本页面简要介绍了限制资源服务使用 组织政策限制条件,这项政策可让企业管理员控制可以在其 Google Cloud资源层次结构中使用哪些Google Cloud 服务。此限制条件只能对资源是组织、文件夹或项目资源的直接后代的服务强制执行。例如,Compute Engine 和 Cloud Storage。
限制资源服务使用约束条件会排除某些对产品至关重要的依赖项服务,例如 Identity and Access Management (IAM)、Cloud Logging 和 Cloud Monitoring,并且不会对这些服务生效。 Google Cloud如需查看受此限制条件支持的云资源服务列表,请参阅限制资源使用支持的服务。
管理员可以使用此限制条件来定义对资源容器(例如组织、文件夹或项目)中允许的 Google Cloud 资源服务的分层限制。例如,允许项目 X 中的 storage.googleapis.com,或拒绝文件夹 Y 中的 compute.googleapis.com。此约束条件还决定了 Google Cloud 控制台的可用性。
限制资源服务使用限制条件可通过两种互斥的方式使用:
拒绝名单 - 允许任何未拒绝的服务的资源。
许可名单 - 拒绝任何不允许的服务的资源。
限制资源服务使用限制条件会控制对所有范围内资源的运行时访问权限。包含此约束条件的组织政策更新后,它会立即应用于对该政策范围内的所有资源的所有访问权限,最终会保持一致。
我们建议管理员谨慎管理包含此限制条件的组织政策的更新。您可以使用标记来有条件地强制执行该限制条件,以便更安全地发布此政策更改。如需了解详情,请参阅设置带有标记的组织政策。
当某项服务受此政策限制时,与受限服务存在直接依赖关系的部分服务也将受到限制。 Google Cloud 这仅适用于管理相同客户资源的服务。例如,Google Kubernetes Engine (GKE) 依赖于 Compute Engine。当 Compute Engine 受到限制时,GKE 也会受到限制。
Google Cloud 控制台可用性
Google Cloud 控制台中受限服务的行为方式如下:
- 您无法使用 菜单导航到商品。
- 受限服务不会显示在 Google Cloud 控制台搜索结果中。
- 当您前往受限服务的 Google Cloud 控制台页面(例如通过链接或书签)时,系统会显示一条错误消息。
使用“限制资源服务使用”限制条件
组织政策限制条件可以在组织、文件夹和项目级层进行设置。每项政策都适用于其相应资源层次结构中的所有资源,但可能会在该资源层次结构的较低级层被替换。
