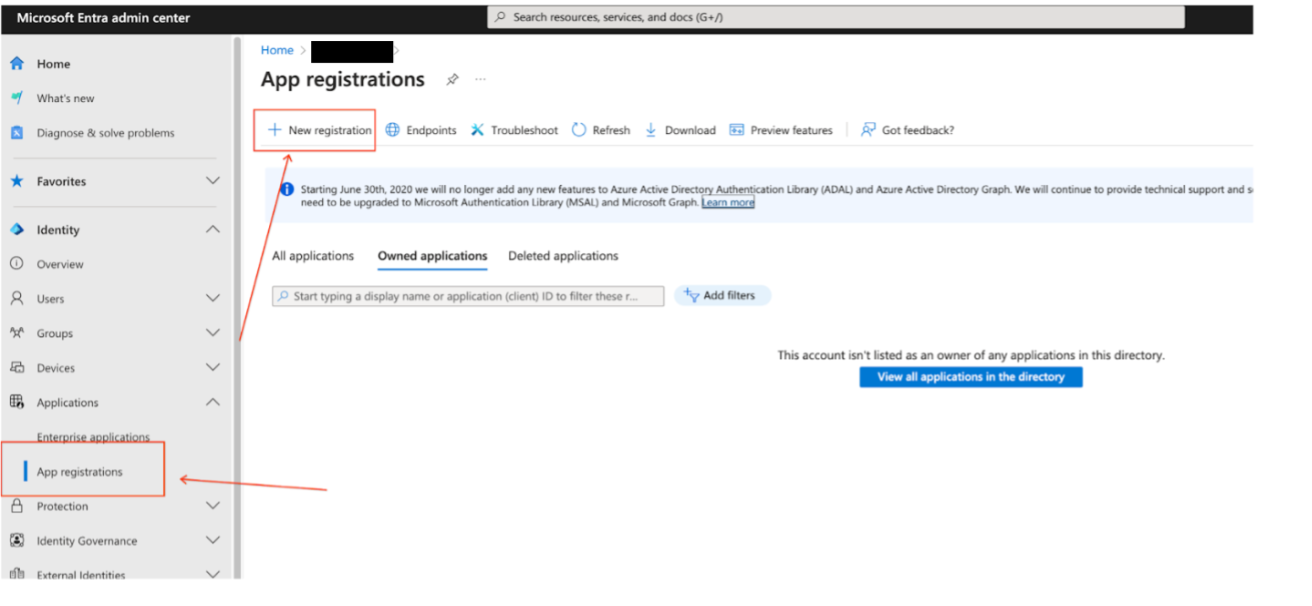
Register a new app in Microsoft Entra admin center - Create an app registration on the Register an application page:
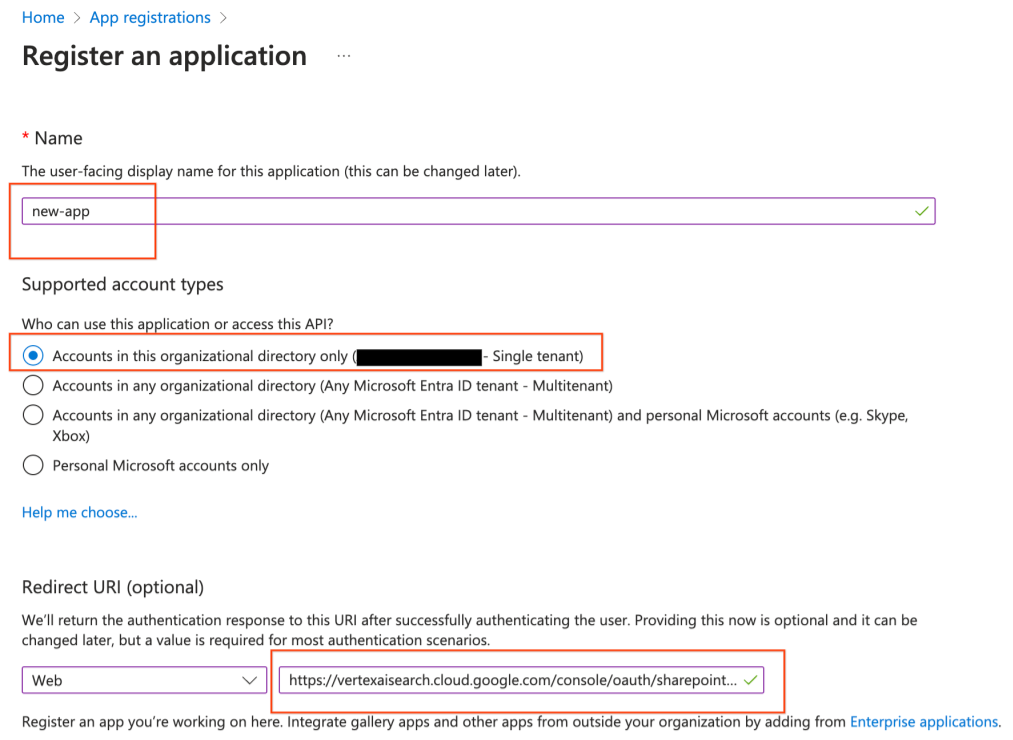
Select the account type and enter the redirect URI - In the Supported account types section, select Accounts in the organizational directory only.
