This page provides an overview of Security Command Center in the Google Cloud console, describes the navigation, and gives an overview of top-level pages.
If you haven't set up Security Command Center, see one of the following for instructions about how to activate it:
- To activate the Standard or Premium tier, see Overview of activating Security Command Center.
- To activate the Enterprise tier, see Activate the Security Command Center Enterprise tier.
For a general overview of Security Command Center, see Security Command Center overview.
Required IAM permissions
To use Security Command Center with all service tiers, you must have an Identity and Access Management (IAM) role that includes appropriate permissions:
Standard
- Security Center Admin Viewer (
roles/securitycenter.adminViewer) lets you view Security Command Center. - Security Center Admin Editor (
roles/securitycenter.adminEditor) lets you view Security Command Center and make changes.
Premium
- Security Center Admin Viewer (
roles/securitycenter.adminViewer) lets you view Security Command Center. - Security Center Admin Editor (
roles/securitycenter.adminEditor) lets you view Security Command Center and make changes.
Enterprise
- Security Center Admin Viewer (
roles/securitycenter.adminViewer) lets you view Security Command Center. - Security Center Admin Editor (
roles/securitycenter.adminEditor) lets you view Security Command Center and make changes. - Chronicle Service Viewer (
roles/chroniclesm.viewer) lets you view the associated Google SecOps instance.
You also need any of the following IAM roles:
- Chronicle SOAR Admin (
roles/chronicle.soarAdmin) - Chronicle SOAR Threat Manager (
roles/chronicle.soarThreatManager) - Chronicle SOAR Vulnerability Manager
(
roles/chronicle.soarVulnerabilityManager)
To enable access to SOAR-related features, you must also map these Identity and Access Management roles to a SOC role, Permission group, and Environment on the Settings > SOAR settings page. For more information, see Map and authorize users using IAM.
If your organization policies are set to restrict identities by domain, you must be signed in to the Google Cloud console on an account that's in an allowed domain.
The IAM roles for Security Command Center can be granted at the organization, folder, or project level. Your ability to view, edit, create, or update findings, assets, and security sources depends on the level for which you are granted access. To learn more about Security Command Center roles, see Access control.
Access Security Command Center
To access Security Command Center in the Google Cloud console:
Go to Security Command Center:
If data residency is enabled and your organization uses the jurisdictional Google Cloud console, see About the jurisdictional Google Cloud console.
Select the project or organization that you want to view.
If Security Command Center is active in the organization or project you select, the Risk overview page appears.
If Security Command Center is not active, you are invited to activate it. For more information about activating Security Command Center, see one of the following:
- Standard or Premium: Overview of activating Security Command Center.
- Enterprise: Activate the Security Command Center Enterprise tier.
Security Command Center navigation
The following describes the navigation in Security Command Center. The navigation differs depending on your Security Command Center service tier. The tasks that you can perform also depend on services that are enabled and the IAM permissions that you are granted.
Click a link for an explanation of the page.
Standard
The following describes the navigation in Security Command Center Standard.
- Risk overview
- Threats: Prompts you to upgrade to the Premium service tier.
- Vulnerabilities
- Compliance: Prompts you to upgrade to the Premium service tier.
- Assets
- Findings
- Sources
- Posture Management: Prompts you to upgrade to the Premium service tier.
Premium
The following describes the navigation in Security Command Center Premium.
Enterprise
Security Command Center Enterprise left navigation includes links to pages in the Google Security Operations tenant that was configured during Security Command Center Enterprise activation.
In addition, the Google Security Operations tenant that was configured during Security Command Center Enterprise activation includes links to a subset of Google Cloud console pages.
For information about the features available in Google Security Operations, see Security Command Center Enterprise links to the Security Operations console.
| Section name | Link name |
|---|---|
| Risk | |
| Investigation | |
| Detection | |
| Response | |
| Dashboards | |
| Settings |
Risk overview
The Risk overview page serves as your first-contact security dashboard, highlighting high-priority risks in your cloud environments identified by all built-in and integrated services.
The views on the Risk overview page differ depending on your service tier.
Standard
The Risk overview page includes the following panels:
- Vulnerabilities per resource type is a graphic display that shows the active vulnerabilities for the resources in your project or organization.
- Active vulnerabilities provides tabbed views of the vulnerability findings by category name, by affected resource, and by project. You can sort each view by finding severity.
Premium
Learn more about each investigative view by selecting one of the following views:
- All risk: shows all data.
