This guide helps you understand, deploy, and use the Ecommerce platform with serverless computing solution. This solution demonstrates how to build and run an ecommerce application for a retail organization, with a publicly visible online store website. It shows you how to create an application that scales to handle spikes in usage (for example, during peak scale events like a seasonal sale), and that can manage requests based on the visitor's location. This design helps the online store provide a consistent service to geographically distributed customers.
This solution is a good starting point if you want to learn how to deploy scalable ecommerce web apps with serverless capabilities. If you want granular operational control, check out the Ecommerce web app deployed on Kubernetes solution.
This document assumes that you're familiar with basic cloud concepts, though not necessarily Google Cloud. Experience with Terraform is helpful.
Objectives
This solution guide helps you do the following:
- Learn how to design a system architecture for an ecommerce website.
- Optimize an ecommerce website for performance, scale, and responsiveness.
- Monitor and anticipate load limitations.
- Use tracing and error reporting to understand and manage problems.
Products
The solution uses the following Google Cloud products:
- Cloud Run: A fully managed service that lets you build and deploy serverless containerized apps. Google Cloud handles scaling and other infrastructure tasks so that you can focus on the business logic of your code.
- Cloud SQL: A cloud-based PostgreSQL database that's fully managed on the Google Cloud infrastructure.
- Secret Manager: A service that lets you store, manage, and access secrets as binary blobs or text strings. You can use Secret Manager to store database passwords, API keys, or TLS certificates that are needed by an application at runtime.
- Cloud Storage: An enterprise-ready service that provides low-cost, no-limit object storage for diverse data types. Data is accessible from within and outside of Google Cloud and is replicated geo-redundantly.
- Firebase Hosting: A fully managed hosting service to deploy and serve your web applications and static content.
- Cloud Logging: A service that lets you store, search, analyze, monitor, and alert on logging data and events from Google Cloud and other clouds.
- Cloud Trace: A distributed tracing system for Google Cloud that helps you understand how long it takes your application to handle incoming requests from users or other applications, and how long it takes to complete operations like RPC calls performed when handling the requests.
- Error Reporting: This service aggregates and displays errors produced in your running cloud services. Error Reporting groups errors which are considered to have the same root cause.
Architecture
The following diagram shows the architecture of the solution:
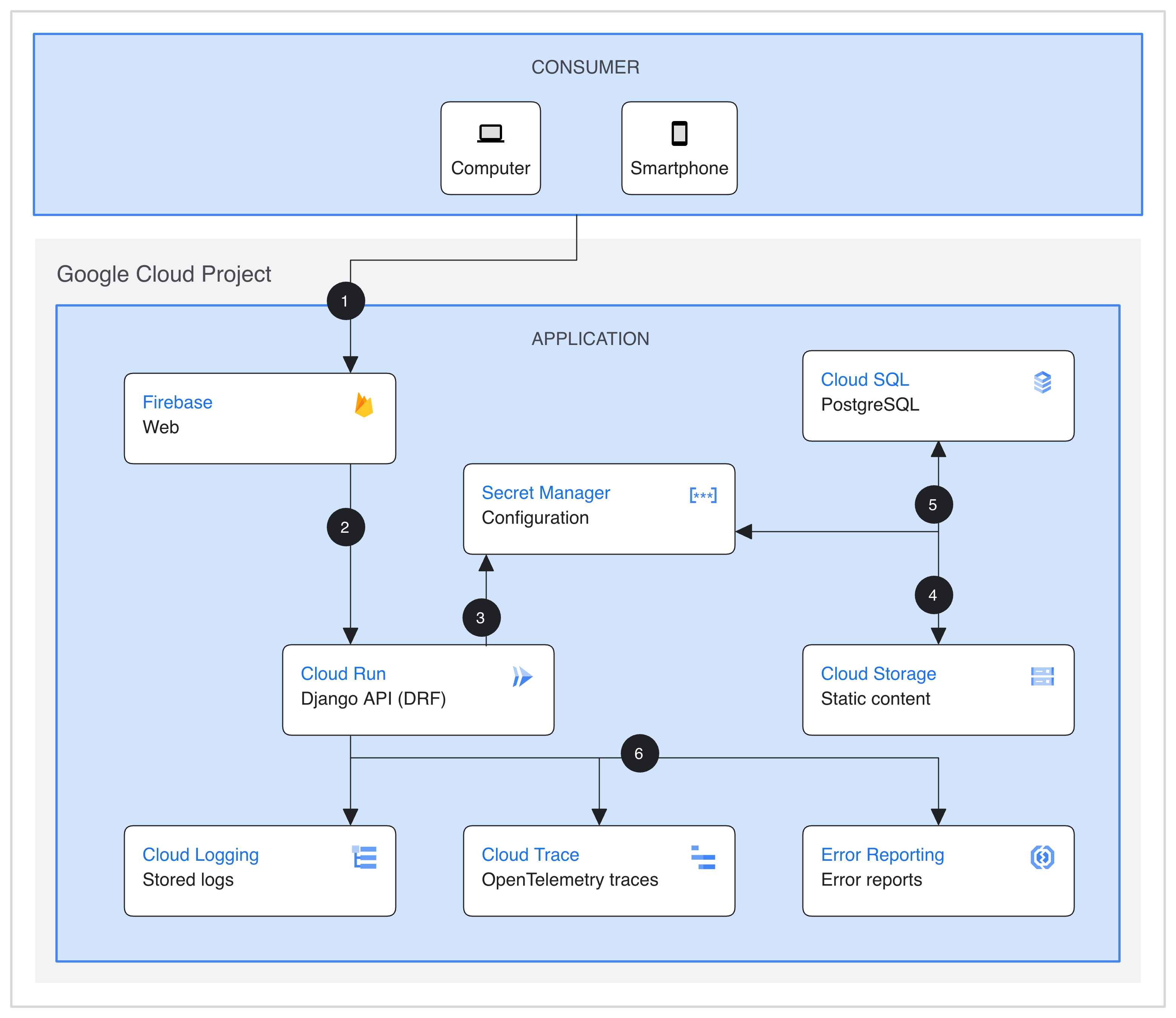
Request flow
The following is the request processing flow of the ecommerce platform. The steps in the flow are numbered as shown in the preceding architecture diagram.