如需详细了解政策评估,请参阅了解层次结构评估。
设置组织政策
要设置、更改或删除组织政策,您必须拥有组织政策管理员角色。
控制台
如需设置包含限制资源服务使用限制条件的组织政策,请执行以下操作:
在 Google Cloud 控制台中,前往组织政策页面。
在项目选择器中,选择要为其设置组织政策的资源。
在组织政策表中,选择限制资源服务使用 (Restrict Resource Service Usage)。
点击管理政策。
在应用对象下,选择覆盖父资源的政策。
在政策执行下,选择此政策的继承方式。
如果要继承父资源的组织政策并将其与此政策合并,请选择与父资源规则合并。
如果您要替换任何现有组织政策,请选择替换。
点击添加规则。
在政策值下方,选择自定义。
在政策类型下,选择拒绝表示列入拒绝名单,选择允许表示列入许可名单。
在自定义值下,将您要阻止或允许的服务添加到列表中。
例如,如需阻止 Cloud Storage,您可以输入
storage.googleapis.com。如需添加更多服务,请点击添加值。
如需强制执行政策,请点击设置政策。
gcloud
可以通过 Google Cloud CLI 设置组织政策。如需强制执行包含限制资源服务使用限制条件的组织政策,请先创建一个包含要更新的政策的 YAML 文件:
name: organizations/ORGANIZATION_ID/policies/gcp.restrictServiceUsage
spec:
rules:
- values:
deniedValues:
- file.googleapis.com
- bigquery.googleapis.com
- storage.googleapis.com
将 ORGANIZATION_ID 替换为您的组织资源的 ID。 如需对该组织设置此政策,请运行以下命令:
gcloud org-policies set-policy /tmp/policy.yaml
如需了解如何在组织政策中使用限制条件,请参阅使用限制条件。
限制未标记的资源
您可以使用标记和有条件的组织政策来限制不使用特定标记的任何资源。如果您对某个资源设置了限制服务的组织政策,并使其取决于是否存在标记,则除非已添加标记,否则无法使用该资源派生的任何子资源。这样一来,必须先根据治理计划设置资源,然后才能使用这些资源。
如需限制未标记的组织、文件夹或项目资源,您可以在创建组织政策时在条件查询中使用 ! 逻辑运算符。