- Data: displays information about your data security posture.
- Vulnerabilities: displays vulnerabilities and related CVE information.
- Identity: shows a summary of identity and access findings by category.
- Threats: shows threat-related findings.
Enterprise
Learn more about each investigative view by selecting one of the following views:
- All risk: shows all data.
- Vulnerabilities: displays vulnerabilities and related CVE information.
- Data: displays information about your data security posture.
- Code: shows code-related security findings (Preview).
- AI Security: shows AI-related findings and security posture data (Preview).
Assets
The Assets page provides a detailed display of all Google Cloud resources, also called assets, in your project or organization.
For more information about how to work with assets on the Assets page, see Work with resources in the console.
Compliance
By default, when you activate Security Command Center, you enable Compliance Manager. The Compliance page shows the following tabs: Configure (New), Monitor (New), and Audit (New). These tabs let you create and apply cloud controls and frameworks, monitor your environment, and complete audits.
If you activated Security Command Center before Compliance Manager was generally available and you don't enable Compliance Manager, the Compliance page shows a Monitor tab only. This tab shows all industry benchmarks that Security Command Center supports using Security Health Analytics and the percentage of passing benchmark controls. For more information about how Security Command Center supports compliance management if Compliance Manager isn't enabled, see Assess compliance without Compliance Manager.
Findings
On the Findings page, you can query, review, mute, and mark Security Command Center findings, the records that Security Command Center services create when they detect a security issue in your environment. For more information about how to work with findings on the Findings page, see Review and manage findings.
Issues
Issues are the most important security risks that Security Command Center finds in your cloud environments, giving you the opportunity to respond quickly to vulnerabilities and threats. Security Command Center discovers issues through virtual red teaming and rule-based detections. For information about investigating issues, see Issues overview.
Posture management
On the Posture page, you can view details about the security postures that you created in your organization and apply the postures to an organization, folder, or project. You can also view the available predefined posture templates.
SCC settings
In Security Command Center Enterprise, you open the Settings page from the SCC settings link in the navigation. In Security Command Center Standard and Premium, you open the page from the Settings link in the header.
The Settings page lets you configure Security Command Center, including the following:
- Additional Security Command Center services
- Multi-cloud connectors
- High-value resource sets
- Mute findings rules
- Continuous data exports
SCC setup guide
The Setup guide page lets you activate Security Command Center Enterprise and configure additional services. For more information, see Activate the Security Command Center Enterprise tier.
Sources
The Sources page contains cards that provide a summary of assets and findings from the security sources you have enabled. The card for each security source shows some of the findings from that source. You can click the finding category name to view all findings in that category.
Findings by source
The Findings by source card displays a count of each category of finding that your enabled security sources provide.
- To view details about the findings from a specific source, click the source name.
- To view details about all findings, click the Findings page, where you can group findings or view details about an individual finding.
Source summaries
Below the Findings by source card, separate cards appear for any built-in, integrated, and third-party sources you enabled. Each card provides counts of active findings for that source.
Threats
Threats are potentially harmful events in your cloud resources. Security Command Center displays threats in different views, depending on your service tier.
Standard
The Threats page is not supported in Security Command Center Standard. You can view threat findings on the Findings page.
Premium
In Security Command Center Premium, the Threats navigation link opens the Risk Overview > Threats dashboard.
Enterprise
In Security Command Center Enterprise, you view threats in the Risk Overview > Threats dashboard.
Legacy Vulnerabilities page
The legacy Vulnerabilities page lists all of the misconfiguration and software vulnerability findings that the built-in detection services of Security Command Center run in your cloud environments. For each listed detector, the number of active findings is displayed.
To view the Vulnerabilities page in Security Command Center, do the following:
Standard
In the Google Cloud console, go to the Vulnerabilities page.
Premium
In the Google Cloud console, go to the Risk overview page.
On the Risk Overview page, click Vulnerabilities.
On the Vulnerabilities dashboard, click Go to legacy page.
Enterprise
In the Google Cloud console, go to the Risk overview page.
On the Risk Overview page, click Vulnerabilities.
On the Vulnerabilities dashboard, click Go to legacy page.
Vulnerability detection services
The Vulnerabilities page lists detectors for the following built-in detection services of Security Command Center:
- Notebook Security Scanner (Preview)
- Security Health Analytics
- Vulnerability Assessment for Amazon Web Services (AWS)
- Web Security Scanner
Other Google Cloud services that are integrated with Security Command Center also detect software vulnerabilities and misconfigurations. The findings from a selection of these services are also displayed on the Vulnerabilities page. For more information about the services that produce vulnerability findings in Security Command Center, see Detection services.
