Tags provide a way to conditionally allow or deny policies based on whether a resource has a specific tag. You can use tags and conditional enforcement of organization policies to provide centralized control of the resources in your hierarchy.
Before you begin
For more information about what tags are and how they work, see the Tags overview.
For detailed instructions about how to use tags, see Creating and managing tags.
Required roles
To get the permissions that
you need to manage organization policies,
ask your administrator to grant you the
Organization policy administrator (roles/orgpolicy.policyAdmin)
IAM role on the organization.
For more information about granting roles, see Manage access to projects, folders, and organizations.
You might also be able to get the required permissions through custom roles or other predefined roles.
You can delegate the administration of organization policies by adding IAM Conditions to the Organization policy administrator role binding. To control the resources where a principal can manage organization policies, you can make the role binding conditional on a particular tag. For more information, see Using constraints.
Setting an organization policy with tags
To use tags to determine where an organization policy should take effect, you must specify a condition in the organization policy YAML file. You can set the condition to match a particular tag key-value pair, requiring that a particular tag value is set for the organization policy to be enforced.
You can also set the condition to match a tag key. This lets you enable or disable enforcement against all resources with that tag key, regardless of what tag value is attached.
Most organization policies are evaluated and enforced when a resource is created or updated. Mandatory tags can be used to govern resources as they are created.
List rule example
The following example demonstrates how to set an organization policy that
enforces the gcp.resourceLocations legacy managed constraint. This
organization policy uses both conditional and unconditional values, set within
the same policy file.
Console
To set the organization policy, do the following:
In the Google Cloud console, go to the Organization policies page.
From the project picker, select the project for which you want to set the organization policy.
On the Organization policies page, select a constraint from the list. The Policy details page for that constraint appears.
To update the organization policy for this resource, click Manage policy.
On the Edit policy page, select Override parent's policy.
Under Policy enforcement, select an enforcement option:
To merge and evaluate your organization policies together, select Merge with parent. For more information about inheritance and the resource hierarchy, see Understanding Hierarchy Evaluation.
To override policies inherited from a parent resource, select Replace.
Click Add rule.
Under Policy values, select whether this organization policy should allow all values, deny all values, or specify a custom set of values.
- Specific values accepted by the policy depend on the service to which the policy applies. For a list of constraints and the values they accept, see Organization policy constraints.
Optionally, to make the organization policy conditional on a tag, click Add condition.
In the Title field, enter a name for the condition.
In the Description field, give your condition a description. The description provides context on the tags that are required and how they impact resources.
You can use the Condition builder to create a condition that requires a particular tag for the constraint to take effect.
In the Condition type box, select Tag.
Select the Operator for your condition.
To match an entire tag, use the has value operator with the namespaced name of the tag, or use the has value ID operator with the key and value IDs of the tag.
To match the tag key only, use the has key operator with the namespaced name of the tag key, or use the has key ID operator with the tag key ID.
You can create multiple conditions by clicking Add. If you add another condition, you can set the conditional logic to require all of them by toggling And. You can set the conditional logic to require only one of the conditions to be true by toggling Or.
You can delete an expression by clicking the large X to the right of the condition fields.
When you have finished editing your conditions, click Save.
The Condition editor can be used to create a conditional expression programmatically. It will also display a programmatic rendering of your current set of conditions.
The conditional expression must include 1 to 10 subexpressions, joined by the
||or&&operators. Each subexpression must be one of the following functions:"resource.matchTag('KEY_NAME', 'VALUE_SHORT_NAME')"Replace the following:
KEY_NAMEwith the namespaced name of the tag key. For example,123456789012/env.VALUE_SHORT_NAMEwith the short name of the tag value. For example,prod.
For example:
resource.matchTag('123456789012/environment, 'prod')"resource.matchTagId('KEY_ID', 'VALUE_ID')"Replace the following:
KEY_IDwith the permanent ID of the tag key. For example,tagKeys/123456789012.VALUE_IDwith the permanent ID of the tag value. For example,tagValues/567890123456.
For example:
resource.matchTagId('tagKeys/123456789012', 'tagValues/567890123456')"resource.hasTagKey('KEY_NAME')"Replace
KEY_NAMEwith the namespaced name of the tag key. For example,123456789012/env.For example:
resource.matchTag('123456789012/environment, 'prod')"resource.hasTagKeyId('KEY_ID')"Replace
KEY_IDwith the permanent ID of the tag key. For example,tagKeys/123456789012.For example:
resource.matchTagId('tagKeys/123456789012')
- You can use the Condition editor to apply the
!logical operator. For example, the query!resource.matchTag('ORGANIZATION_ID/location', 'us-west1')would apply the organization policy constraint to any resource that does not have theus-west1tag.
