本文档介绍了 Google Distributed Cloud (GDC) 气隙资源层次结构,以及如何在气隙实例中管理资源。如需了解跨多个可用区管理资源的概念,请参阅多可用区概览。
GDC 资源层次结构有两个用途:
- 提供所有权层次结构,该层次结构将资源的生命周期绑定到层次结构中该资源的直接父级。
- 为访问权限控制和组织政策提供连接点与继承机制。
GDC 资源层次结构与操作系统中的文件系统类似,能够以分层方式组织和管理实体。一般来说,每项资源有且仅有一个父项。通过这种分层化的资源组织方式,您可以设置访问权限控制政策(例如 Identity and Access Management [IAM]),子资源可以继承这些政策。
如需详细了解组织访问权限边界的最佳实践,请参阅设计资源之间的访问权限边界。
资源结构详情
以下实体是 GDC 资源层次结构中可识别的资源类型:
GDC 资源以分层方式进行组织。资源层次结构中的大多数资源有且仅有一个父项。此例外情况仅适用于最高资源。在最低级层上,服务资源是构成所有 GDC 服务的基本组成部分。
组织是 GDC 资源层次结构的最高层级,属于某个组织的所有资源都在组织资源下划分成组。这使您可以集中查看和控制属于组织的所有资源。
项目和集群均属于组织级资源。它们可以相互附加,以整理服务资源。不过,项目和集群彼此独立运行。这种灵活性为组织服务和工作负载提供了许多不同的选择。例如,您可以拥有一个专用于单个项目的集群。同样,一个集群可以跨多个项目。
服务资源是必须属于项目或集群的实体,不能在项目或集群之间共享。服务资源的示例包括虚拟机 (VM)、数据库、存储分区和备份。大多数此类较低级别的资源都以项目资源作为其父级资源。
下图展示了 GDC 资源层次结构示例:
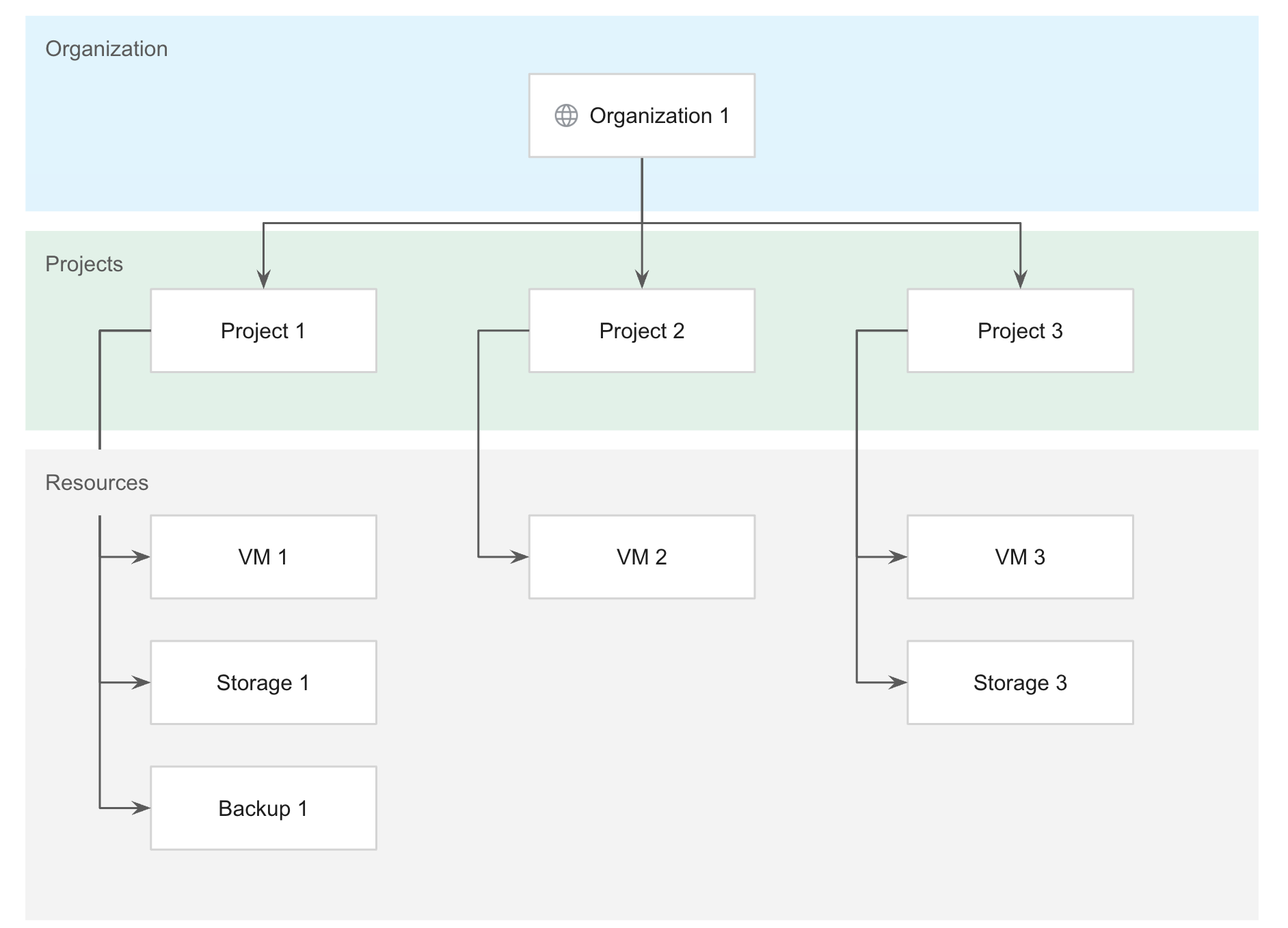