In the Redirect URI section, select Web and enter the following URLs as web callback URLs (or redirect URLs):
https://vertexaisearch.cloud.google.com/console/oauth/sharepoint_oauth.htmlhttps://vertexaisearch.cloud.google.com/oauth-redirect
Add a client secret:
- Go to Certificates & secrets and click New client secret.
- Copy and note the secret string.
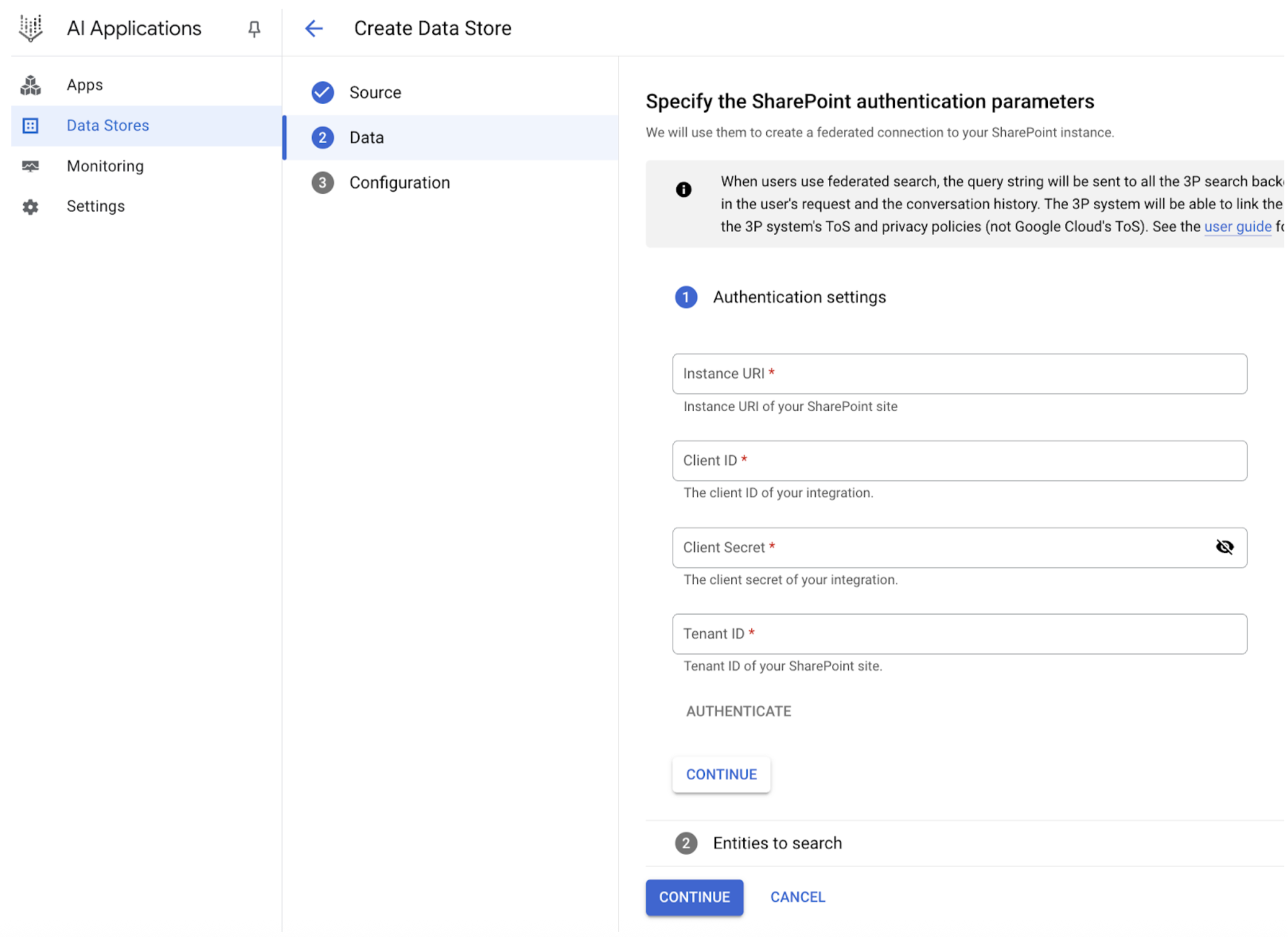
Collect the following credentials:
- Client ID
- Client secret
- Instance URL
- Tenant ID
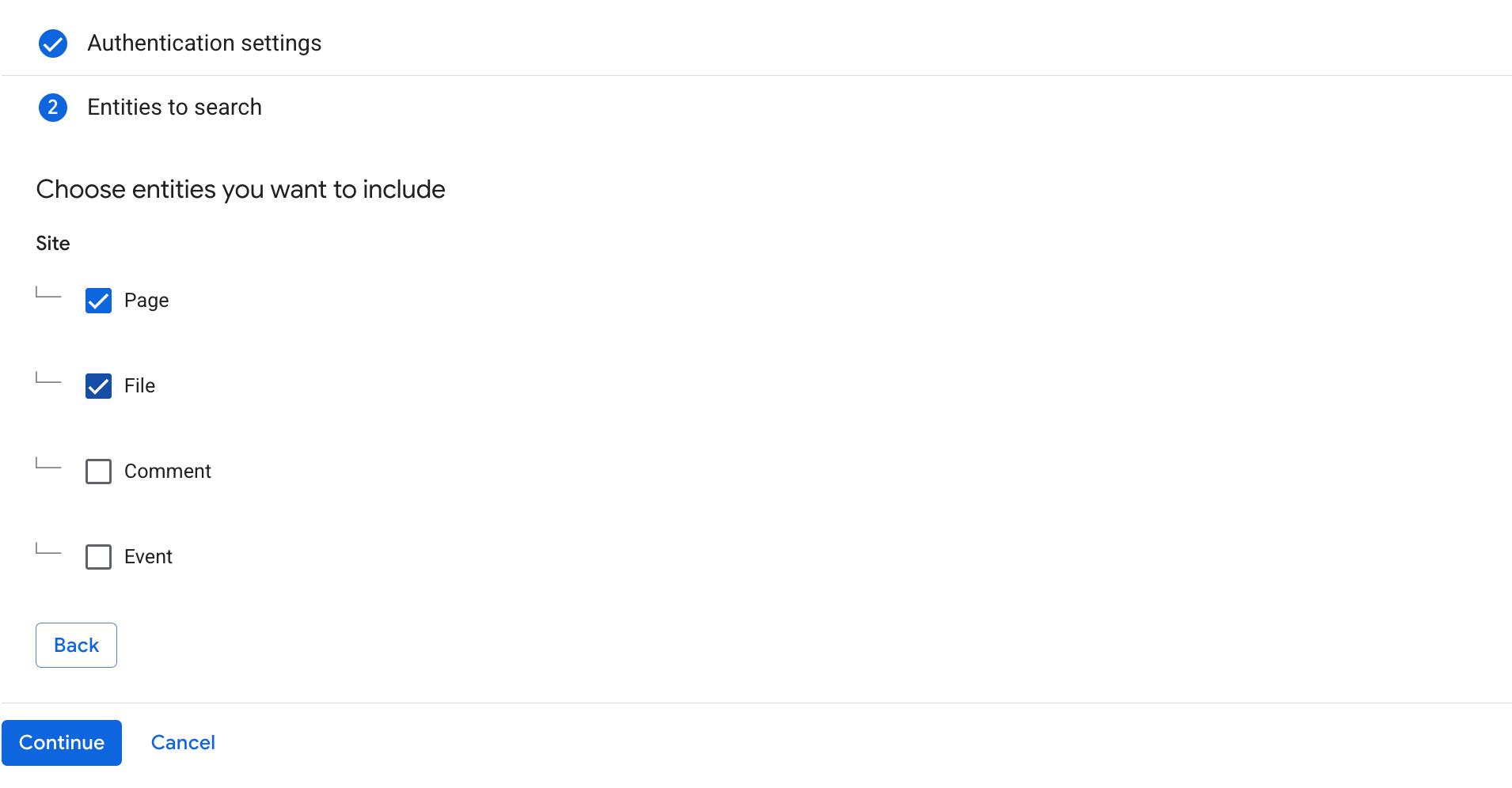
Configure these SharePoint API (Application) permissions with administrator consent:
Permission Type AllSites.Read Delegated MyFiles.Read Delegated Sites.Search.All Delegated
