Konektivitas ke layanan yang dihosting di lingkungan serverless
Halaman ini menjelaskan cara mengonfigurasi Konektor Integrasi untuk terhubung ke layanan yang dihosting di lingkungan serverless seperti Cloud Run di Google Cloud.
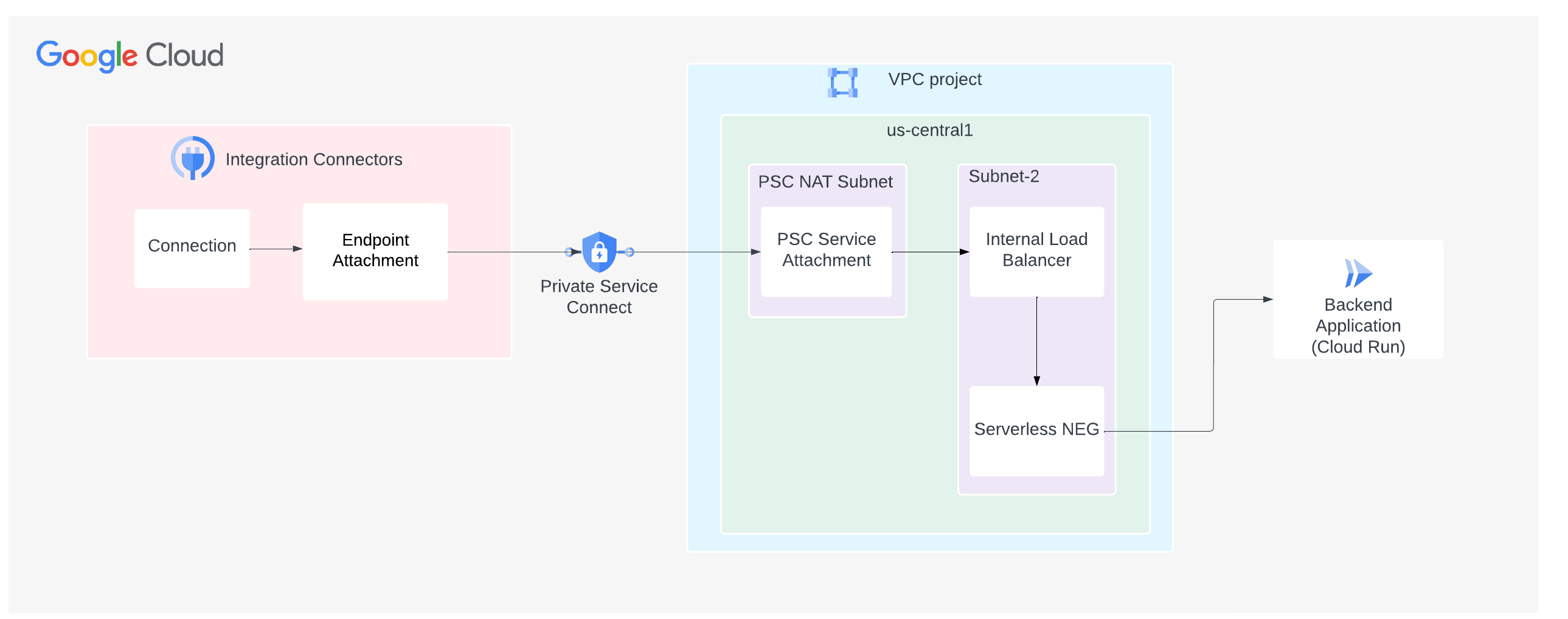
Gambar berikut menunjukkan penyiapan konektivitas jaringan pribadi dari Konektor Integrasi ke layanan yang dihosting di lingkungan Cloud Run di Google Cloud:
Halaman ini mengasumsikan bahwa Anda sudah memahami konsep berikut:
Pertimbangan
Saat Anda membuat lampiran layanan PSC, pertimbangkan poin-poin penting berikut:
- Lampiran layanan PSC dan load balancer dibuat di subnet yang berbeda dalam VPC yang sama. Secara khusus, lampiran layanan selalu dibuat di subnet NAT.
- Traffic dari load balancer dan probe health check harus dikirim ke port yang sama.
- Konfigurasikan aturan firewall untuk memfasilitasi aliran traffic.
Aturan traffic masuk
Traffic dari subnet lampiran layanan PSC harus menjangkau layanan backend Anda.
Aturan traffic keluar
Traffic keluar diaktifkan secara default di project Google Cloud, kecuali jika aturan penolakan tertentu dikonfigurasi.
- Semua komponen Google Cloud Anda seperti lampiran layanan PSC dan load balancer harus berada di region yang sama.
Membuat lampiran layanan PSC
Untuk membuat konektivitas pribadi dari Integration Connectors, layanan Anda harus diekspos ke Integration Connectors menggunakan lampiran layanan PSC. Lampiran layanan selalu menggunakan load balancer. Oleh karena itu, jika layanan Anda tidak berada di balik load balancer, load balancer harus dikonfigurasi.
- Buat load balancer. Jika sudah memiliki load balancer, lewati langkah ini.
Buat load balancer aplikasi menggunakan NEG serverless sebagai backend dengan mengikuti petunjuk di Menyiapkan Load Balancer Aplikasi internal regional dengan Cloud Run.