- A Firebase Hosting client frontend. The frontend uses Lit and web components for client-side rendering of API data.
- The web client calls an API backend that is running as a Cloud Run service. The Cloud Run API server is written in Django using the Django REST Framework.
- The configuration and other secrets for the Python application are stored in Secret Manager.
- Static assets for the application are stored in Cloud Storage.
- A Cloud SQL database, using PostgreSQL, is used as the relational database backend for the Python application.
- Cloud Logging, Cloud Trace, and Error Reporting stores logs, OpenTelemetry traces, and error reports sent by other cloud products and the Cloud Run API server. This data enables monitoring for the correct application behavior and troubleshooting of unexpected behavior.
Cost
For an estimate of the cost of the Google Cloud resources that the Ecommerce platform with serverless computing solution uses, see the precalculated estimate in the Google Cloud Pricing Calculator.
Use the estimate as a starting point to calculate the cost of your deployment. You can modify the estimate to reflect any configuration changes that you plan to make for the resources that are used in the solution.
The precalculated estimate is based on assumptions for certain factors, including the following:
- The Google Cloud locations where the resources are deployed.
- The amount of time that the resources are used.
Before you begin
To deploy this solution, you first need a Google Cloud project and some IAM permissions.
Create or choose a Google Cloud project
When you deploy the solution, you choose the Google Cloud project where the resources are deployed. You can either create a new project or use an existing project for the deployment.
If you want to create a new project, do so before you begin the deployment. Using a new project can help avoid conflicts with previously provisioned resources, such as resources that are used for production workloads.
To create a project, complete the following steps:
-
Ensure that you have the Project Creator IAM role
(
roles/resourcemanager.projectCreator). Learn how to grant roles. -
In the Google Cloud console, go to the project selector page.
-
Click Create project.
-
Name your project. Make a note of your generated project ID.
-
Edit the other fields as needed.
-
Click Create.
Get the required IAM permissions
To start the deployment process, you need the Identity and Access Management (IAM) permissions that are listed in the following table.
If you created a new project for this solution, then you have the roles/owner
basic role
in that project and have all the necessary permissions. If you don't have the
roles/owner role, then ask your administrator to grant these permissions (or
the roles that include these permissions) to you.
| IAM permission required | Predefined role that includes the required permissions |
|---|---|
|
Service Usage Admin ( roles/serviceusage.serviceUsageAdmin) |
|
Service Account Admin ( roles/iam.serviceAccountAdmin) |
|
Project IAM Admin ( roles/resourcemanager.projectIamAdmin) |
config.deployments.createconfig.deployments.list |
Cloud Infrastructure Manager Admin ( roles/config.admin) |
iam.serviceAccount.actAs |
Service Account User ( roles/iam.serviceAccountUser) |
About temporary service account permissions
If you start the deployment process through the console, Google creates a service account to deploy the solution on your behalf (and to delete the deployment later if you choose). This service account is assigned certain IAM permissions temporarily; that is, the permissions are revoked automatically after the solution deployment and deletion operations are completed. Google recommends that after you delete the deployment, you delete the service account, as described later in this guide.
View the roles that are assigned to the service account
These roles are listed here in case an administrator of your Google Cloud project or organization needs this information.
- Cloud SQL Admin (
roles/cloudsql.admin) - Compute Engine Admin (
roles/compute.admin) - Compute Engine Network Admin (
roles/compute.networkAdmin) - Firebase Service Management Service Agent (
roles/firebase.managementServiceAgent) - Firebase Hosting Admin (
roles/firebasehosting.admin) - Service Account Admin (
roles/iam.serviceAccountAdmin) - Service Account User (
roles/iam.serviceAccountUser) - Project IAM Admin (
roles/resourcemanager.projectIamAdmin) - Cloud Run Admin (
roles/run.admin) - Secret Manager Admin (
roles/secretmanager.admin) - Cloud Storage Admin (
roles/storage.admin)
Deploy the solution
To help you deploy this solution with minimal effort, a Terraform configuration is provided in GitHub. The Terraform configuration defines all the Google Cloud resources that are required for the solution.
You can deploy the solution by using one of the following methods:
Through the console: Use this method if you want to try the solution with the default configuration and see how it works. Cloud Build deploys all the resources that are required for the solution. When you no longer need the deployed solution, you can delete it through the console. Any resources that you create after you deploy the solution might need to be deleted separately.
