This page explains how to view security information about the container images you deploy. You can view this information in the Security insights side panel for Cloud Deploy in Google Cloud console.
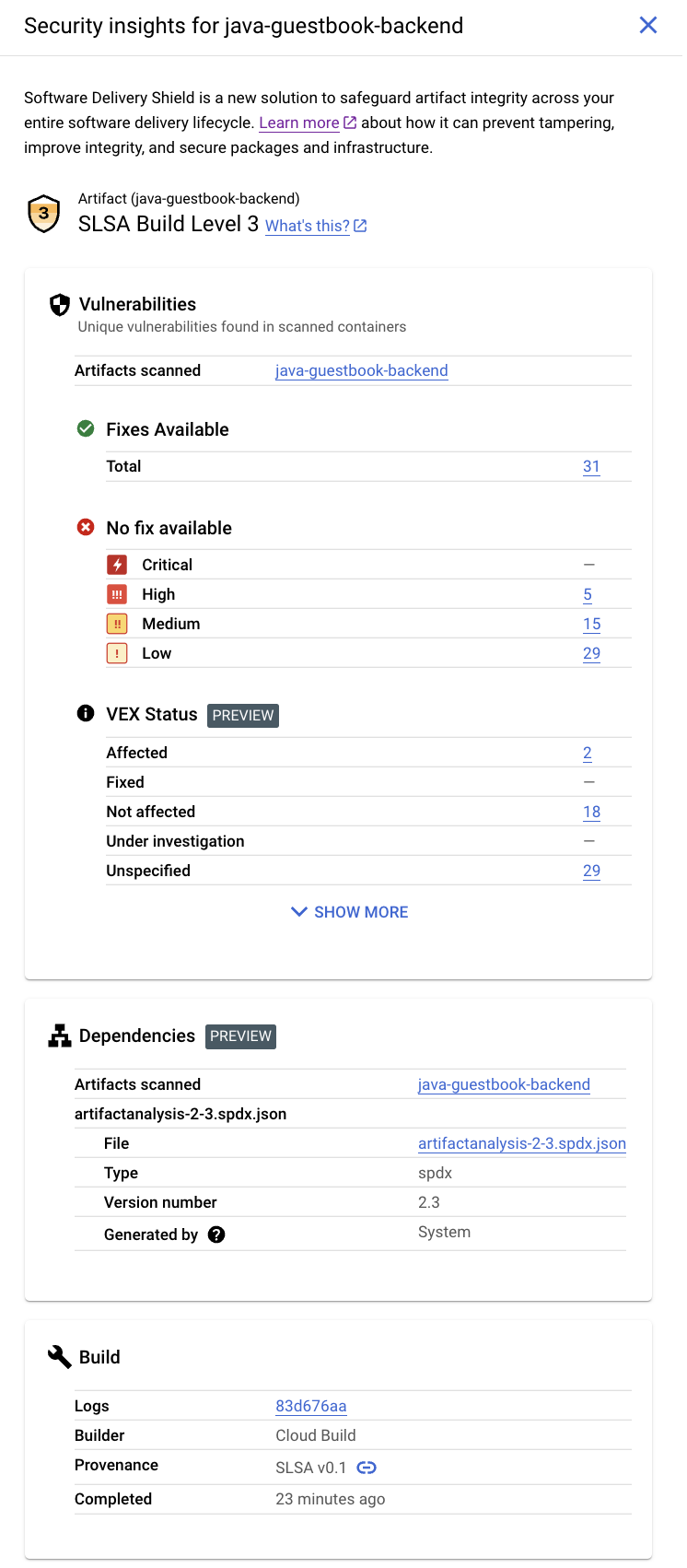
The Security insights side panel provides a high-level overview of multiple security metrics. You can use this panel to identify and mitigate risks in the images you deploy.
This panel displays the following information:
SLSA build level
Identifies the maturity level of your software build process in accordance with the Supply-chain Levels for Software Artifacts (SLSA) specification.
Vulnerabilities
Lists any vulnerabilities found in your artifact or artifacts.
VEX status
Vulnerability Exploitability eXchange(VEX) status for the build artifacts.
SBOM
Software bill of materials (SBOM) for the build artifacts.
Build details
Includes information about the build.
Requirements
Security insights are available only for container images that meet the following requirements:
Vulnerability scanning must be enabled.
The required Identity and Access Management roles must be granted, in the project where Artifact Analysis is running.
The name of the image, as part of release creation, must be SHA qualified.
If the image is shown in the Artifacts tab in Cloud Deploy without the SHA256 hash, you might need to rebuild that image.
Enable vulnerability scanning
The information shown in the Security Insights panel comes from Artifact Analysis and potentially from Cloud Build. Artifact Analysis is a service that provides integrated on-demand or automated scanning for base container images, Maven, and Go packages in containers, and for non-containerized Maven packages.
To receive all of the security insights available, you must enable vulnerability scanning:
To turn on vulnerability scanning, enable the required APIs.
Roles required to enable APIs
To enable APIs, you need the Service Usage Admin IAM role (
roles/serviceusage.serviceUsageAdmin), which contains theserviceusage.services.enablepermission. Learn how to grant roles.Build your container image, and store it in Artifact Registry. Artifact Analysis automatically scans the build artifacts.
Vulnerability scanning may take a few minutes, depending on the size of your container image.
For more information on vulnerability scanning, see On-push scanning.
There is a cost for scanning. See the Pricing page for pricing information.
Grant permissions to view insights
To view security insights in Cloud Deploy, you need the IAM roles described here, or a role with equivalent permissions. If Artifact Registry and Artifact Analysis are running in different projects, you must add the Artifact Analysis Occurrences Viewer role, or equivalent permissions, in the project where Artifact Analysis is running.