- Membuat lampiran layanan
- Buat subnet untuk PSC NAT. Perintah berikut membuat subnet dengan nama
psc-nat-subnet1dan tujuannya adalahPRIVATE_SERVICE_CONNECT.gcloud compute networks subnets create psc-nat-subnet1 \ --network=VPC_NETWORK --range=SUBNET_RANGE_1 \ --purpose=PRIVATE_SERVICE_CONNECT - Buat aturan firewall untuk mengizinkan traffic dari NAT PSC ke load balancer.
gcloud compute network-firewall-policies rules create PRIORITY --firewall-policy FIREWALL_POLICY_NAME_SA \ --direction=INGRESS --network=VPC_NETWORK \ --action=allow --allow=tcp:BACKEND_SERVER_PORT --src-ip-ranges=SUBNET_RANGE_1
- Buat lampiran layanan dengan persetujuan eksplisit.
gcloud compute service-attachments create SERVICE_ATTACHMENT_NAME --producer-forwarding-rule=FORWARDING_RULE_NAME --connection-preference=ACCEPT_MANUAL --consumer-accept-list=SERVICE_DIRECTORY_PROJECT_ID=LIMIT --nat-subnets=psc-nat-subnet1
Dalam perintah ini, LIMIT adalah batas koneksi untuk project. Batas koneksi adalah jumlah endpoint PSC konsumen yang dapat terhubung ke layanan ini. Untuk mendapatkan SERVICE_DIRECTORY_PROJECT_ID, lakukan langkah berikut:
-
Anda dapat membuat lampiran layanan PSC sehingga hanya menerima permintaan dari project Google Cloud yang ditentukan. Namun, untuk melakukannya, Anda memerlukan project ID direktori layanan yang terkait dengan project Google Cloud Anda. Untuk mendapatkan project ID direktori layanan, Anda dapat menggunakan List Connections API seperti yang ditunjukkan dalam contoh berikut.
Sintaks
curl -X GET \ -H "authorization: Bearer $(gcloud auth print-access-token)" \ -H "Content-Type: application/json" \ "https://connectors.googleapis.com/v1/projects/CONNECTORS_PROJECT_ID/locations/-/connections"
Ganti kode berikut:
- CONNECTORS_PROJECT_ID: ID project Google Cloud tempat Anda membuat koneksi.
Contoh
Contoh ini mendapatkan project ID direktori layanan untuk project Google Cloud
connectors-test.curl -X GET \ -H "authorization: Bearer $(gcloud auth print-access-token)" \ -H "Content-Type: application/json" \ "https://connectors.googleapis.com/v1/projects/connectors-test/locations/-/connections"
Menjalankan perintah ini di terminal akan menampilkan output yang mirip dengan berikut:
..... { "connections": [ { "name": "projects/connectors-test/locations/asia-northeast1/connections/big-query-iam-invalid-sa", "createTime": "2022-10-07T09:02:31.905048520Z", "updateTime": "2022-10-07T09:22:39.993778690Z", "connectorVersion": "projects/connectors-test/locations/global/providers/gcp/connectors/bigquery/versions/1", "status": { "state": "ACTIVE" }, "configVariables": [ { "key": "project_id", "stringValue": "connectors-test" }, { "key": "dataset_id", "stringValue": "testDataset" } ], "authConfig": {}, "serviceAccount": "564332356444-compute@", "serviceDirectory": "projects/abcdefghijk-tp/locations/asia-northeast1/namespaces/connectors/services/runtime", "nodeConfig": { "minNodeCount": 2, "maxNodeCount": 50 } }, ....Pada contoh output, untuk project Google Cloud
connectors-test, project ID direktori layanan adalahabcdefghijk-tp.
-
- Buat subnet untuk PSC NAT. Perintah berikut membuat subnet dengan nama
Membuat lampiran endpoint untuk menggunakan lampiran layanan PSC
Lampiran endpoint sebagai alamat IPUntuk petunjuk cara membuat lampiran endpoint sebagai alamat IP, lihat Membuat lampiran endpoint sebagai alamat IP.
Lampiran endpoint sebagai nama hostDalam kasus tertentu seperti backend yang mengaktifkan TLS, tujuan mengharuskan Anda menggunakan nama host, bukan IP pribadi, untuk melakukan validasi TLS. Jika DNS pribadi digunakan, bukan alamat IP untuk tujuan host, selain membuat lampiran endpoint sebagai alamat IP, Anda juga harus mengonfigurasi zona terkelola. Untuk petunjuk cara membuat lampiran endpoint sebagai nama host, lihat Membuat lampiran endpoint sebagai nama host.
Kemudian, saat mengonfigurasi koneksi untuk menggunakan lampiran endpoint, Anda dapat memilih lampiran endpoint ini.
Mengonfigurasi koneksi untuk menggunakan lampiran endpoint
Setelah membuat lampiran endpoint, gunakan lampiran endpoint di koneksi Anda. Saat Anda membuat koneksi baru atau memperbarui koneksi yang ada, di bagian Tujuan, pilih Lampiran endpoint sebagai Jenis Tujuan dan pilih lampiran endpoint yang Anda buat dari daftar Lampiran Endpoint.
Jika Anda membuat zona terkelola, pilih Host Address sebagai Destination Type dan gunakan A-record yang Anda buat saat membuat zona terkelola.
Tips pemecahan masalah
Ikuti panduan yang tercantum di bagian ini untuk menghindari masalah umum:
- Untuk memverifikasi bahwa lampiran endpoint disiapkan dengan benar dan koneksi PSC dibuat, periksa status koneksi. Untuk informasi selengkapnya, lihat Memverifikasi koneksi lampiran endpoint.
- Untuk informasi tentang cara memecahkan masalah Load Balancer, lihat Memecahkan masalah terkait Load Balancer Aplikasi internal.
- Uji Konektivitas Google Cloud dapat digunakan untuk mengidentifikasi kesenjangan dalam konfigurasi jaringan Anda. Untuk mengetahui informasi selengkapnya, lihat Membuat dan menjalankan Uji Konektivitas.