Konektivitas pribadi untuk penyedia cloud lokal atau lainnya
Halaman ini menjelaskan cara menyiapkan konektivitas pribadi dari Konektor Integrasi ke layanan backend Anda seperti MySQL, Postgres, dan SQL Server yang dihosting di pusat data on-premise atau penyedia cloud lainnya.
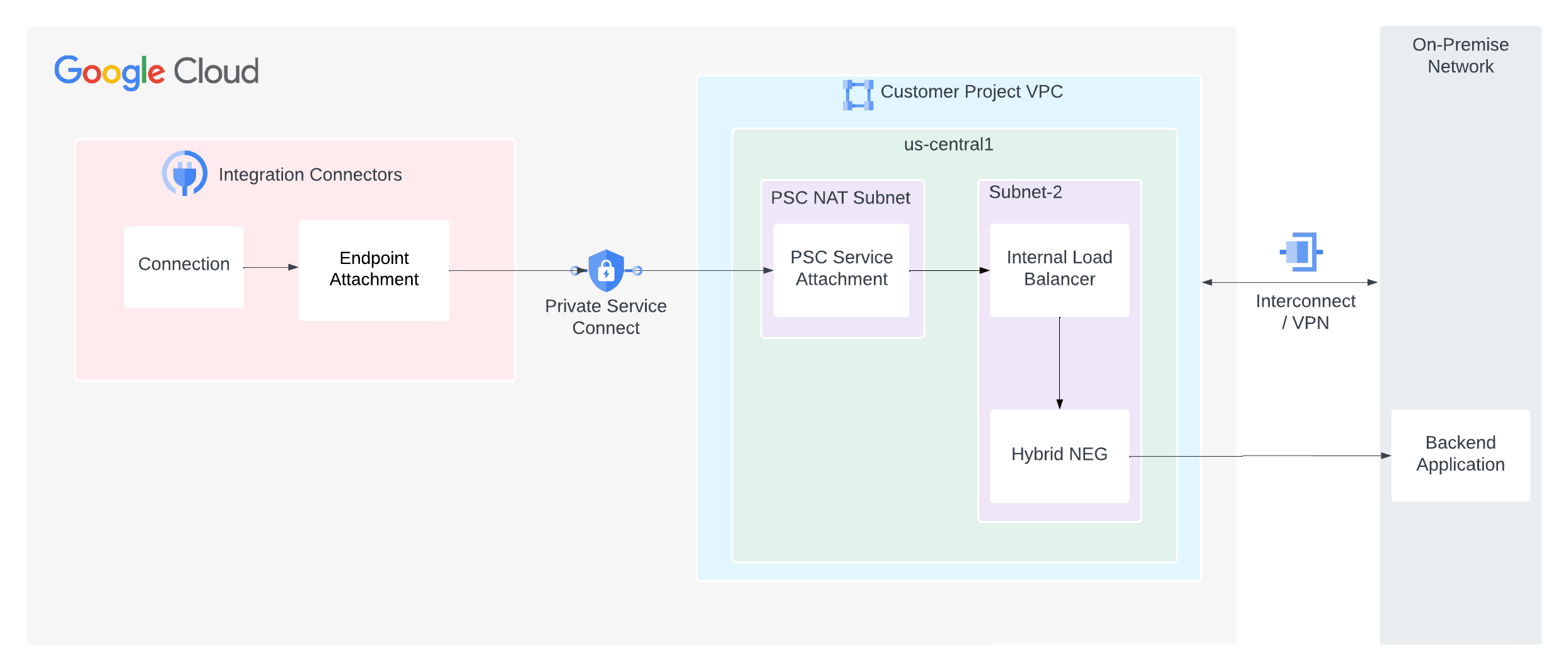
Gambar berikut menunjukkan penyiapan konektivitas jaringan pribadi dari Integration Connectors ke layanan backend yang dihosting di jaringan lokal Anda.
Halaman ini mengasumsikan bahwa Anda sudah memahami konsep berikut:
Pertimbangan
Saat Anda membuat lampiran layanan PSC, pertimbangkan poin-poin penting berikut:
- Sebagai produsen layanan, Anda harus mengonfigurasi lampiran layanan PSC yang dapat digunakan Konektor Integrasi untuk menggunakan layanan. Setelah lampiran layanan siap, Anda dapat mengonfigurasi koneksi untuk menggunakan lampiran layanan menggunakan lampiran endpoint.
- Lampiran layanan PSC dan load balancer harus berada di subnet yang berbeda dalam VPC yang sama. Dan secara khusus, lampiran layanan harus berada dalam subnet NAT.
- Software yang berjalan di VM backend Anda harus merespons traffic load-balanced dan probe health check yang dikirim ke setiap alamat IP aturan penerusan (software harus memproses di
0.0.0.0:<port>, bukan di alamat IP tertentu yang ditetapkan ke antarmuka jaringan). Untuk mengetahui informasi selengkapnya, lihat Health check. - Konfigurasikan aturan firewall untuk memfasilitasi aliran traffic.
Aturan traffic masuk
- Traffic dari subnet lampiran layanan PSC harus menjangkau subnet ILB.
- Dalam subnet ILB, ILB harus dapat mengirim traffic ke sistem backend Anda.
- Pemeriksaan health check harus dapat mengakses sistem backend Anda. Penguji
health check Google Cloud memiliki rentang IP tetap (
35.191.0.0/16, 130.211.0.0/22). Jadi, IP ini dapat diizinkan untuk mengirim traffic ke server backend Anda.