To use this deployment method, follow the instructions in Deploy through the console.
Using the Terraform CLI: Use this method if you want to customize the solution or if you want to automate the provisioning and management of the resources by using the infrastructure as code (IaC) approach. Download the Terraform configuration from GitHub, optionally customize the code as necessary, and then deploy the solution by using the Terraform CLI. After you deploy the solution, you can continue to use Terraform to manage the solution.
To use this deployment method, follow the instructions in Deploy using the Terraform CLI.
Deploy through the console
Complete the following steps to deploy the preconfigured solution.
In the Google Cloud Jump Start Solutions catalog, go to the Ecommerce platform with serverless computing solution.
Go to the Ecommerce platform with serverless computing solution
Review the information that's provided on the page, such as the estimated cost of the solution and the estimated deployment time.
When you're ready to start deploying the solution, click Deploy.
A step-by-step configuration pane is displayed.
Complete the steps in the configuration pane.
Note the name that you enter for the deployment. This name is required later when you delete the deployment.
When you click Deploy, the Solution deployments page is displayed. The Status field on this page shows Deploying.
Wait for the solution to be deployed.
If the deployment fails, the Status field shows Failed. You can use the Cloud Build log to diagnose the errors. For more information, see Errors when deploying through the console.
After the deployment is completed, the Status field changes to Deployed.
To view and use the deployed ecommerce web app, follow the instructions in Explore your Avocano deployment.
To view the Google Cloud resources that are deployed and their configuration, take an interactive tour.
When you no longer need the solution, you can delete the deployment to avoid continued billing for the Google Cloud resources. For more information, see Delete the deployment.
Deploy using the Terraform CLI
This section describes how you can customize the solution or automate the provisioning and management of the solution by using the Terraform CLI. Solutions that you deploy by using the Terraform CLI are not displayed in the Solution deployments page in the Google Cloud console.
Set up the Terraform client
You can run Terraform either in Cloud Shell or on your local host. This guide describes how to run Terraform in Cloud Shell, which has Terraform preinstalled and configured to authenticate with Google Cloud.
The Terraform code for this solution is available in a GitHub repository.
Clone the GitHub repository to Cloud Shell.
A prompt is displayed to confirm downloading the GitHub repository to Cloud Shell.
Click Confirm.
Cloud Shell is launched in a separate browser tab, and the Terraform code is downloaded to the
$HOME/cloudshell_opendirectory of your Cloud Shell environment.In Cloud Shell, check whether the current working directory is
$HOME/cloudshell_open/terraform-dynamic-python-webapp/infra. This is the directory that contains the Terraform configuration files for the solution. If you need to change to that directory, run the following command:cd $HOME/cloudshell_open/terraform-dynamic-python-webapp/infraInitialize Terraform by running the following command:
terraform initWait until you see the following message:
Terraform has been successfully initialized!
Configure the Terraform variables
The Terraform code that you downloaded includes variables that you can use to customize the deployment based on your requirements. For example, you can specify the Google Cloud project and the region where you want the solution to be deployed.
Make sure that the current working directory is
$HOME/cloudshell_open/terraform-dynamic-python-webapp/infra. If it isn't, go to that directory.In the same directory, create a text file named
terraform.tfvars.In the
terraform.tfvarsfile, copy the following code snippet, and set values for the required variables.- Follow the instructions that are provided as comments in the code snippet.
- This code snippet includes only the variables for which you must set
values. The Terraform configuration includes other variables that have
default values. To review all the variables and the default values, see
the
variables.tffile that's available in the$HOME/cloudshell_open/terraform-dynamic-python-webapp/infradirectory. Make sure that each value that you set in the
terraform.tfvarsfile matches the variable type as declared in thevariables.tffile. For example, if the type that's defined for a variable in thevariables.tffile isbool, then you must specifytrueorfalseas the value of that variable in theterraform.tfvarsfile.# This is an example of the terraform.tfvars file. # The values in this file must match the variable types declared in variables.tf. # The values in this file override any defaults in variables.tf. # ID of the project in which you want to deploy the solution project_id = "PROJECT_ID" # Google Cloud region where you want to deploy the solution # Example: us-central1 region = "REGION" # Google Cloud zone where you want to deploy the solution # Example: us-central1-a zone = "ZONE" # Container Registry that hosts the client image client_image_host = "hsa-public/serverless-ecommerce" # Container Registry that hosts the server image server_image_host = "hsa-public/serverless-ecommerce"For information about the values that you can assign to the required variables, see the following:
- PROJECT_ID: Identifying projects
- REGION and ZONE: Available regions and zones
Validate and review the Terraform configuration
Make sure that the current working directory is
$HOME/cloudshell_open/terraform-dynamic-python-webapp/infra. If it isn't, go to that directory.Verify that the Terraform configuration has no errors:
terraform validateIf the command returns any errors, make the required corrections in the configuration and then run the
terraform validatecommand again. Repeat this step until the command returns the following message:Success! The configuration is valid.Review the resources that are defined in the configuration:
terraform planIf you didn't create the
terraform.tfvarsfile as described earlier, Terraform prompts you to enter values for the variables that don't have default values. Enter the required values.The output of the
terraform plancommand is a list of the resources that Terraform provisions when you apply the configuration.If you want to make any changes, edit the configuration and then run the
terraform validateandterraform plancommands again.
