This page describes the roles and permissions used by Cloud Data Fusion instances with role-based access control (RBAC) enabled.
For fine-grained access enforcement at the namespace level and lower, use these data plane resources and permissions with RBAC.
Resource hierarchy
Cloud Data Fusion resources have the following resource hierarchy:
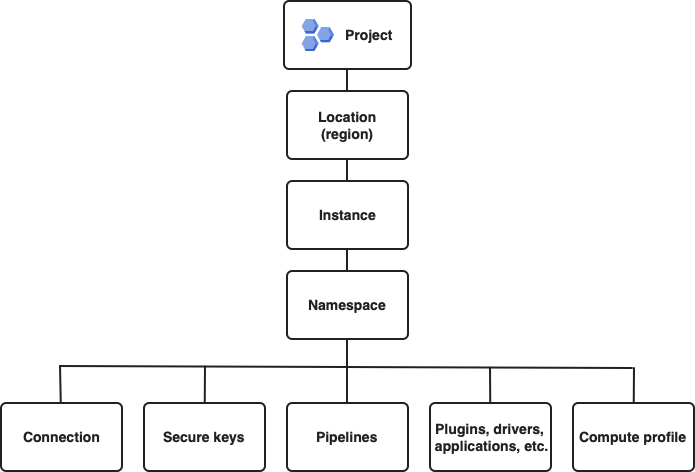
This figure shows the resource hierarchy in descending order (broadest to narrowest): Google Cloud project, location, Cloud Data Fusion instance, and namespaces. Below namespaces, in no order, are connections, secure keys, pipelines, artifacts (such as plugins, drivers, and applications), and compute profiles.
The following resources are Cloud Data Fusion data plane resources that you control with the REST API or in the Cloud Data Fusion Studio: namespaces, connections, secure keys, pipelines, artifacts, and compute profiles.
Predefined roles for RBAC
Cloud Data Fusion RBAC includes several predefined roles that you can use:
- Instance Access role (
datafusion.accessor) - Grants the principal access to a Cloud Data Fusion instance, but not to any resources within the instance. Use this role in combination with other namespace-specific roles to provide fine-grained access to namespace.
- Viewer role (
datafusion.viewer) - Grants access to a principal on a namespace to view pipelines, but not to author or run pipelines.
- Operator role (
datafusion.operator) - Grants access to a principal on a namespace to access and run pipelines, change the compute profile, create compute profiles, or upload artifacts. Can perform the same actions as a developer, with the exception of previewing pipelines.
- Developer role (
datafusion.developer) - Grants access to a principal on a namespace to create and modify limited resources, such as pipelines, within the namespace.
- Editor role (
datafusion.editor) - Grants the principal full access to all Cloud Data Fusion resources under a namespace within a Cloud Data Fusion instance. This role must be granted in addition to the Instance Accessor role to the principal. With this role, the principal can create, delete, and modify resources in the namespace.
- Instance Admin role (
datafusion.admin) - Grants access to all resources within a Cloud Data Fusion instance. Assigned through IAM. Not assigned at the namespace level through RBAC.
| Operation | datafusion.accessor | datafusion.viewer | datafusion.operator | datafusion.developer | datafusion.editor | datafusion.admin |
|---|---|---|---|---|---|---|
| Instances | ||||||
| Access instance | ||||||
| Namespaces | ||||||
| Create namespace | * | |||||
| Access namespace with explicit access granted | ||||||
| Access namespace without explicit access granted | * | |||||
| Edit namespace | ||||||
| Delete namespace | ||||||
| Namespace service account | ||||||
| Add service account | ||||||
| Edit service account | ||||||
| Remove service account | ||||||
| Use service account | ||||||
| RBAC | ||||||
| Grant or revoke permissions for other principals in the namespace | * | |||||
| Schedules | ||||||
| Create schedule | ||||||
| View schedule | ||||||
| Change schedule | ||||||
| Compute profiles | ||||||
| Create compute profiles | ||||||
| View compute profiles | ||||||
| Edit compute profiles | ||||||
| Delete compute profiles | ||||||
| Connections | ||||||
| Create connections | ||||||
| View connections | ||||||
| Edit connections | ||||||
| Delete connections | ||||||
| Use connections | ||||||
| Wrangler workspaces | ||||||
| Create workspaces | ||||||
| View workspaces | ||||||
| Edit workspaces | ||||||
| Delete workspaces | ||||||
| Use workspaces | ||||||
| Pipelines | ||||||
| Create pipelines | ||||||
| View pipelines | ||||||
| Edit pipelines | ||||||
| Delete pipelines | ||||||
| Preview pipelines | ||||||
| Deploy pipelines | ||||||
| Run pipelines | ||||||
| Secure keys | ||||||
| Create secure keys | ||||||
| View secure keys | ||||||
| Delete secure keys | ||||||
| Tags | ||||||
| Create tags | ||||||
| View tags | ||||||
| Delete tags | ||||||
| Cloud Data Fusion Hub | ||||||
| Deploy plugins | ||||||
| Source Control Management | ||||||
| Configure source control repository | ||||||
| Sync pipelines from a namespace | ||||||
| Lineage | ||||||
| View lineage | ||||||
| Logs | ||||||
| View logs | ||||||
For a complete list of permissions included in Cloud Data Fusion's predefined role, see Cloud Data Fusion predefined roles.
