This page explains how to view security information about your Cloud Build builds using the Security insights side panel in the Google Cloud console.
The Security insights side panel provides a high-level overview of multiple security metrics. You can use the side panel to identify and mitigate risks in your build process.
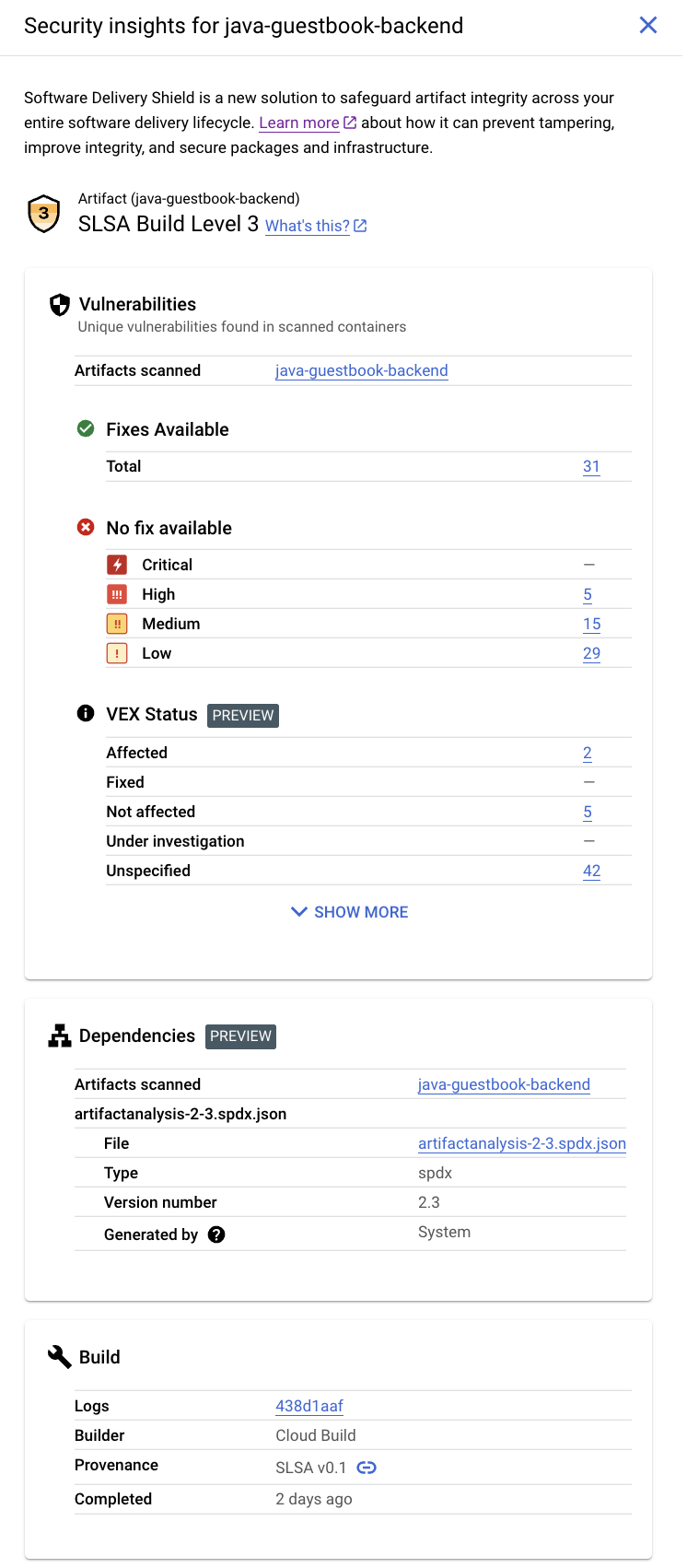
This panel displays the following information:
- Supply-chain Levels for Software Artifacts (SLSA) Level: Identifies the maturity level of your software build process in accordance with the SLSA specification. For example, this build has achieved SLSA Level 3.
- Vulnerabilities: An overview of any vulnerabilities found in your artifacts, and the name of the image that Artifact Analysis has scanned. You can click the image name to view vulnerability details. For example, in the screenshot, you can click on java-guestbook-backend.
- Vulnerability Exploitability eXchange(VEX) status for the built artifacts.
- Software bill of materials (SBOM) for the build artifacts.
- Build details: Details of the build such as the builder and the link to view logs.
To learn how you can use Cloud Build with other Google Cloud products and features to improve the security posture of your software supply chain, see Software supply chain security.
Enable vulnerability scanning
The Security insights panel displays data from Cloud Build and from Artifact Analysis. Artifact Analysis is a service that scans for vulnerabilities in OS, Java (Maven) and Go packages when you upload build artifacts to Artifact Registry.
You must enable vulnerability scanning to receive the complete set of Security insights results.
Enable the Container Scanning API to turn on vulnerability scanning.
Execute a build and store your build artifact in Artifact Registry. Artifact Analysis automatically scans the build artifacts.
Vulnerability scanning may take a few minutes, depending on the size of your build.
For more information on vulnerability scanning, see Automatic scanning.
There is a cost for scanning. See the Pricing page for pricing information.
Grant permissions to view insights
To view Security insights in Google Cloud console, you must have the following IAM roles, or a role with equivalent permissions. If Artifact Registry and Artifact Analysis are running in different projects, you must add the Container Analysis Occurrences Viewer role or equivalent permissions in the project where Artifact Analysis is running.
- Cloud Build
Viewer
(
roles/cloudbuild.builds.viewer): View insights for a build. - Container Analysis Occurrences Viewer
(
roles/containeranalysis.occurrences.viewer): View vulnerabilities and other dependency information.