Cloud Build Viewer (
roles/cloudbuild.builds.viewer)View insights for a build.
Artifact Analysis Viewer (
roles/containeranalysis.occurrences.viewer)View vulnerabilities and other dependency information.
View security insights in Cloud Deploy
Open the Cloud Deploy Delivery pipelines page in the Google Cloud console:
If necessary, select the project that includes the pipeline and release that delivered the container image for which you want to view security insights.
Click the name of the delivery pipeline.
The delivery pipeline details are shown.
From the Delivery pipeline details page, select a release that delivered the container image.
On the Release details page, select the Artifacts tab.
Containers that were delivered by the selected release are listed under Build artifacts. For each container, the Security insights column includes a View link.
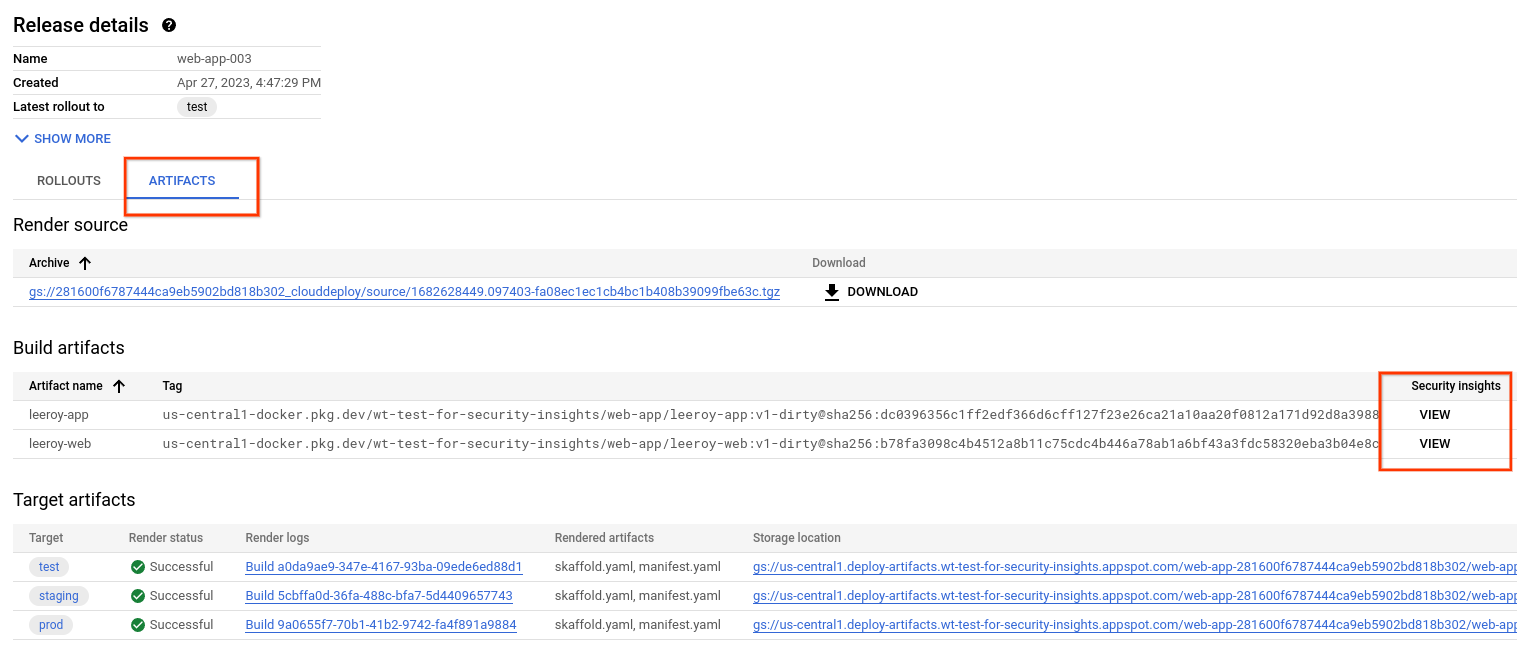
Click the View link next to the name of the artifact whose security details you want to view.
The Security insights panel is displayed, showing available security information for this artifact. The following sections describe this information in more detail.
SLSA level
SLSA is an industry-standard set security guidelines for producers and consumers of software. This standard establishes four levels of confidence in the security of your software.
Vulnerabilities
The Vulnerabilities card shows the vulnerability occurrences, available fixes, and VEX status for the build artifacts.
Artifact Analysis supports scanning for container images pushed to Artifact Registry. The scans detect vulnerabilities in operating system packages, and in application packages created in Python, Node.js, Java (Maven), or Go.
Scanning results are organized by severity level. The severity level is a qualitative assessment based on exploitability, scope, impact, and maturity of the vulnerability.
Click the image name to see the artifacts that have been scanned for vulnerabilities.
For every container image pushed to Artifact Registry, Artifact Analysis can store an associated VEX statement. VEX is a type of security advisory that indicates whether a product is affected by a known vulnerability.
Each VEX statement provides:
- The publisher of the VEX Statement
- The artifact for which the statement is written
- The vulnerability assessment (VEX status) for any CVEs
Dependencies
The Dependencies card displays a list of SBOMs that include a list of dependencies.
When you build a container image using Cloud Build and push it to Artifact Registry, Artifact Analysis can generate SBOM records for the pushed images.
An SBOM is a full inventory of an application, identifying the packages your software relies on. The contents can include third-party software from vendors, internal artifacts, and open source libraries.
Build details
The build details include the following:
A link to the Cloud Build logs
The name of the builder that built the image
The build date/time
Build provenance, in JSON format
What's next
Try the quickstart Deploy an app to GKE and view security insights
Try the quickstart Deploy an app to Cloud Run and view security insights
Learn how to store and view build logs.