Provision the resources
When no further changes are necessary in the Terraform configuration, deploy the resources.
Make sure that the current working directory is
$HOME/cloudshell_open/terraform-dynamic-python-webapp/infra. If it isn't, go to that directory.Apply the Terraform configuration:
terraform applyIf you didn't create the
terraform.tfvarsfile as described earlier, Terraform prompts you to enter values for the variables that don't have default values. Enter the required values.Terraform displays a list of the resources that will be created.
When you're prompted to perform the actions, enter
yes.Terraform displays messages showing the progress of the deployment.
If the deployment can't be completed, Terraform displays the errors that caused the failure. Review the error messages and update the configuration to fix the errors. Then run the
terraform applycommand again. For help with troubleshooting Terraform errors, see Errors when deploying the solution using the Terraform CLI.After all the resources are created, Terraform displays the following message:
Apply complete!To view and use the deployed ecommerce web app, follow the instructions in Explore your Avocano deployment.
To view the Google Cloud resources that are deployed and their configuration, take an interactive tour.
When you no longer need the solution, you can delete the deployment to avoid continued billing for the Google Cloud resources. For more information, see Delete the deployment.
Explore your Avocano deployment
You have now deployed the Avocano website application! You can visit the Avocano website and look around, and then explore how the solution works in Google Cloud console. Be aware that it can take a few minutes after deploying the application for the site to show up at the provided address.
What is Avocano?
This solution uses a sample application named Avocano to demonstrate the deployment and management of a web app with many of the tools and products used for serverless applications. Avocano is an application that mimics a real-world implementation of an ecommerce web app.
The Avocano frontend presents a faux storefront, where you can add items to your cart, and attempt to complete a checkout process, but then the store reveals it is fake (Avoca--no!). While you can't actually purchase an avocado, the application demonstrates inventory management by decreasing the amount of available product by one.
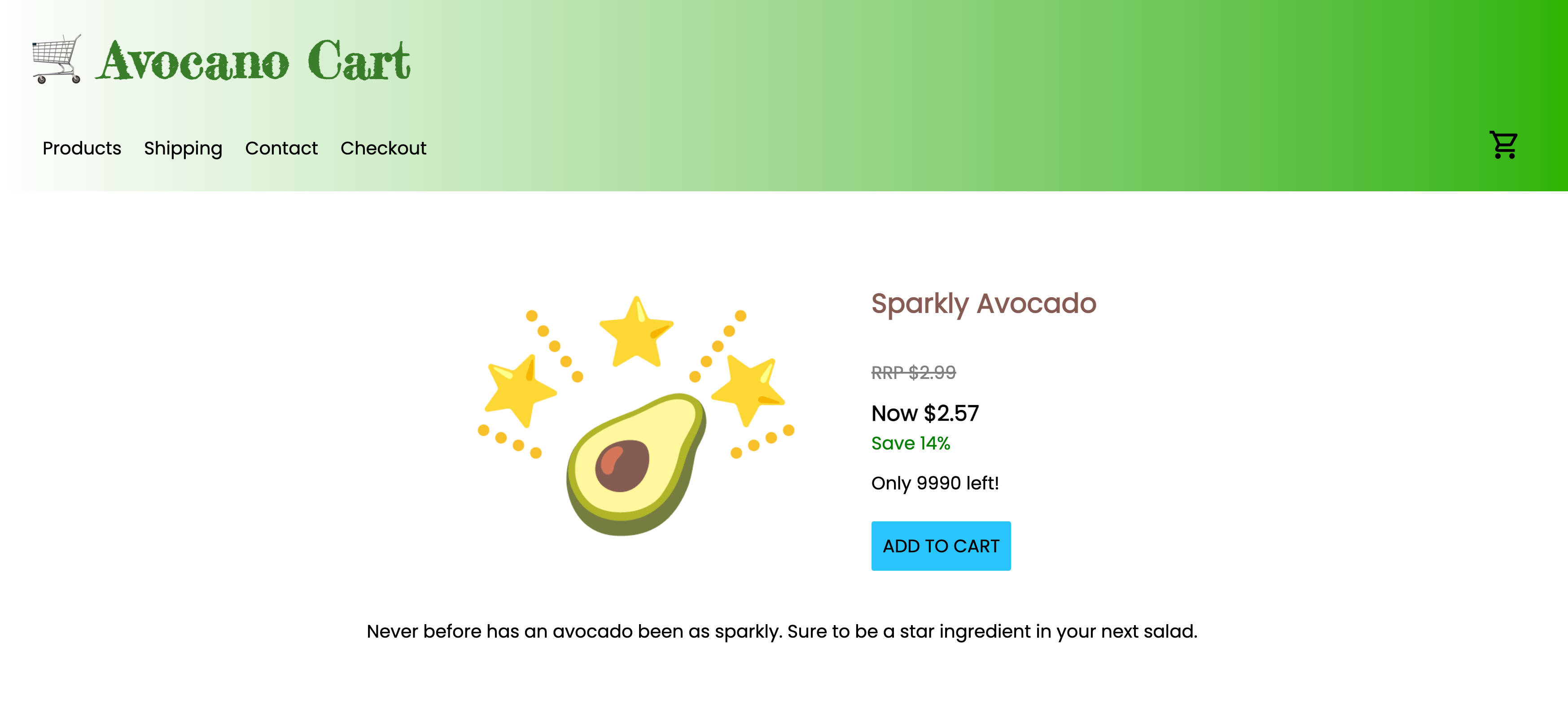
Explore the frontend
To launch the frontend of your solution deployment:
- Open the Firebase console.