View the Security insights side panel
To view the Security insights panel:
Open the Build History page in the Google Cloud console:
Select your project and click Open.
In the Region drop-down menu, select the region in which you ran your build.
In the table with the builds, locate the row with the build for which you want to view security insights.
Under the Security insights column click View.
This opens the Security insights side panel.
[Optional] If your build produces multiple artifacts, select the artifact for which you want to view security insights from the Artifact drop-down box.
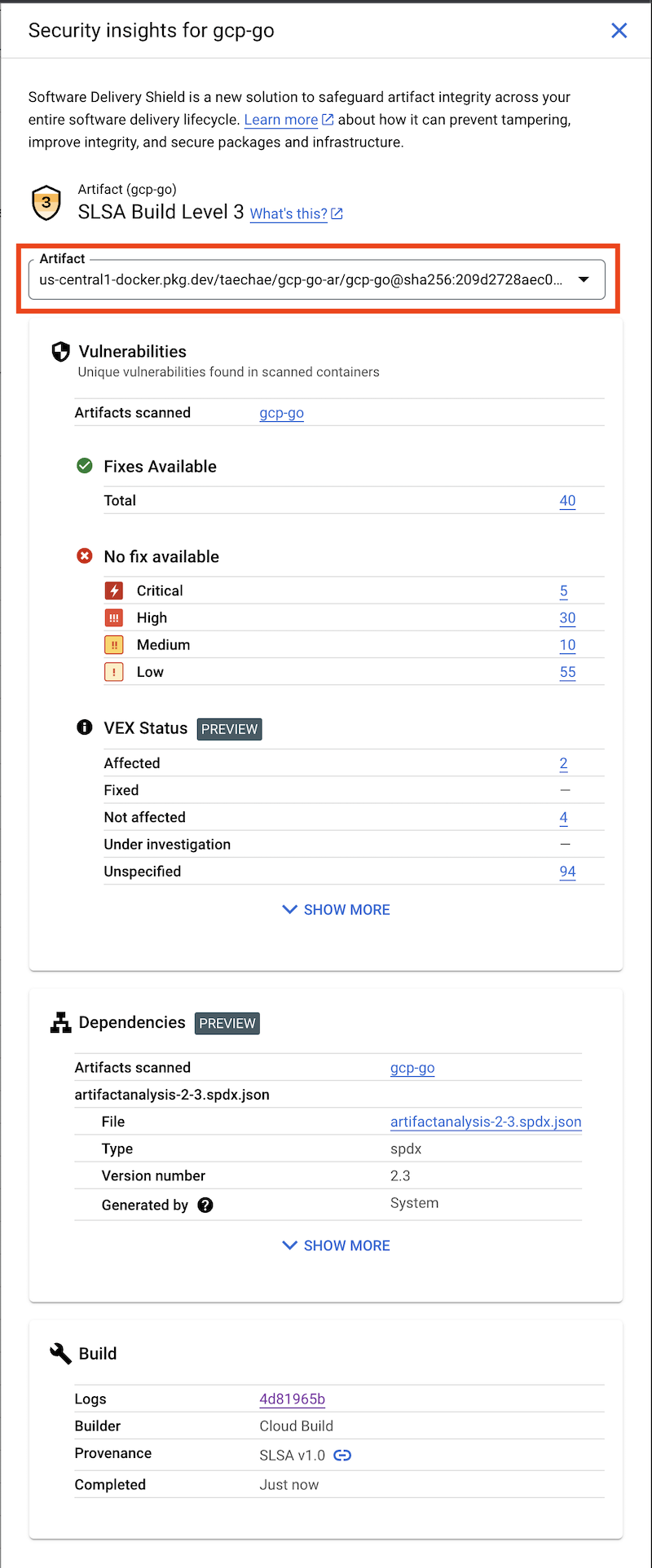
This displays the Security insights panel for the selected artifact.
SLSA level
The SLSA level rates your build's current level of security assurance based on a collection of guidelines.
Vulnerabilities
The Vulnerabilities card displays the vulnerability occurrences, available fixes, and VEX status for the build artifacts.
Artifact Analysis supports scanning for container images pushed to Artifact Registry. The scans detect vulnerabilities in operating system packages, and in application packages created in Java (Maven) or Go.
Scanning results are organized by severity level. The severity level is a qualitative assessment based on exploitability, scope, impact, and maturity of the vulnerability.
Click the image name to see the artifacts that have been scanned for vulnerabilities.
For every container image pushed to Artifact Registry, Artifact Analysis can store an associated VEX statement. VEX is a type of security advisory that indicates whether a product is affected by a known vulnerability.
Each VEX statement provides:
- The publisher of the VEX Statement
- The artifact for which the statement is written
- The vulnerability assessment (VEX status) for any known vulnerabilities
Dependencies
The Dependencies card shows a list of SBOMs with a list of dependencies.
When you build a container image using Cloud Build and push it to Artifact Registry, Artifact Analysis can generate SBOM records for the pushed images.
An SBOM is a full inventory of an application, identifying the packages your software relies on. The contents can include third-party software from vendors, internal artifacts, and open source libraries.
Build
The Build card includes the following information:
- Logs - links to your build log information
- Builder - builder name
- Completed - time elapsed since the build completed
- Provenance - verifiable metadata about a build
Provenance metadata includes details such as the digests of the built images, the input source locations, the build toolchain, build steps, and the build duration. You can also validate build provenance at any time.
To ensure that your future builds include provenance information, configure Cloud Build to require that your images have provenance metadata.
What's next
- Learn about software supply chain security.
- Learn software supply chain security best practices.
- Learn how to store and view build logs.
- Learn how to troubleshoot build errors.