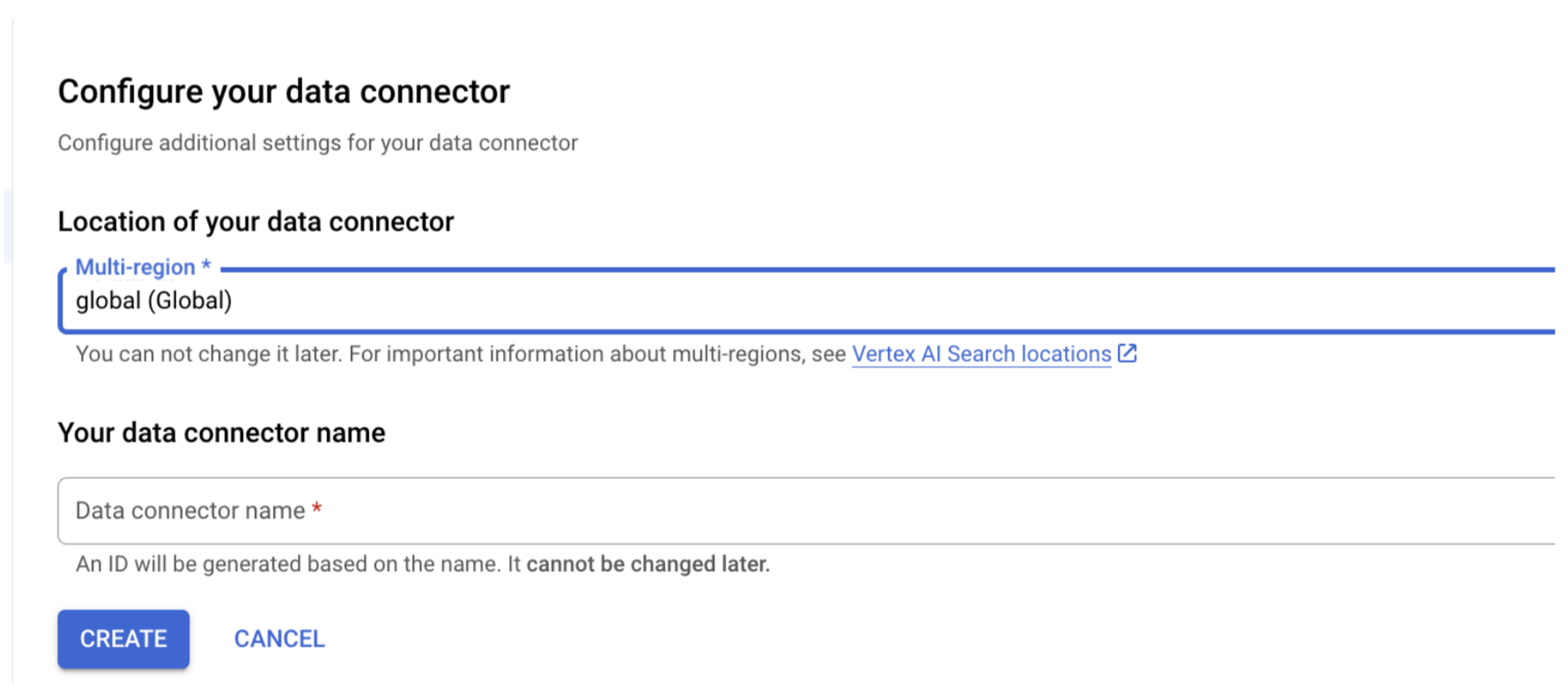
Create a federated search connector with SharePoint
User authorization
After creating a federated search data store, you can see it listed as one of the data sources in your source management panel. If you haven't previously authorized Gemini Enterprise, then you can't select the data source. Instead, an Authorize button appears next to it.
To initiate the authorization flow:
- Click Authorize.
You are redirected to the SharePoint authorization server.
Click Authorize Sign in to your account.
Click Grant access. After granting access, you are redirected back to Gemini Enterprise to complete the authorization flow. Gemini Enterprise obtains the
access_token, and uses it to access the 3P search.
Query execution
When you enter a search query:
- If SharePoint is authorized, Gemini Enterprise sends the query to the SharePoint API.
- Gemini Enterprise blends the results with those from other sources and displays them.
Data handling
When using third-party federated search, your query string is sent to the third-party search backend. These third parties may associate queries with your identity. If multiple federated search data sources are enabled, the query may be sent to all of them.
Once the data reaches the third-party system, it is governed by that system's Terms of Service and privacy policies (not by Google Cloud's terms).