Mengumpulkan data Microsoft Windows AD
Dokumen ini mencakup informasi berikut:
- Arsitektur deployment dan langkah-langkah penginstalan, serta konfigurasi yang diperlukan yang menghasilkan log yang didukung oleh parser Google Security Operations untuk peristiwa Microsoft Windows Active Directory. Untuk ringkasan penyerapan data Google Security Operations, lihat Penyerapan data ke Google Security Operations.
- Informasi tentang cara parser memetakan kolom dalam log asli ke kolom Unified Data Model Google Security Operations.
Berdasarkan arsitektur deployment Anda, konfigurasikan agen Bindplane atau agen NXLog untuk menyerap log Microsoft Windows Active Directory ke Google Security Operations. Sebaiknya gunakan Agen Bindplane untuk meneruskan log Windows Active Directory ke Google Security Operations.
Informasi dalam dokumen ini berlaku untuk parser dengan label transfer WINDOWS_AD. Label penyerapan mengidentifikasi parser yang menormalisasi data log mentah ke format UDM terstruktur.
Sebelum memulai
Sebelum mengonfigurasi agen Bindplane atau Agen NXLog, selesaikan tugas berikut:
- Konfigurasikan semua sistem untuk menggunakan zona waktu UTC.
- Mengonfigurasi server Microsoft Windows AD.
- Tinjau perangkat dan versi yang didukung.
- Tinjau jenis log yang didukung.
Mengonfigurasi server AD Microsoft Windows
Di setiap server Microsoft Windows Active Directory, buat dan konfigurasikan skrip PowerShell untuk menyimpan data log ke file output. Agen Bindplane atau Agen NXLog membaca file output.
# Set the location where the log file will be written $OUTPUT_FILENAME="<Path_of_the_output_file>" If (Test-Path -Path $OUTPUT_FILENAME) { Remove-Item -path $OUTPUT_FILENAME -ErrorAction SilentlyContinue} # USER_CONTEXT: Gets all Active Directory users and their properties. Get-ADUser -Filter * -properties samAccountName | % { Get-ADUser $_.SamAccountName -properties * | ConvertTo-JSON -compress | Out-File -encoding utf8 $OUTPUT_FILENAME -Append } # ASSET_CONTEXT: Gets all Active Directory assets and their properties. Get-ADComputer -Filter * -properties samAccountName | % { Get-ADComputer $_.SamAccountName -properties * | ConvertTo-JSON -compress | Out-File -encoding utf8 $OUTPUT_FILENAME -Append }Ganti kode berikut :
- Ganti nilai
$OUTPUT_FILENAMEdengan lokasi file output. - Simpan data dalam format JSON.
- Tetapkan encoding ke UTF-8.
- Gunakan parameter
-Filter, bukan parameter-LDAPFilter, saat memanggil cmdletGet-ADUserdanGet-ADComputer.
- Ganti nilai
Buat tugas berulang yang menjalankan skrip untuk mengambil dan menulis data ke file output.
- Buka aplikasi Task Scheduler.
- Klik Create task.
- Masukkan nama dan deskripsi tugas.
- Centang kotak Run with highest privileges untuk memastikan semua data diambil.
- Di tab Triggers, tentukan kapan Anda ingin mengulangi tugas.
- Di tab Action, tambahkan tindakan baru dan berikan jalur file tempat skrip disimpan.
Meninjau perangkat dan versi yang didukung
Microsoft Windows Server dirilis dengan edisi berikut: Foundation, Essentials, Standar, dan Datacenter. Skema peristiwa log yang dihasilkan oleh setiap edisi tidak berbeda.
Parser Google Security Operations mendukung log dari versi server Microsoft Windows berikut:
- Microsoft Windows Server 2019
- Microsoft Windows Server 2016
- Microsoft Windows Server 2012
Parser Google Security Operations mendukung log yang dikumpulkan oleh NXLog Community Edition atau Enterprise Edition.
Meninjau jenis log yang didukung
Parser Google Security Operations akan mengurai dan menormalisasi data yang diambil dari Konteks Pengguna dan Konteks Aset. Fitur ini mendukung log yang dibuat dengan teks bahasa Inggris dan tidak mendukung log yang dibuat dalam bahasa non-Inggris.
Mengonfigurasi agen Bindplane
Sebaiknya gunakan agen Bindplane untuk meneruskan log Windows Active Directory ke Google Security Operations.
Setelah penginstalan, layanan agen Bindplane akan muncul sebagai layanan observIQ dalam daftar layanan Windows.
- Instal agen Bindplane di setiap server Windows Active Directory. Untuk informasi selengkapnya tentang cara menginstal agen Bindplane, lihat petunjuk penginstalan Agen Bindplane.