Information about vulnerability detector categories
For each misconfiguration or software vulnerability detector, the Vulnerabilities page shows the following information:
- Status: an icon indicates whether the detector is active and whether the detector found a finding that needs to be addressed. When you hold the pointer over the status icon, a tooltip displays the date and time the detector found the result or information about how to validate the recommendation.
- Last scanned: the date and time of the last scan for the detector.
- Category: the category or type of vulnerability. For a list of the categories that each Security Command Center service detects, see the following:
Recommendation: a summary of how to remediate the finding. For more information, see the following:
Active: the total number of findings in the category.
Standards: the compliance benchmark that the finding category applies to, if any. For more information about benchmarks, see Vulnerabilities findings.
Filtering vulnerability findings
A large organization might have many vulnerability findings across their deployment to review, triage, and track. By using filters that are available on the Security Command Center Vulnerabilities and Findings pages in the Google Cloud console, you can focus on the highest severity vulnerabilities across your organization, and review vulnerabilities by asset type, project, and more.
For more information about filtering vulnerability findings, see Filter vulnerability findings in Security Command Center.
Security Command Center Enterprise links to the Security Operations console
The Security Command Center Enterprise tier includes features available on both the Google Cloud console pages and on Security Operations console pages.
You sign in to the Google Cloud console and navigate to Security Operations console pages from the Google Cloud console navigation. This section describes the tasks that you can perform on each page and the navigation links that open Security Operations console pages.
Google Cloud console pages
The Google Cloud console pages let you perform tasks such as the following:
- Activate Security Command Center.
- Set up Identity and Access Management (IAM) permissions for all Security Command Center users.
- Connect to other cloud environments to collect resource and configuration data.
- Work with and export findings.
- Assess risks with attack exposure scores.
- Work with issues, the most important security risks Security Command Center Enterprise has found in your cloud environments.