Aturan traffic keluar
Traffic keluar diaktifkan secara default di project Google Cloud, kecuali jika aturan penolakan tertentu dikonfigurasi.
- Semua komponen Google Cloud Anda seperti lampiran layanan PSC dan load balancer harus berada di region yang sama.
Sistem backend Anda tidak boleh terbuka untuk jaringan publik, karena hal ini dapat menjadi masalah keamanan. Namun, pastikan sistem backend Anda menerima traffic dalam skenario berikut:
Load balancer berbasis proxy/HTTP(s) (ILB proxy L4, ILB L7): Semua permintaan baru berasal dari load balancer. Oleh karena itu, backend Anda harus menerima permintaan dari subnet proxy jaringan VPC Anda. Untuk informasi selengkapnya, lihat Subnet khusus proxy untuk load balancer berbasis Envoy.
Mengonfigurasi konektivitas pribadi
Untuk mengonfigurasi konektivitas pribadi, lakukan tugas berikut:
- Buat lampiran layanan PSC.
- Buat lampiran endpoint untuk menggunakan lampiran layanan PSC.
- Konfigurasikan koneksi Anda untuk menggunakan lampiran endpoint.
Membuat lampiran layanan PSC
Untuk membuat konektivitas pribadi dari konektor Integrasi, Anda harus mengekspos layanan ke Konektor Integrasi menggunakan lampiran layanan PSC. Lampiran layanan selalu menargetkan load balancer. Oleh karena itu, jika layanan Anda tidak berada di balik load balancer, load balancer harus dikonfigurasi.
Untuk membuat lampiran layanan PSC, lakukan langkah berikut:- Buat probe health check, lalu buat load balancer. Untuk mengetahui informasi tentang cara menyiapkan Load Balancer Jaringan proxy internal regional, lihat Menyiapkan Load Balancer Jaringan proxy internal regional dengan konektivitas campuran.
- Buat lampiran layanan di region yang sama dengan load balancer layanan. Untuk mengetahui informasi tentang cara membuat lampiran layanan, lihat Memublikasikan layanan.
Membuat lampiran endpoint
Lampiran endpoint sebagai alamat IPUntuk petunjuk cara membuat lampiran endpoint sebagai alamat IP, lihat Membuat lampiran endpoint sebagai alamat IP.
Lampiran endpoint sebagai nama hostDalam kasus tertentu seperti backend yang mengaktifkan TLS, tujuan mengharuskan Anda menggunakan nama host, bukan IP pribadi, untuk melakukan validasi TLS. Jika DNS pribadi digunakan, bukan alamat IP untuk tujuan host, selain membuat lampiran endpoint sebagai alamat IP, Anda juga harus mengonfigurasi zona terkelola. Untuk petunjuk cara membuat lampiran endpoint sebagai nama host, lihat Membuat lampiran endpoint sebagai nama host.
Kemudian, saat mengonfigurasi koneksi untuk menggunakan lampiran endpoint, Anda dapat memilih lampiran endpoint ini.
Mengonfigurasi koneksi untuk menggunakan lampiran endpoint
Setelah membuat lampiran endpoint, gunakan lampiran endpoint di koneksi Anda. Saat Anda membuat koneksi baru atau memperbarui koneksi yang ada, di bagian Tujuan, pilih Lampiran endpoint sebagai Jenis Tujuan dan pilih lampiran endpoint yang Anda buat dari daftar Lampiran Endpoint.
Jika Anda membuat zona terkelola, pilih Host Address sebagai Destination Type dan gunakan A-record yang Anda buat saat membuat zona terkelola.
Tips pemecahan masalah
Jika Anda mengalami masalah dengan konektivitas pribadi, ikuti panduan yang tercantum di bagian ini untuk menghindari masalah umum.
- Untuk memverifikasi bahwa lampiran endpoint disiapkan dengan benar dan koneksi PSC dibuat, periksa status koneksi. Untuk informasi selengkapnya, lihat Memverifikasi koneksi lampiran endpoint.
- Pastikan konfigurasi berikut untuk aturan firewall:
- Traffic dari subnet lampiran layanan PSC harus diizinkan untuk menjangkau layanan backend Anda.
- Load balancer harus dapat mengirim traffic ke sistem backend Anda. NEG hybrid hanya didukung di load balancer proxy. Permintaan dari load balancer proxy berasal dari subnet khusus proxy di region. Oleh karena itu, aturan firewall Anda perlu dikonfigurasi agar permintaan dari rentang subnet khusus proxy dapat menjangkau backend Anda.
- Pemeriksaan health check harus dapat mengakses sistem backend Anda. Pemeriksaan health check Google Cloud memiliki rentang IP tetap (35.191.0.0/16, 130.211.0.0/22). Jadi, alamat IP ini harus diizinkan untuk mengirim traffic ke server backend Anda.
- Uji Konektivitas Google Cloud dapat digunakan untuk mengidentifikasi kesenjangan dalam konfigurasi jaringan Anda. Untuk mengetahui informasi selengkapnya, lihat Membuat dan menjalankan Uji Konektivitas.
- Pastikan aturan firewall diperbarui di lingkungan cloud lokal atau cloud lainnya untuk mengizinkan traffic dari subnet khusus proxy region Google Cloud.