To enforce the policy, click Set policy.
gcloud
To set the organization policy, create a YAML file to store the organization policy:
name: RESOURCE_TYPE/RESOURCE_ID/policies/gcp.resourceLocations
spec:
rules:
# As there is no condition specified, this allowedValue is enforced unconditionally.
- values:
allowedValues:
- us-east1-locations
# This condition applies to the values block.
- condition:
expression: "resource.matchTag('ORGANIZATION_ID/location', 'us-west1')"
values:
allowedValues:
- us-west1-locations
You can match an entire tag with the condition using the resource.matchTag
operator with the namespaced name of the tag.
To match the tag key only, use the resource.hasTagKey operator with the
namespaced name of the tag key. To match any tag value for a given tag key,
use the resource.hasTagKeyID operator with the tag key ID.
Run the set-policy command:
gcloud org-policies set-policy POLICY_PATH
Replace the following:
POLICY_PATH: the full path to your organization policy YAML fileRESOURCE_TYPE:organizations,foldersorprojectsRESOURCE_ID: your organization ID, folder ID, project ID, or project number, depending on the type of resource specified inRESOURCE_TYPEORGANIZATION_ID: the parent organization of your tag key
For this organization policy, the resource and all of its child resources have
the gcp.resourceLocations legacy managed constraint enforced against them,
with allowedValues of us-east1-locations only. Any of these
resources that have the tag location: us-west1 will have the
gcp.resourceLocations legacy managed constraint enforced against it, with
allowedValues of us-east1-locations and us-west1-locations.
In this way, both conditional and unconditional sets of values can be enforced for a constraint in a single organization policy.
Boolean rule example
The following example demonstrates how to set an organization policy that
enforces the compute.disableSerialPortAccess legacy managed constraint. This
organization policy specifies that all serial ports are accessible to resources,
but uses a condition to only restrict serial port access to resources that have
the matching tag.
Console
To set the organization policy, do the following:
In the Google Cloud console, go to the Organization policies page.
From the project picker, select the project for which you want to set the organization policy.
Select a constraint from the list on the Organization policies page. The Policy details page for that constraint should appear.
To update the organization policy for this resource, click Manage policy.
On the Edit policy page, select Override parent's policy.
Click Add rule.
Under Enforcement, select whether enforcement of this organization policy should be on or off.
Optionally, to make the organization policy conditional on a tag, click Add condition. Note that, if you add a conditional rule to an organization policy, you must add only one unconditional rule or the policy cannot be saved.
In the Title field, enter a name for the condition.
In the Description field, give your condition a description. The description provides context on the tags that are required and how they impact resources.
You can use the Condition builder to create a condition that requires a particular tag for the constraint to take effect.
In the Condition type box, select Tag.
Select the Operator for your condition.
To match an entire tag, use the has value operator with the namespaced name of the tag, or use the has value ID operator with the key and value IDs of the tag.
To match the tag key only, use the has key operator with the namespaced name of the tag key, or use the has key ID operator with the tag key ID.
You can create multiple conditions by clicking Add. If you add another condition, you can set the conditional logic to require all of them by toggling And. You can set the conditional logic to require only one of the conditions to be true by toggling Or.
You can delete an expression by clicking the large X to the right of the condition fields.
When you have finished editing your conditions, click Save.
An organization policy with a condition enforced must have only one unconditional rule. Click Add rule, and set whether enforcement of this organization policy should default to on or off.
The Condition editor can be used to create a conditional expression programmatically. It will also display a programmatic rendering of your current set of conditions.
The conditional expression must include from 1 to 10 subexpressions, joined by the
||or&&operators. Each subexpression must be one of the following forms:"resource.matchTag('KEY_NAME', 'VALUE_SHORT_NAME')"Replace the following:
KEY_NAMEwith the namespaced name of the tag key. For example,123456789012/env.VALUE_SHORT_NAMEwith the short name of the tag value. For example,prod.
"resource.matchTagId('KEY_ID', 'VALUE_ID')"Replace the following:
KEY_IDwith the permanent ID of the tag key. For example,tagKeys/123456789012.VALUE_IDwith the permanent ID of the tag value. For example,tagValues/567890123456.