- Select your existing project.
- Navigate to the Build > Hosting section.
- Select the Domain ending with web.app. The frontend of your sample application opens in a new browser window.
You can now interact with the Avocano website just as its customers would see it, including browsing through products, adding products to the shopping cart, and checking out as a guest.
View the autoscaling and concurrency configuration
Cloud Run automatically scales up or down container instances from zero depending on traffic, to provide a fast startup time for your app.
Understand the settings for autoscaling and concurrency
It's important to understand that the settings for autoscaling and concurrency on Cloud Run can affect the performance and costs for your app:
Minimum instances: You can set the minimum instances setting to enable idle instances for your service. By raising the minimum instances setting in anticipation of higher traffic, you can minimize response time for the first N users. If your service requires reduced latency, especially when scaling from zero active instances, you can specify a minimum number of container instances to be kept warm and ready to serve requests.
Maximum instances: Increasing the maximum instances setting in Cloud Run can help you to serve exceptionally high traffic that's anticipated. In such a scenario, you should also evaluate your current quota and consider requesting an increase. Reducing the maximum instances setting can help you avoid unexpected costs or a higher utilization of underlying backing infrastructure (such as your database capacity).
Concurrency: The Cloud Run concurrency setting specifies the maximum number of requests that can be processed simultaneously by a given container instance. Optimizing the memory, CPU, and concurrency for your application's behavior ensures that each container instance has the best utilization, and minimizes the need to scale up to new instances. For more information, see Optimize concurrency.
View autoscaling and concurrency settings
To view the current minimum and maximum instances settings, and concurrency settings for your Cloud Run service:
- Go to Cloud Run
- Click the service you are interested in to open the Service details page.
- Click the Revisions tab.
- In the details panel at the right, the current minimum instances, maximum instances, and concurrency settings are listed under the Container tab.
If you want to learn how to adjust these settings to optimize app performance, see the General development tips in the Cloud Run documentation.
View traffic logs
You can use the logging tools in Cloud Run to keep watch on traffic to your app and get alerts when problems arise.
To view logs for your Cloud Run service:
- Go to Cloud Run
- Click the chosen service in the displayed list.
- Click the Logs tab to get the request and container logs for all revisions of this service. You can filter by log severity level.
Cloud Run automatically captures logs from many places:
anything written to standard out and standard error, anything in /var/log/, and others.
Any manual logging done with the Cloud Logging libraries
is also captured.
You can also view the logs for this service directly in Cloud Logging by
clicking View in Logs Explorer.
In the Avocano app, try the following user actions to trigger corresponding output that you can view in the logs.
| User action | Log output |
|---|---|
| Purchase the shopping cart using Collect as the payment type and the product amount in the cart does not exceed the inventory count. | The log output shows an info log, with
httpRequest status of 200. |
| Purchase the shopping cart using Collect as the payment type but the product amount in the cart exceeds the inventory count. | The log output shows a Warning log, with httpRequest
status of 400. |
| Purchase the shopping cart using Credit as the payment type. | The log output shows an Error log, with httpRequest
status of 501. |
You can view the code that raises the error that leads to the 400/501
HTTP response in the serializers.py
file. Cloud Run notes the response, and generates a corresponding
request log entry.
You can use log-based alerts to notify you whenever a specific message appears in your included logs.
View trace instrumentation and captured traces
This solution uses Open Telemetry Python automatic instrumentation to capture telemetry data for the Avocano application.
Understand how tracing is implemented
The solution implements the following code and configuration settings in order to generate traces using automatic instrumentation:
- Add dependencies for Cloud Trace in the
requirements.txt
file, including the following:
opentelemetry-distro: installs the Open Telemetry API, SDK, and command-line tools.opentelemetry-instrumentation: adds support for Python auto-instrumentation.opentelemetry-exporter-gcp-trace: provides support for exporting traces to Cloud Trace.opentelemetry-resource-detector: provides support for detecting Google Cloud resources.opentelemetry-instrumentation-django: allow tracing requests for Django application.
- Set the IAM binding in the
iam.tffile to enable the server to write to Cloud Trace. - Configure the
OTEL_TRACES_EXPORTERenvironment variable in theservices.tffile to use the exporter for Cloud Trace. - In the
server/Procfile, configure the server to run theopentelemetry-instrumentcommand on the Avocano app. This command detects packages in Avocano and applies automatic tracing instrumentation on them, if possible.
To learn more about collecting Cloud Trace data for Python, see Python and OpenTelemetry.
View the latency data
To view the latency data for requests, follow these steps:
- Go to Cloud Trace
- In the Select a trace section of the Trace list page, click the blue dot, which represents a captured trace. The Latency column displays the latency for the captured traces.
You can also view trace data using the following visualizations in the Trace list page:
- Waterfall graph: represents a complete request through the application. Each step in the timeline is a span, which you can click to view details. Cloud Run automatically creates spans for internal operations, such as request handling and load balancing. These spans appear in the same waterfall graph as spans produced by Avocano, allowing you to view the full lifetime of the request.
- Span details: shows any labels or annotations you added to the app's code when you instrumented it for tracing.