如需详细了解最佳实践组织资源层次结构以实现最佳工作负载管理,请参阅设计用户工作负载分离。
组织
组织资源代表一个管理单元或业务职能(例如公司),是 GDC 资源层次结构中的顶级资源。组织定义了一个安全边界,其中包含要一起管理的基础设施资源,以便用户可以部署应用工作负载。组织是全球性的,涵盖一个宇宙中的所有区域。在组织内,虚拟机和存储卷等服务资源按项目进行逻辑分组。
所有项目、集群和服务资源都属于您的组织,而不是其创建者。这意味着,如果创建组织中任何资源类型的用户离开组织,相应资源不会被删除。相反,所有资源类型都遵循 GDC 中的组织生命周期。
应用于组织资源的 IAM 访问权限控制政策适用于组织中所有资源的整个层次结构。如需详细了解如何授予组织范围的政策和权限,请参阅组织政策和 IAM 部分。
项目
项目是每个服务都必须集成的租户单元。项目可用于对服务资源进行逻辑分组。项目是全球性的,涵盖一个宇宙中的所有可用区。
项目可用于细分组织内的服务资源,并提供用于管理资源的生命周期和政策边界。项目内的服务资源永远不会比项目本身更长寿,也不会在项目之间移动,从而确保在资源生命周期内始终可以进行控制。 因此,您必须在项目命名空间内部署任何类型的资源。
项目被视为一个适当的 Kubernetes 命名空间,可跨组织中的多个集群。命名空间相同性会将给定名称的所有命名空间视为同一组织内所有集群的同一命名空间。单个命名空间在整个集集群中具有一致的所有者。服务提供商通过在命名空间中创建控制平面和数据平面组件来创建项目范围的服务。
项目的命名空间包含以下内容:
- 项目范围的服务 API。
- 项目级政策配置,例如角色和角色绑定。