- Identify high-sensitivity data with Sensitive Data Protection.
- Investigate and remediate individual findings.
- Configure Security Health Analytics, Web Security Scanner, and other Google Cloud integrated services.
- Manage security postures.
- Configure cloud controls and frameworks.
- Manage a data security posture.
- Assess and report on your compliance with common security standards or benchmarks.
- View and search your Google Cloud assets.
The following image shows the Security Command Center content in the Google Cloud console.
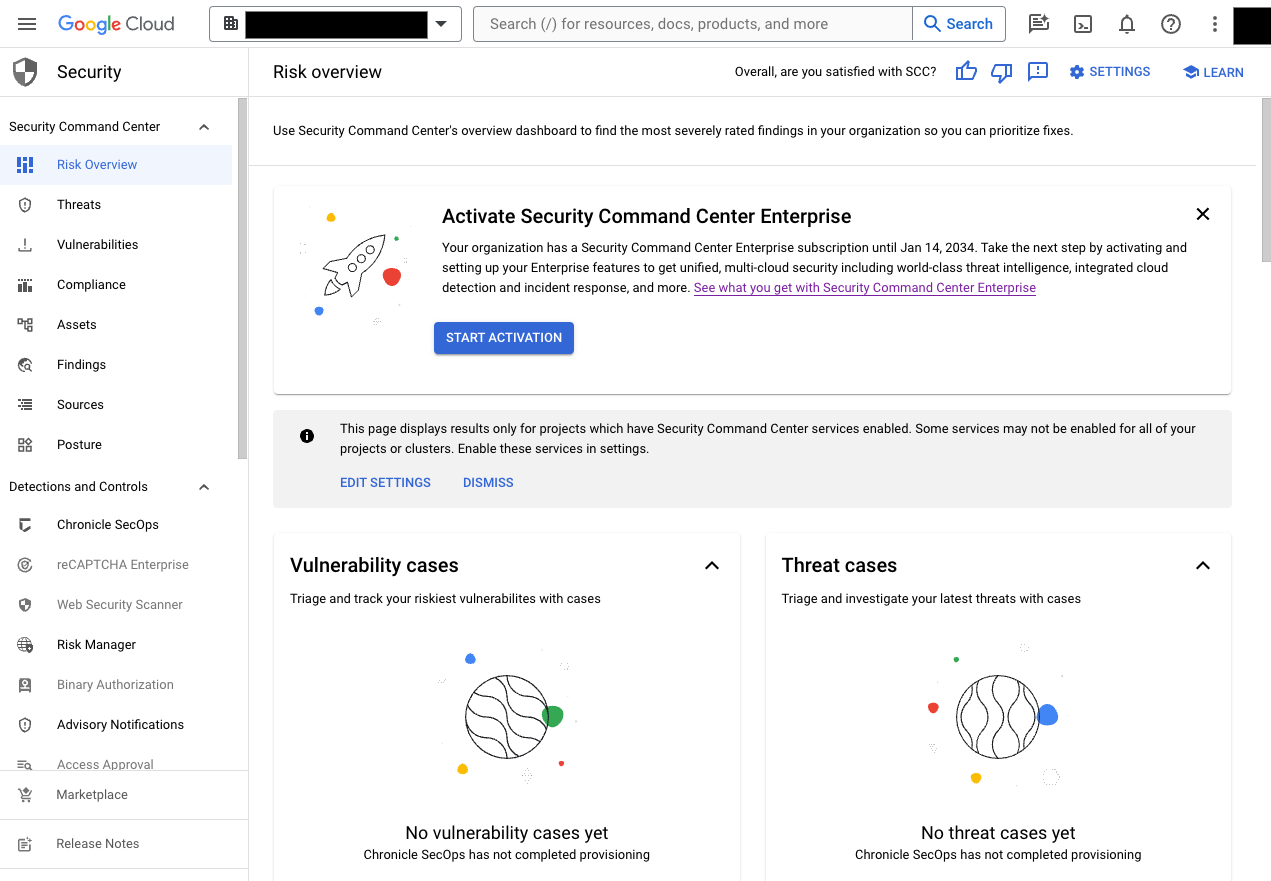
Security Operations console pages
The Security Operations console page lets you perform tasks such as the following:
- Connect to other cloud environments to collect log data for curated detections in security information and event management (SIEM).
- Configure security orchestration, automation, and response (SOAR) settings.
- Configure users and groups for incident and case management.
- Work with cases, which includes grouping findings, assigning tickets, and working with alerts.
- Use an automated sequence of steps known as playbooks to remediate problems.
- Use Workdesk to manage actions and tasks waiting for you from open cases and playbooks.
The following image shows the Security Operations console.
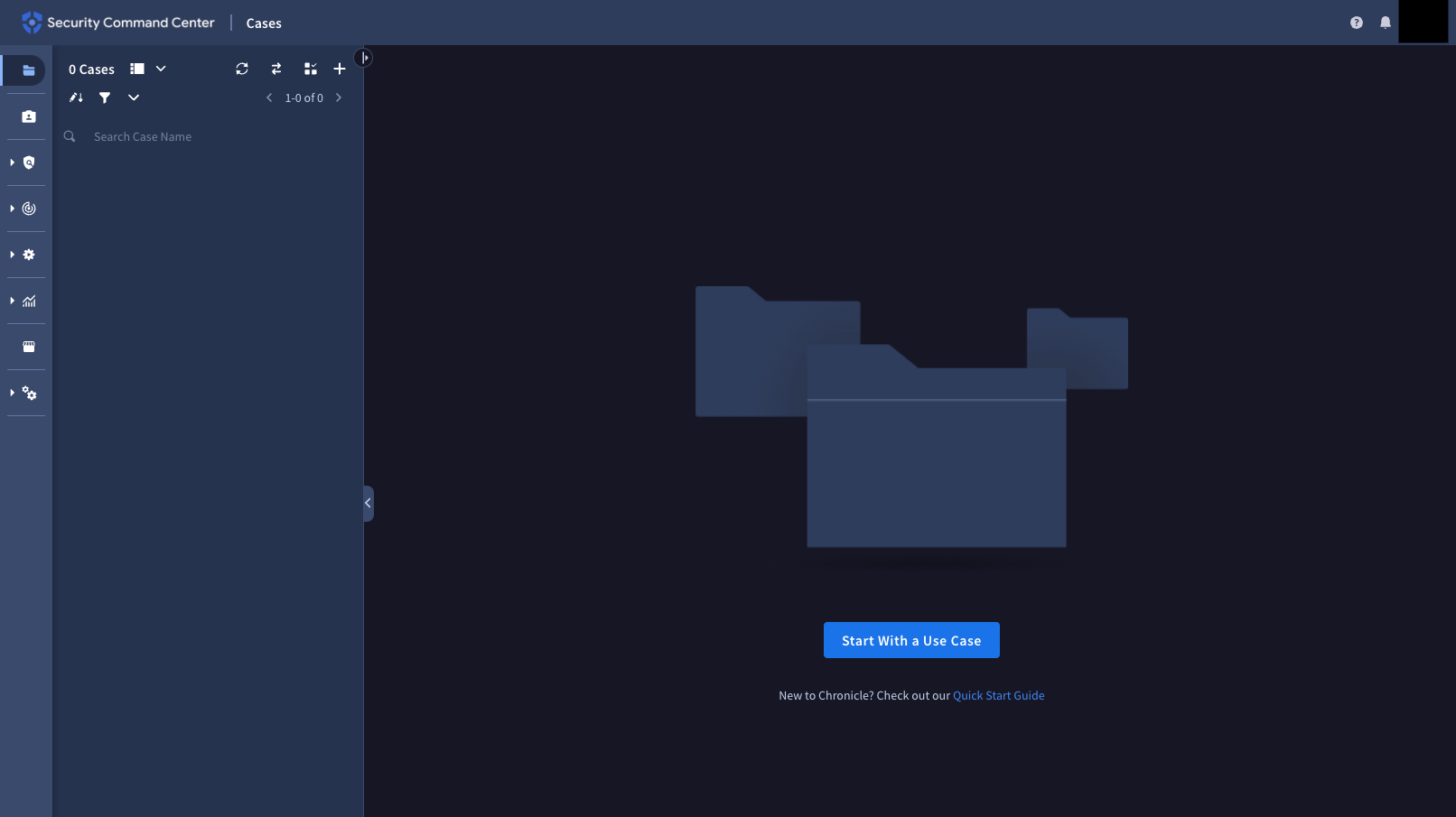
Security Operations console pages have a URL similar to the following pattern.
https://CUSTOMER_SUBDOMAIN.backstory.chronicle.security/cases
Where CUSTOMER_SUBDOMAIN is your customer-specific identifier.
Alerts & IOCs
This Security Operations console page lets you view alerts created by curated detections and custom rules. For information about investigating alerts, see the following in Google Security Operations documentation:
- Investigating a GCTI alert generated by curated detections.
- Investigating an alert.
Cases
In the Security Operations console, you use cases to obtain details about findings, attach playbooks to finding alerts, apply automatic threat responses, and track the remediation of security issues.
For information, see Cases overview in Google Security Operations documentation.
Playbooks
This Security Operations console page lets you manage playbooks included in the SCC Enterprise - Cloud Orchestration and Remediation use case.
For information about the integrations available in this use case, see Security Command Center service tiers.
For information about the available playbooks, see Update the Enterprise use case.