If you want to add customized traces, refer to Manual Instrumentation in the Open Telemetry documentation.
Design recommendations
This section provides recommendations for using the Ecommerce platform with serverless computing solution to develop an architecture that meets your requirements for security, reliability, cost, and performance.
To view the design recommendations for each area, click the appropriate tab.
Enhance security
| Design focus | Recommendations |
|---|---|
| Data encryption |
By default, Cloud Run encrypts data by using a Google-owned and Google-managed encryption key. To protect your containers by using a key that you control, you can use customer managed encryption keys. For more information, see Using customer-managed encryption keys. |
| Software supply-chain security | To ensure that only authorized container images are deployed to the Cloud Run services, you can use Binary Authorization. |
Improve reliability
| Design focus | Recommendations |
|---|---|
| App scaling | The Cloud Run services in the solution are configured to autoscale the container instances horizontally based on the request load. Review and adjust the autoscaling parameters based on your requirements. For more information, see About container instance autoscaling. |
| Request handling | To improve the responsiveness of Cloud Run services that store client-specific state on container instances, you can use session affinity. Requests from the same client are routed to the same container instance, on a best-effort basis. For more information, see Setting session affinity (services). |
| Data durability | To protect your data against loss, you can use automated backups of the Cloud SQL database. For more information, see About Cloud SQL backups. |
| Database high availability (HA) | The Cloud SQL database in the solution is deployed in a single zone. For HA, you can use a multi-zone configuration. For more information, see About high availability. If database HA is a critical requirement, AlloyDB for PostgreSQL is an alternative Google Cloud service that you can consider. |
| Database reliability | The Cloud SQL instance in this solution uses the
A Cloud SQL instance that uses the |
| Quotas and limits | The number of Cloud Run resources is limited. If you anticipate a surge in traffic, for example due to a seasonal or sales event, you should request a quota increase. For more information, see How to increase quota. Some quota requests require manual approval, so you should plan ahead. You can also set alerts on your progress towards reaching your quota. |
Optimize cost
| Design focus | Recommendations |
|---|---|
| Resource efficiency | Cloud Run determines the number of requests that should be sent to a container instance based on CPU usage and memory usage. By increasing the maximum concurrency setting, you can reduce the number of container instances that Cloud Run needs to create, and therefore reduce cost. For more information, see Maximum concurrent requests per instance (services). The Cloud Run services in this solution are configured to allocate CPUs only during request processing. When a Cloud Run service finishes handling a request, the container instance's access to CPUs is disabled. For information about the cost and performance effect of this configuration, see CPU allocation (services). |
Improve performance
| Design focus | Recommendations |
|---|---|
| App startup time | To reduce the performance effect of cold starts, you can configure the minimum number of Cloud Run container instances to a non-zero value. For more information, see General development tips for Cloud Run. |
| Tune concurrency | This solution is tuned to maximize individual container throughput. Cloud Run automatically adjusts the concurrency for serving multiple requests. However, you should adjust the default maximum concurrency if your container is not able to process many concurrent requests, or if your container is able to handle a larger volume of requests. For more information, see Optimize concurrency. |
| Database performance | For performance-sensitive applications, you can improve performance of Cloud SQL by using a larger machine type and by increasing the storage capacity. If database performance is a critical requirement, AlloyDB for PostgreSQL is an alternative Google Cloud service that you can consider. |
Note the following:
- Before you make any design changes, assess the cost impact and consider potential trade-offs with other features. You can assess the cost impact of design changes by using the Google Cloud Pricing Calculator.
- To implement design changes in the solution, you need expertise in Terraform coding and advanced knowledge of the Google Cloud services that are used in the solution.
- If you modify the Google-provided Terraform configuration and if you then experience errors, create issues in GitHub. GitHub issues are reviewed on a best-effort basis and are not intended for general usage questions.
- For more information about designing and setting up production-grade environments in Google Cloud, see Landing zone design in Google Cloud and Google Cloud setup checklist.
Delete the solution deployment
When you no longer need the solution deployment, to avoid continued billing for the resources that you created, delete the deployment.
Delete through the console
Use this procedure if you deployed the solution through the console.
In the Google Cloud console, go to the Solution deployments page.
Select the project that contains the deployment that you want to delete.
Locate the deployment that you want to delete.
In the row for the deployment, click Actions and then select Delete.
You might need to scroll to see Actions in the row.
Enter the name of the deployment and then click Confirm.
The Status field shows Deleting.
If the deletion fails, see the troubleshooting guidance in Error when deleting a deployment.
When you no longer need the Google Cloud project that you used for the solution, you can delete the project. For more information, see Optional: Delete the project.
Delete using the Terraform CLI
Use this procedure if you deployed the solution by using the Terraform CLI.
In Cloud Shell, make sure that the current working directory is
$HOME/cloudshell_open/terraform-dynamic-python-webapp/infra. If it isn't, go to that directory.Remove the resources that were provisioned by Terraform:
terraform destroyTerraform displays a list of the resources that will be destroyed.
When you're prompted to perform the actions, enter
yes.Terraform displays messages showing the progress. After all the resources are deleted, Terraform displays the following message:
Destroy complete!If the deletion fails, see the troubleshooting guidance in Error when deleting a deployment.
When you no longer need the Google Cloud project that you used for the solution, you can delete the project. For more information, see Optional: Delete the project.