- You can use the Condition editor to apply the
!logical operator. For example, the query!resource.matchTag('ORGANIZATION_ID/location', 'us-west1')would apply the organization policy constraint to any resource that does not have theus-west1tag.
To finish and apply the organization policy, click Save.
gcloud
To set the organization policy, create a YAML file to store the organization policy:
name: RESOURCE_TYPE/RESOURCE_ID/policies/gcp.disableSerialPortAccess
spec:
rules:
- condition:
expression: "resource.matchTag('ORGANIZATION_ID/disableSerialAccess', 'yes')"
enforce: true
- enforce: false
You can match an entire tag with the condition using the resource.matchTag
operator with the namespaced name of the tag.
To match the tag key only, use the resource.hasTagKey operator with the
namespaced name of the tag key. To match any tag value for a given tag key,
use the resource.hasTagKeyID operator with the tag key ID.
Run the set-policy command:
gcloud org-policies set-policy POLICY_PATH
Replace the following:
POLICY_PATH: the full path to your organization policy YAML fileRESOURCE_TYPE:organizations,foldersorprojectsRESOURCE_ID: your organization ID, folder ID, project ID, or project numberORGANIZATION_ID: the parent organization of your tag key
For this organization policy, the resource and all of its child resources
have the gcp.disableSerialPortAccess legacy managed constraint enforced
against them. Any resources that have the tag disableSerialAccess: yes are
denied by the organization policy. Any resource that does not have the tag
disableSerialAccess: yes doesn't have the legacy managed constraint enforced
against them.
Conditionally add rules to organization policy
You can use tags to conditionally add constraint rules to resources based on the tags they have attached. You can add multiple conditions within the same organization policy, which gives you fine-grained control of the resources to which you want the organization policy to apply.
Common Expression Language, or CEL, is the expression language used to specify
conditional expressions. A conditional expression consists of one or more
statements that are joined using logical operators (&&, ||, or !). For
more information, see the
CEL spec and its language
definition.
Consider an organization policy to restrict the locations in which resources
could be created based on the tags applied to those resources. To do this,
create an organization policy that enforces the gcp.resourceLocations
legacy managed constraint, and use conditions to narrow enforcement to only
certain resources.
Start by creating a temporary file, /tmp/policy.yaml, to contain your
organization policy:
name: organizations/ORGANIZATION_ID/policies/gcp.resourceLocations
spec:
rules:
- condition:
expression: "resource.matchTag('ORGANIZATION_ID/location', 'us-east')"
values:
allowedValues:
- in:us-east1-locations
- condition:
expression: "resource.matchTag('ORGANIZATION_ID/location', 'us-west')"
values:
allowedValues:
- in:us-west1-locations
- values:
deniedValues:
- in:asia-south1-locations
Replace ORGANIZATION_ID with the parent organization of
your tag key.
In this example, any resource that has the location: us-east tag attached
will be restricted to locations within the us-east1-locations value group. Any
resource that has the location: us-west tag attached will be restricted to
locations within the us-west1-locations value group. All resources in the
organization will be blocked from locations within the asia-south1-locations
value group.
Then, set the policy using the set-policy command:
gcloud org-policies set-policy /tmp/policy.yaml
Restricting untagged resources
You can use tags and conditional organization policies to restrict any resources that are not using a particular tag. If you set an organization policy on a resource that restricts services and make it conditional on the presence of a tag, no child resources descended from that resource can be used unless they have been tagged. In this way, resources must be set up in accordance with your governance plan before they can be used.
To restrict untagged organization, folder, or project resources, you can use the
! logical operator in a conditional query when creating your organization
policy.
For example, to allow the usage of sqladmin.googleapis.com only in projects
that have the tag sqladmin=enabled, you can create an organization policy that
denies sqladmin.googleapis.com on projects that do not have the tag
sqladmin=enabled.
