This page gives an overview of private pools and explains its features. If you're new to Cloud Build, read Cloud Build overview.
Overview of default pools and private pools
By default, when you run a build on Cloud Build, the build runs in a secure, hosted environment with access to the public internet. Each build runs on its own worker and is isolated from other workloads. You can customize your build in multiple ways including increasing the size of the machine type or allocating more disk space. The default pool has limits on how much you can customize the environment, particularly around private network access.
Private pools are private, dedicated pools of workers that offer greater customization over the build environment, including the ability to access resources in a private network. Private pools, similar to default pools, are hosted and fully-managed by Cloud Build and scale up and down to zero, with no infrastructure to set up, upgrade, or scale. Because private pools are customer-specific resources, you can configure them in more ways.
The following tables compares the features of the default pool with a private pool:
| Feature | Default pool | Private pool |
|---|---|---|
| Fully managed | ||
| Pay per build minute | ||
| Auto scaling, scales to 0 | ||
| Access to public internet | Configurable | |
| Peer into a VPC or shared VPC to access private resources | ||
| VPC Service Controls support | ||
| Static internal IP ranges | ||
| Ability to disable public IPs | ||
| Maximum concurrent builds | 30 | 100+ |
| Machine types | 5 | 64 |
| Regions | global, supported regions | supported regions |
| Region in which the build is run | The build runs in the region specified in gcloud builds submit or in the Google Cloud console triggers page. |
The build runs in the region where you create the private pool. |
Network architecture
Private pool is a fully-managed resource created by a user in a Google Cloud project. Private pools can be created, updated, and deleted via API, Google Cloud CLI, Google Cloud console, or managed via infrastructure provisioning tools such as Terraform.
Using Identity and Access Management permissions, builds run on private pools can be submitted cross project; that is builds don't have to originate from the same project as the private pool. Likewise, the service account the build runs as can be configured to allow workers to access resources from other Google Cloud projects during a build.
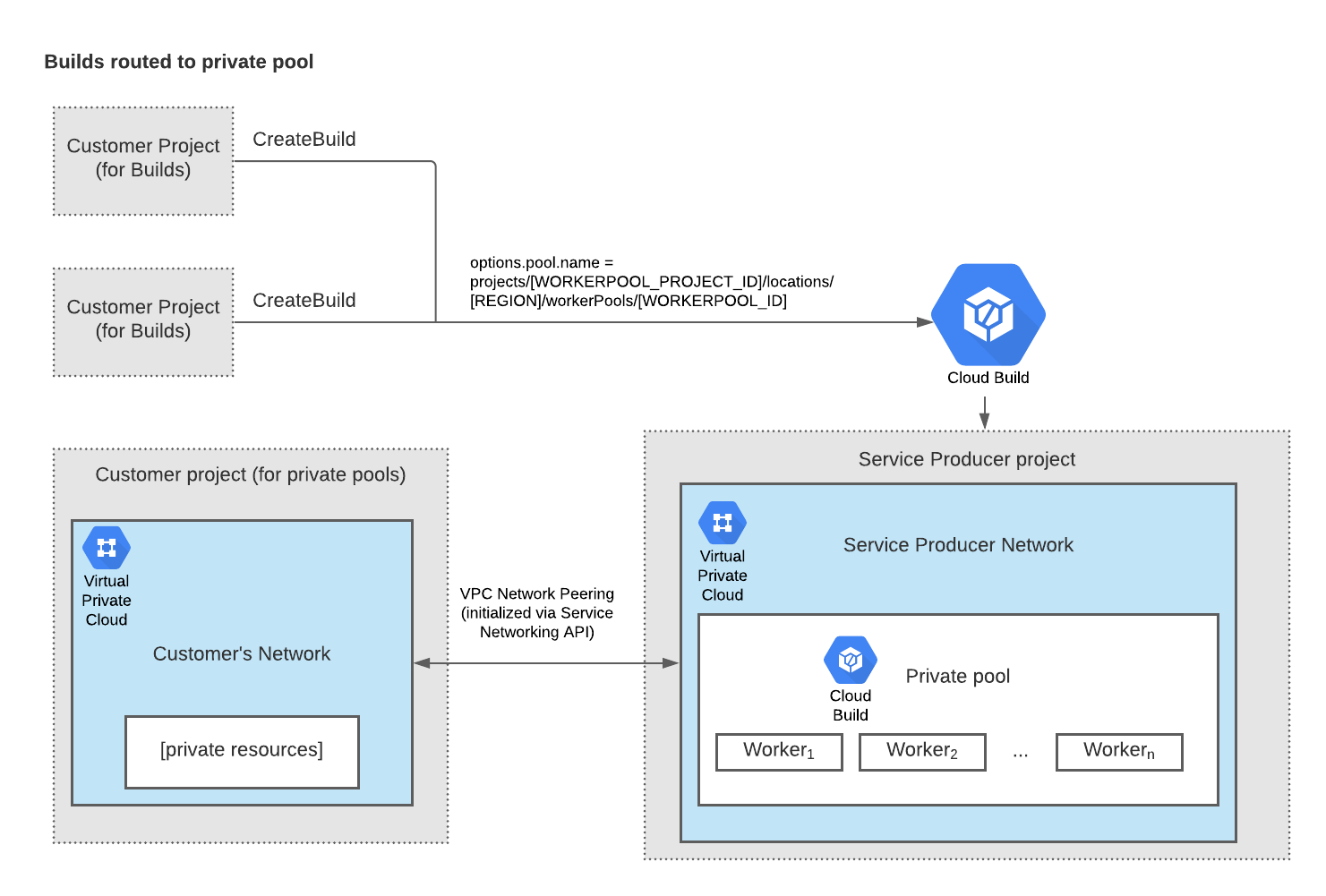
Private pools are hosted in a Google-owned service producer network that comes with internal IP addresses. For your builds to access resources in your private network, you can create a private VPC peering connection between your VPC network and the service producer network.
The following diagram shows how builds are routed to the private pool. In this setup, the customer has two projects sending builds to Cloud Build. The customer has configured all the builds from these projects to be routed to their private pool. The service producer network, where the private pool is in, is peered to the customer's VPC network giving the builds access to private resources in the customer's VPC network.
What's next
- Learn how to set up your environment to create private pools.
- Learn how to create and manage private pools.
- Learn how to configure commonly used networking use cases.
- Learn how to use VPC Service Controls with private pools.