For information about using the Security Operations console Playbooks page, see What's on the Playbooks page? in Google Security Operations documentation.
Rules & Detections
This Security Operations console page lets you enable curated detections and create custom rules to identify patterns in data collected using the Security Operations console log data collection mechanisms. For information about the curated detections available with Security Command Center Enterprise, see Investigate threats with curated detections.
SIEM dashboards
This Security Operations console page lets you view Google Security Operations SIEM dashboards to analyze alerts created by Google Security Operations rules and data collected using the Security Operations console log data collection capabilities.
For more information about using SIEM dashboards, see Dashboards overview in Google Security Operations documentation.
SIEM search
This Security Operations console page lets you find Unified Data Model (UDM) events and alerts within your Google Security Operations instance. For more information, see SIEM search in Google Security Operations documentation.
SIEM settings
This Security Operations console page lets you change the configuration for features related to Google Security Operations SIEM. For information about using these features, see Google Security Operations documentation.
SOAR dashboards
This Security Operations console page lets you view and create dashboards using SOAR data that can be used to analyze responses and cases. For more information about using SOAR dashboards, see SOAR Dashboard Overview in Google Security Operations documentation.
SOAR reports
This Security Operations console page lets you view reports against SOAR data. For more information about using SOAR reports, see Understanding SOAR Reports in Google Security Operations documentation.
SOAR search
This Security Operations console page lets you find specific cases or entities indexed by Google Security Operations SOAR. For more information, see Work with the Search page in SOAR in Google Security Operations documentation.
SOAR settings
This Security Operations console page lets you change the configuration for features related to Google Security Operations SOAR. For information about using these features, see Google Security Operations documentation.
What's next
- Learn about detection services.
- Learn how to use security marks.
- Learn how to configure Security Command Center services.