Create a tag that identifies whether the resources have had proper governance applied. For example, you could create a tag with the key
sqlAdminand the valueenabled, to designate that this resource should allow the usage of the Cloud SQL Admin API. For example: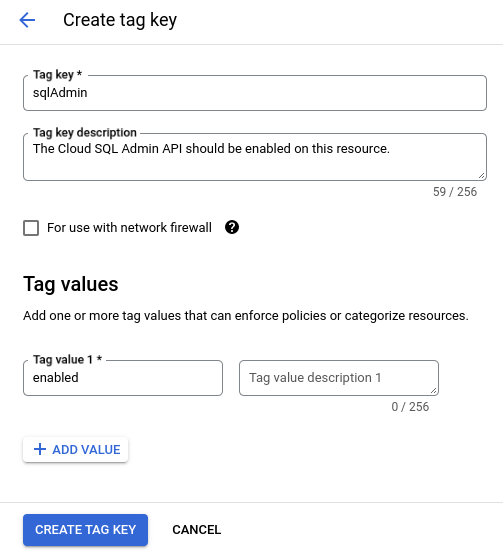
Click on the name of the newly created tag. You need the namespaced name of the tag key, listed under Tag key path, in the next steps to create a condition.
Create a Restrict Resource Service Usage organization policy at the level of your organization resource to deny access to the Cloud SQL Admin API. For example:
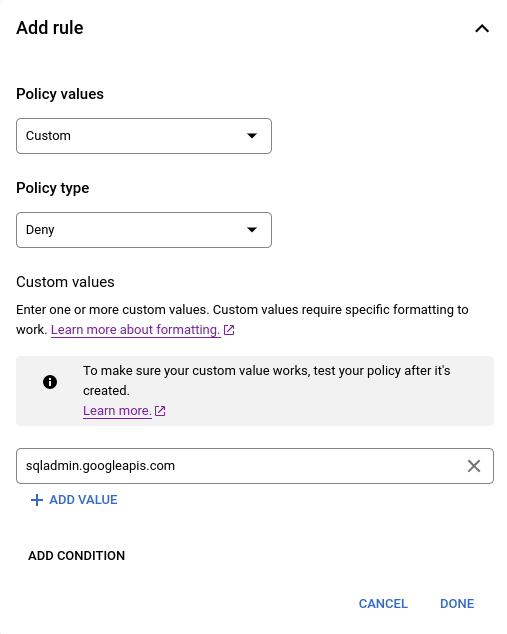
Add a condition to the above organization policy, specifying that the policy is enforced if the governance tag is not present. The logical NOT operator is not supported by the condition builder, so this condition must be built in the condition editor. For example:
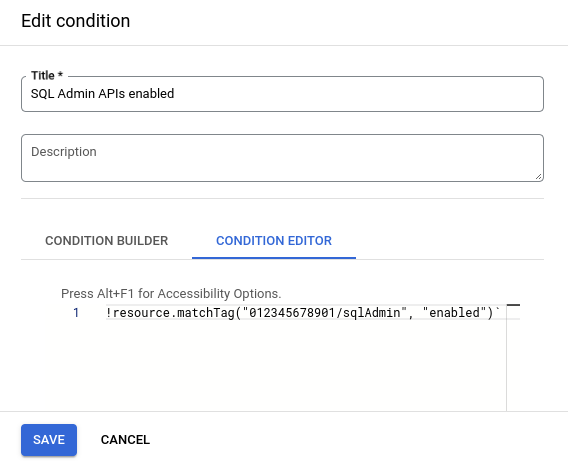
!resource.matchTag("012345678901/sqlAdmin", "enabled")
Now, the sqlAdmin=enabled tag must be attached to or inherited by a project,
before your developers can use the Cloud SQL Admin API with that project.
Enforcing mandatory tags on resources
You can enforce mandatory tags on resources by using a custom organization policy. When you enforce mandatory tags, you can only create resources that comply with your organization's tagging policies; that is, resources are bound with the tag values for the mandatory tag keys specified in the policy. For more information, see Set up a custom constraint to enforce tags.
Organization policy inheritance
Constraints with list rules that are enabled using tags merge with the existing organization policy, per normal rules of inheritance. These conditional rules only apply if the condition is true.
Constraints with boolean rules that are enabled using tags override the existing organization policy. In addition, since boolean rules only have two states, true or false, then all conditional statements must be the opposite of the non-condition statement to prevent multiple tags from conflicting with each other.
For example, consider an organization policy that enforces the
disableSerialPortAccess legacy managed constraint. The unconditional value,
which is the value that is used if no conditions override it, is true. Therefore,
any other conditional statements for this policy must be set to false to not
conflict.
What's next
For more information about how to use tags, read the Creating and managing tags page.
For more information about how to create and manage organization policy constraints, see Using constraints.