例如,如需仅允许在具有 sqladmin=enabled 标记的项目中使用 sqladmin.googleapis.com,您可以创建一个组织政策,用于对不具有 sqladmin=enabled 标记的项目拒绝使用 sqladmin.googleapis.com。
创建一个标记,用于确定资源是否已应用适当的治理。例如,您可以创建一个键为
sqlAdmin且值为enabled的标记,以指定此资源应允许使用 Cloud SQL Admin API。例如: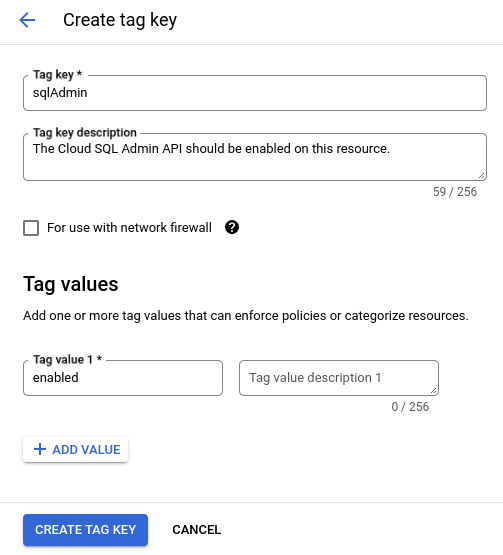
点击新创建的代码的名称。您需要在下一步中创建条件时使用标记键路径下列出的标记键的命名空间名称。
在组织资源级别创建限制资源服务使用组织政策,以拒绝对 Cloud SQL Admin API 的访问。例如:
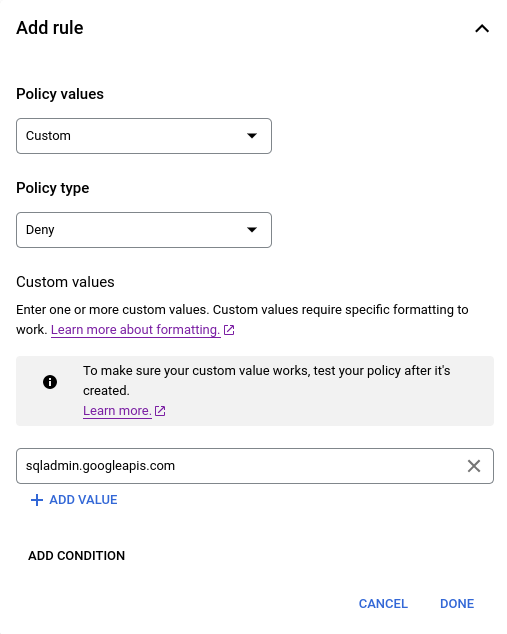
向上述组织政策添加一个条件,指定如果不存在治理标记,则强制执行该政策。条件构建器不支持逻辑 NOT 运算符,因此必须在条件编辑器中构建此条件。例如:
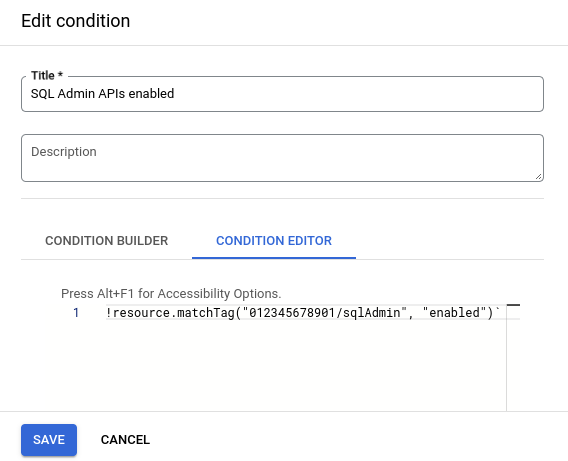
!resource.matchTag("012345678901/sqlAdmin", "enabled")
现在,必须将 sqlAdmin=enabled 标记附加到项目或由项目继承该标记,您的开发者才能对该项目使用 Cloud SQL Admin API。
如需详细了解如何创建基于条件的组织政策,请参阅设置带有标记的组织政策。
在试运行模式下创建组织政策
处于试运行模式的组织政策是一种组织政策,其中违反政策的行为会记录在审核日志中,但系统不会拒绝违规操作。您可以在试运行模式下使用限制资源服务使用限制条件创建组织政策,以便在强制执行正式政策之前监控该政策对组织的影响。如需了解详情,请参阅在试运行模式下创建组织政策。
错误消息
如果您设置了一项组织政策来拒绝资源层次结构 B 中的服务 A,则当客户端尝试使用资源层次结构 B 中的服务 A 时,操作将失败。系统会返回错误消息,说明失败的原因,此外还会生成一个 AuditLog 条目以进一步监控、提醒或调试。
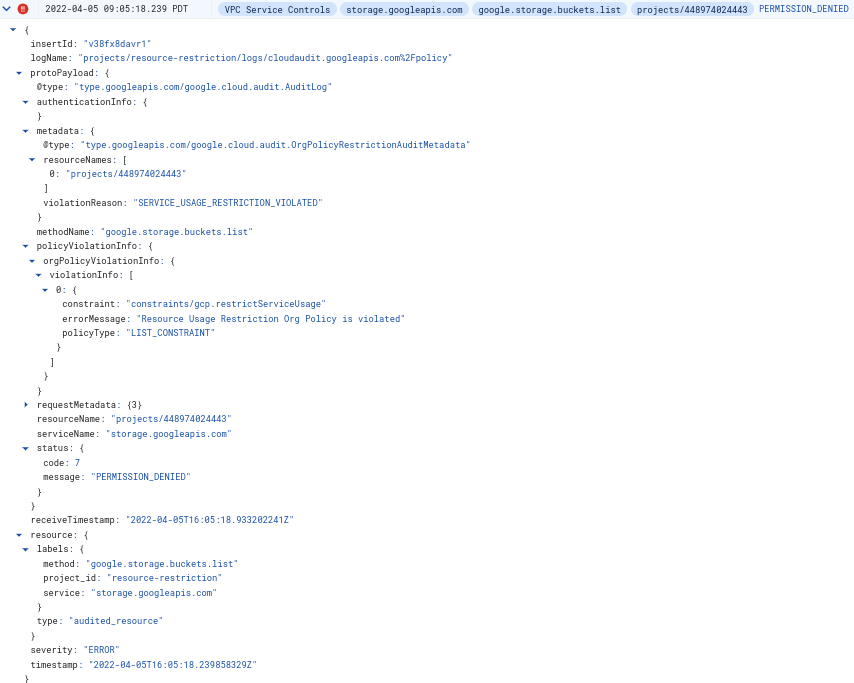
错误消息示例
Request is disallowed by organization's constraints/gcp.restrictServiceUsage constraint for projects/PROJECT_ID attempting to use service storage.googleapis.com.
Cloud Audit Logs 示例