Custom roles for RBAC
Some use cases cannot be implemented using the predefined roles for Cloud Data Fusion. In these cases, create a custom role.
Examples
The following examples describe how to create custom roles for RBAC:
To create a custom role that only gives access to the secure keys within a namespace, create a custom role with the
datafusion.namespaces.getanddatafusion.secureKeys.*permissions.To create a custom role that gives read-only access to secure keys, create a custom role with the
datafusion.namespaces.get,datafusion.secureKeys.getSecret, anddatafusion.secureKeys.listpermissions.
Permissions for common actions
A single, predefined permission might not be sufficient to perform the
corresponding action. For example, to update namespace properties, you might
also need datafusion.namespaces.get permission. The following table describes
common actions performed within a Cloud Data Fusion instance and the
required IAM permissions:
| Action | Required Permission |
|---|---|
| Access an Instance | datafusion.instances.get |
| Create a Namespace | datafusion.namespaces.create |
| Get a Namespace | datafusion.namespaces.get |
| Update Namespace Metadata (such as properties) |
|
| Delete Namespace (Only with Unrecoverable Reset Enabled) |
|
| View Permissions on Namespace | datafusion.namespaces.getIamPolicy |
| Grant Permissions on Namespace | datafusion.namespaces.setIamPolicy |
| Pull Pipelines from Namespace SCM Configuration |
|
| Push Pipelines to SCM Repository for Namespace |
|
| Get Namespace SCM Configuration | datafusion.namespaces.get |
| Update Namespace SCM Configuration | datafusion.namespaces.updateRepositoryMetadata |
| Set a Service Account for a Namespace |
|
| Unset a Service Account for a Namespace |
|
| Provision a Service Account Credential for a Namespace | datafusion.namespaces.provisionCredential |
| View a Pipeline Draft | datafusion.namespaces.get |
| Create/Delete a Pipeline Draft |
|
| List Compute Profiles | datafusion.profiles.list |
| Create a Compute Profile | datafusion.profiles.create |
| View a Compute Profile | datafusion.profiles.get |
| Edit a Compute Profile | datafusion.profiles.update |
| Delete a Compute Profile | datafusion.profiles.delete |
| Create a Connection |
|
| View a Connection |
|
| Edit a Connection |
|
| Delete a Connection |
|
| Browse, Sample, or View Connection Specifications |
|
| Create a Wrangler Workspace |
|
| View a Wrangler Workspace |
|
| Edit or re-sample a Wrangler Workspace |
|
| Delete a Wrangler Workspace |
|
| Apply a set of directives on a Wrangler Workspace |
|
| List Pipelines |
|
| Create Pipeline |
|
| View Pipeline |
|
| Edit Pipeline |
|
| Edit Pipeline Properties |
|
| Delete Pipeline |
|
| Preview Pipeline | datafusion.pipelines.preview |
| Run Pipeline | datafusion.pipelines.execute |
| Create Schedule | datafusion.pipelines.execute |
| View Schedule |
|
| Change Schedule | datafusion.pipelines.execute |
| List Secure Keys |
|
| Create Secure Keys |
|
| View Secure Keys |
|
| Delete Secure Keys |
|
| List Artifacts* |
|
| Create an Artifact* |
|
| Get an Artifact* |
|
| Delete an Artifact* |
|
| Preferences, Tags, and Metadata | Preferences, tags, and metadata are set at the resource level for the
particular resource (datafusion.RESOURCE.update).
|
| Dataset Permissions (Deprecated) | datafusion.namespaces.update |
What's next
- Learn more about RBAC in Cloud Data Fusion.