您可以将项目附加到组织中的部分集群。您可以在项目命名空间内将容器化工作负载部署到这些集群。命名空间相同性概念适用于这些集群上的项目命名空间。命名空间范围的政策(例如基于角色的访问权限 (RBAC) 政策)适用于所有这些命名空间。
如需详细了解项目,请参阅项目概览。
Kubernetes 集群
Kubernetes 集群是一组节点,用于运行容器化工作负载,是 GKE on GDC 的一部分。您可以预配 Kubernetes 集群,以满足应用的计算需求。集群的范围限定为组织,并且必须附加到一个或多个项目。
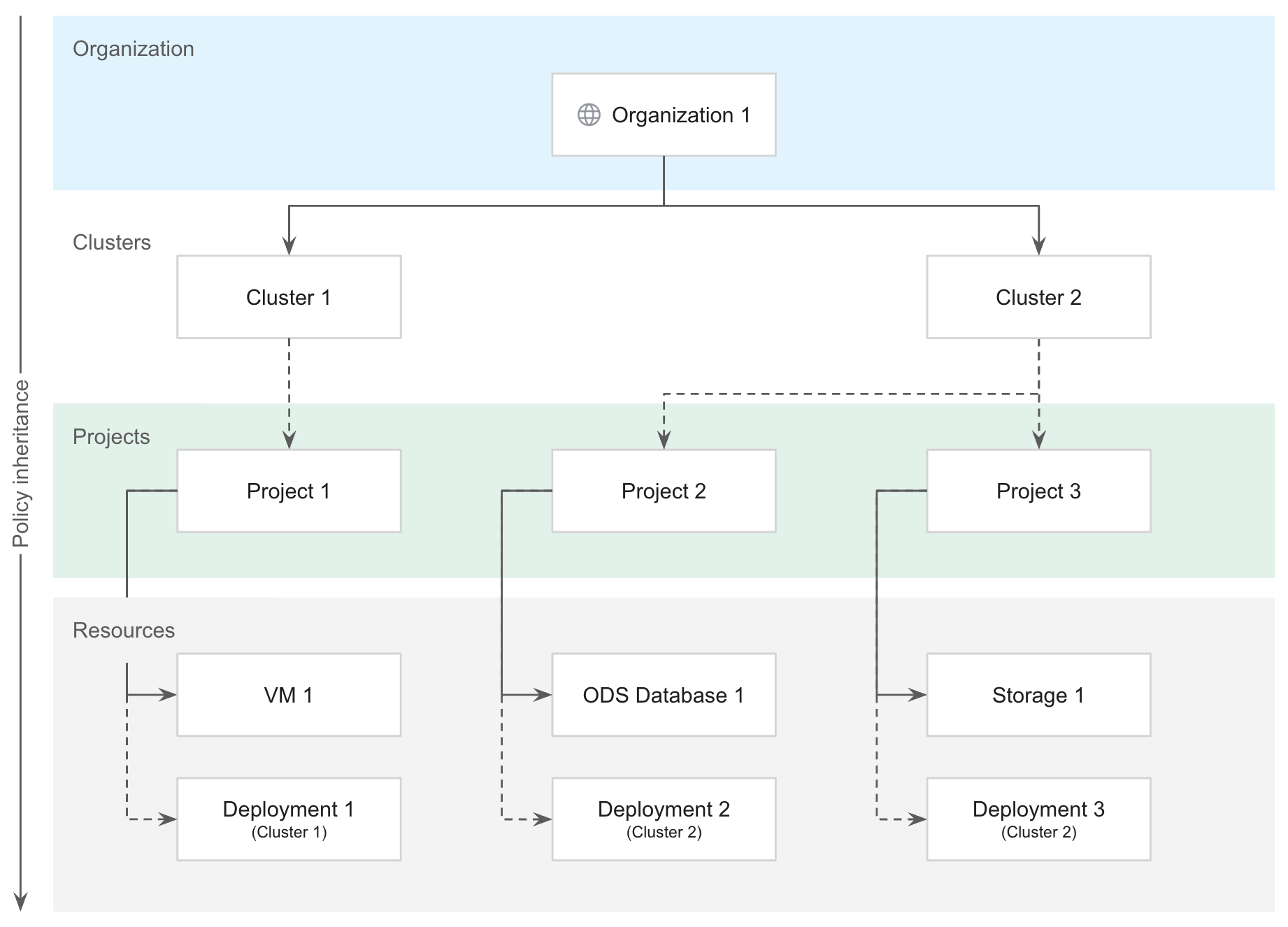
集群将基础设施资源细分为隔离的池,供组织内的项目使用。集群在逻辑上也是相互分离的,可提供不同的故障网域和隔离保证。通过强制执行组织级政策,可以确保团队和用户能够共享集群,同时还能保证性能和资源。 此外,组织政策还允许虚拟机工作负载与容器工作负载并行运行,而不会增加运营复杂性。
对于必须部署容器化工作负载的实例,集群非常有用。不过,如果选择部署基于虚拟机的工作负载,则 GDC 中不需要存在 Kubernetes 集群。
集群仅属于可用区级资源,无法跨多个可用区。如需在多可用区部署中运行集群,您必须在每个可用区中手动部署集群。
如需详细了解 Kubernetes 集群,请参阅管理 Kubernetes 集群部分。
服务资源
服务资源包括许多实体,例如:
- 虚拟机
- 数据库
- 存储桶
- 容器化工作负载
- 备份
服务资源必须属于某个项目,或者(对于容器化工作负载)属于某个集群,并且不能在项目之间共享。这意味着项目中的服务资源永远不会比项目本身存在的时间长,从而确保在资源存在期间始终可以进行控制。
服务资源可以全球部署,也可以按地区部署,具体取决于资源类型。如需了解多可用区部署选项,请参阅特定服务的文档。服务资源默认处于启用状态,可以使用组织政策将其停用。