Optional: Delete the project
If you deployed the solution in a new Google Cloud project, and if you no longer need the project, then delete it by completing the following steps:
- In the Google Cloud console, go to the Manage resources page.
- In the project list, select the project that you want to delete, and then click Delete.
- At the prompt, type the project ID, and then click Shut down.
If you decide to retain the project, then delete the service account that was created for this solution, as described in the next section.
Optional: Delete the service account
If you deleted the project that you used for the solution, then skip this section.
As mentioned earlier in this guide, when you deployed the solution, a service account was created on your behalf. The service account was assigned certain IAM permissions temporarily; that is, the permissions were revoked automatically after the solution deployment and deletion operations were completed, but the service account isn't deleted. Google recommends that you delete this service account.
If you deployed the solution through the Google Cloud console, go to the Solution deployments page. (If you're already on that page, refresh the browser.) A process is triggered in the background to delete the service account. No further action is necessary.
If you deployed the solution by using the Terraform CLI, complete the following steps:
In the Google Cloud console, go to the Service accounts page.
Select the project that you used for the solution.
Select the service account that you want to delete.
The email ID of the service account that was created for the solution is in the following format:
goog-sc-DEPLOYMENT_NAME-NNN@PROJECT_ID.iam.gserviceaccount.comThe email ID contains the following values:
- DEPLOYMENT_NAME: the name of the deployment.
- NNN: a random 3-digit number.
- PROJECT_ID: the ID of the project in which you deployed the solution.
Click Delete.
Troubleshoot errors
The actions that you can take to diagnose and resolve errors depend on the deployment method and the complexity of the error.
Errors when deploying through the console
If the deployment fails when you use the console, do the following:
Go to the Solution deployments page.
If the deployment failed, the Status field shows Failed.
View the details of the errors that caused the failure:
In the row for the deployment, click Actions.
You might need to scroll to see Actions in the row.
Select View Cloud Build logs.
Review the Cloud Build log and take appropriate action to resolve the issue that caused the failure.
Errors when deploying using the Terraform CLI
If the deployment fails when you use Terraform, the output of the terraform
apply command includes error messages that you can review to diagnose the
problem.
The examples in the following sections show deployment errors that you might encounter when you use Terraform.
API not enabled error
If you create a project and then immediately attempt to deploy the solution in the new project, the deployment might fail with an error like the following:
Error: Error creating Network: googleapi: Error 403: Compute Engine API has not
been used in project PROJECT_ID before or it is disabled. Enable it by visiting
https://console.developers.google.com/apis/api/compute.googleapis.com/overview?project=PROJECT_ID
then retry. If you enabled this API recently, wait a few minutes for the action
to propagate to our systems and retry.
If this error occurs, wait a few minutes and then run the terraform apply
command again.
Cannot assign requested address error
When you run the terraform apply command, a cannot assign requested address
error might occur, with a message like the following:
Error: Error creating service account:
Post "https://iam.googleapis.com/v1/projects/PROJECT_ID/serviceAccounts:
dial tcp [2001:db8:ffff:ffff::5f]:443:
connect: cannot assign requested address
If this error occurs, run the terraform apply command again.
Error when deleting a deployment
In certain cases, attempts to delete a deployment might fail:
- After deploying a solution through the console, if you change any resource that was provisioned by the solution, and if you then try to delete the deployment, the deletion might fail. The Status field on the Solution deployments page shows Failed, and the Cloud Build log shows the cause of the error.
- After deploying a solution by using the Terraform CLI, if you change any
resource by using a non-Terraform interface (for example,
the console), and if you then try to delete the deployment,
the deletion might fail. The messages in the output of the
terraform destroycommand show the cause of the error.
Review the error logs and messages, identify and delete the resources that caused the error, and then try deleting the deployment again.
If a console-based deployment doesn't get deleted and if you can't diagnose the error by using the Cloud Build log, then you can delete the deployment by using the Terraform CLI, as described in the next section.
Delete a console-based deployment by using the Terraform CLI
This section describes how to delete a console-based deployment if errors occur when you try to delete it through the console. In this approach, you download the Terraform configuration for the deployment that you want to delete and then use the Terraform CLI to delete the deployment.
Identify the region where the deployment's Terraform code, logs, and other data are stored. This region might be different from the region that you selected while deploying the solution.
In the Google Cloud console, go to the Solution deployments page.
Select the project that contains the deployment that you want to delete.
In the list of deployments, identify the row for the deployment that you want to delete.
Click View all row content.
In the Location column, note the second location, as highlighted in the following example:
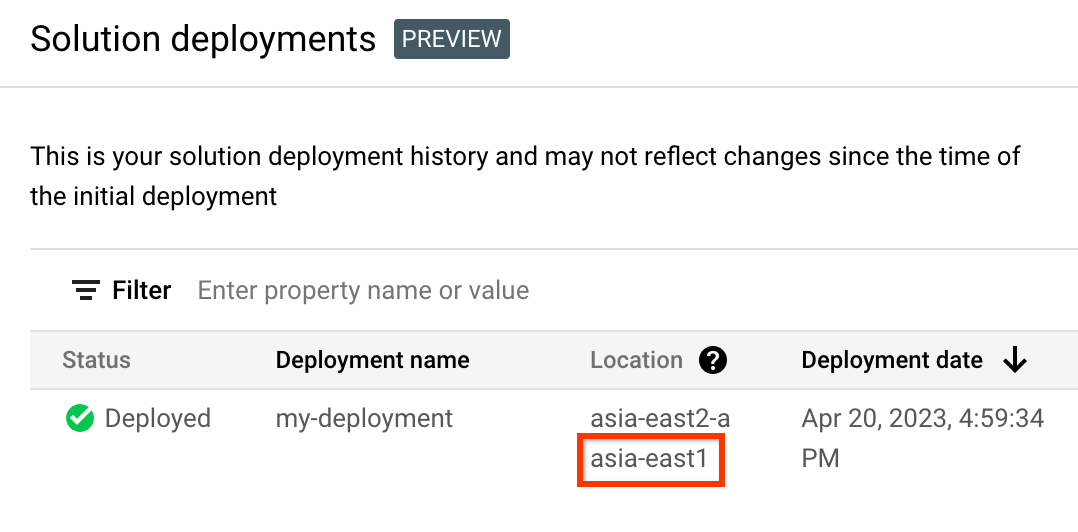
In the Google Cloud console, activate Cloud Shell.
At the bottom of the Google Cloud console, a Cloud Shell session starts and displays a command-line prompt. Cloud Shell is a shell environment with the Google Cloud CLI already installed and with values already set for your current project. It can take a few seconds for the session to initialize.
Create environment variables for the project ID, region, and name of the deployment that you want to delete:
export REGION="REGION" export PROJECT_ID="PROJECT_ID" export DEPLOYMENT_NAME="DEPLOYMENT_NAME"In these commands, replace the following:
- REGION: the location that you noted earlier in this procedure.
- PROJECT_ID: the ID of the project where you deployed the solution.
- DEPLOYMENT_NAME: the name of the deployment that you want to delete.
Get the ID of the latest revision of the deployment that you want to delete:
export REVISION_ID=$(curl \ -H "Authorization: Bearer $(gcloud auth print-access-token)" \ -H "Content-Type: application/json" \ "https://config.googleapis.com/v1alpha2/projects/${PROJECT_ID}/locations/${REGION}/deployments/${DEPLOYMENT_NAME}" \ | jq .latestRevision -r) echo $REVISION_IDThe output is similar to the following:
projects/PROJECT_ID/locations/REGION/deployments/DEPLOYMENT_NAME/revisions/r-0Get the Cloud Storage location of the Terraform configuration for the deployment:
export CONTENT_PATH=$(curl \ -H "Authorization: Bearer $(gcloud auth print-access-token)" \ -H "Content-Type: application/json" \ "https://config.googleapis.com/v1alpha2/${REVISION_ID}" \ | jq .applyResults.content -r) echo $CONTENT_PATHThe following is an example of the output of this command:
gs://PROJECT_ID-REGION-blueprint-config/DEPLOYMENT_NAME/r-0/apply_results/contentDownload the Terraform configuration from Cloud Storage to Cloud Shell:
gcloud storage cp $CONTENT_PATH $HOME --recursive cd $HOME/content/infraWait until the
Operation completedmessage is displayed, as shown in the following example:Operation completed over 45 objects/268.5 KiBInitialize Terraform:
terraform initWait until you see the following message:
Terraform has been successfully initialized!Remove the deployed resources:
terraform destroyTerraform displays a list of the resources that will be destroyed.
If any warnings about undeclared variables are displayed, ignore the warnings.
When you're prompted to perform the actions, enter
yes.Terraform displays messages showing the progress. After all the resources are deleted, Terraform displays the following message:
Destroy complete!Delete the deployment artifact:
curl -X DELETE \ -H "Authorization: Bearer $(gcloud auth print-access-token)" \ -H "Content-Type: application/json" \ "https://config.googleapis.com/v1alpha2/projects/${PROJECT_ID}/locations/${REGION}/deployments/${DEPLOYMENT_NAME}?force=true&delete_policy=abandon"Wait a few seconds and then verify that the deployment artifact was deleted:
curl -H "Authorization: Bearer $(gcloud auth print-access-token)" \ -H "Content-Type: application/json" \ "https://config.googleapis.com/v1alpha2/projects/${PROJECT_ID}/locations/${REGION}/deployments/${DEPLOYMENT_NAME}" \ | jq .error.messageIf the output shows
null, wait a few seconds and then run the command again.After the deployment artifact is deleted, a message as shown in the following example is displayed:
Resource 'projects/PROJECT_ID/locations/REGION/deployments/DEPLOYMENT_NAME' was not found
Submit feedback
Jump Start Solutions are for informational purposes only and are not officially supported products. Google may change or remove solutions without notice.
To troubleshoot errors, review the Cloud Build logs and the Terraform output.
To submit feedback, do the following:
- For documentation, in-console tutorials, or the solution, use the Send Feedback button on the page.
For unmodified code, create issues in the appropriate GitHub repository:
GitHub issues are reviewed on a best-effort basis and are not intended for general usage questions.
- For issues with the products that are used in the solution, contact Cloud Customer Care.
What's next
This solution demonstrates how to deploy an ecommerce web application using Cloud Run. To continue learning more about Google Cloud products and capabilities, see:
- General development tips for Cloud Run.
- Load testing best practices for Cloud Run.
- End user authentication for Cloud Run tutorial.
- Serve dynamic content and host microservices using Firebase Hosting.