Buat file konfigurasi untuk agen Bindplane dengan konten berikut:
receivers: filelog: include: [ `FILE_PATH` ] operators: - type: json_parser start_at: beginning windowseventlog/activedirectoryservice: channel: Directory Service raw: true processors: batch: exporters: chronicle/activedirectory: endpoint: https://malachiteingestion-pa.googleapis.com creds: '{ "type": "service_account", "project_id": "malachite-projectname", "private_key_id": `PRIVATE_KEY_ID`, "private_key": `PRIVATE_KEY`, "client_email":"`SERVICE_ACCOUNT_NAME`@malachite-`PROJECT_ID`.", "client_id": `CLIENT_ID`, "auth_uri": "https://accounts.google.com/o/oauth2/auth", "token_uri": "https://oauth2.googleapis.com/token", "auth_provider_x509_cert_url":"https://www.googleapis.com/oauth2/v1/certs", "client_x509_cert_url": "https://www.googleapis.com/robot/v1/metadata/x509/`SERVICSERVICE_ACCOUNT_NAME`%40malachite-`PROJECT_ID`.", "universe_domain": "googleapis.com" }' log_type: 'WINDOWS_AD' override_log_type: false raw_log_field: body customer_id: `CUSTOMER_ID` service: pipelines: logs/ads: receivers: - filelog - windowseventlog/activedirectoryservice processors: [batch] exporters: [chronicle/activedirectory]Ganti kode berikut :
FILE_PATHdengan jalur file tempat output skrip PowerShell yang disebutkan di Mengonfigurasi server AD Microsoft Windows telah disimpan.PRIVATE_KEY_ID,PRIVATE_KEYSERVICSERVICE_ACCOUNT_NAME,PROJECT_ID,CLIENT_ID, danCUSTOMER_IDdengan nilai masing-masing dari file JSON akun layanan yang dapat Anda download dari Google Cloud. Untuk informasi selengkapnya tentang kunci akun layanan, lihat Membuat dan menghapus kunci akun layanan.
Untuk memulai layanan agen Bindplane (sebelumnya dikenal sebagai observIQ), pilih Layanan > Diperluas > Layanan observIQ > Mulai.
Mengonfigurasi Agen NXLog
Diagram berikut menunjukkan arsitektur tempat Agen NXLog diinstal untuk mengumpulkan dan mengirim peristiwa Microsoft Windows ke Google Security Operations. Bandingkan informasi ini dengan lingkungan Anda untuk memastikan komponen ini diinstal. Deployment Anda mungkin berbeda dari arsitektur ini dan mungkin lebih kompleks.
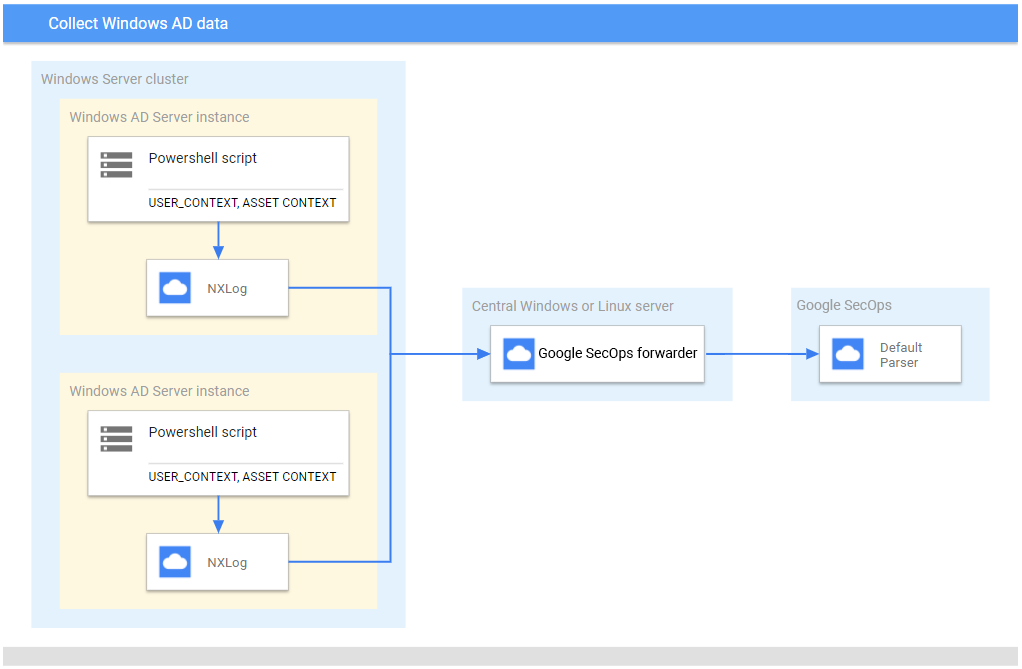
Jika Anda menggunakan agen NXLog, bukan agen Bindplane, verifikasi hal berikut:
- Skrip PowerShell dibuat dan dikonfigurasi di setiap Microsoft Windows Server yang menjalankan Active Directory untuk mengumpulkan data
USER_CONTEXTdanASSET_CONTEXT. Untuk informasi selengkapnya, lihat Mengonfigurasi server Microsoft Windows AD. - NXLog diinstal di setiap server AD Microsoft Windows untuk mengirim data ke server Linux atau Microsoft Windows Server pusat.
- Pengirim Google Security Operations diinstal di server Microsoft Windows Server atau Linux pusat untuk meneruskan data log ke Google Security Operations.
Mengonfigurasi NXLog
- Instal agen NXLog di setiap kolektor yang berjalan di server Windows Active Directory. Aplikasi ini meneruskan log ke server Microsoft Windows atau Linux pusat. Untuk mengetahui informasi selengkapnya, lihat dokumentasi NXLog.
Buat file konfigurasi untuk setiap instance NXLog. Gunakan modul
im_fileNXLog untuk membaca dari file dan mengurai baris menjadi kolom. Gunakanom_tcpuntuk meneruskan data ke server Microsoft Windows atau Linux pusat.Berikut adalah contoh konfigurasi NXLog. Ganti nilai
<hostname>dan<port>dengan informasi tentang Server Microsoft Windows atau Linux pusat tujuan. Di bagian<Input in_adcontext>dan propertiFile, tambahkan jalur file log output yang ditulis oleh skrip PowerShell. Selalu tetapkanDirCheckIntervaldanPollInterval. Jika tidak ditentukan, NXLog akan melakukan polling file setiap 1 detik.define ROOT C:\Program Files\nxlog define ADCONTEXT_OUTPUT_DESTINATION_ADDRESS <hostname> define ADCONTEXT_OUTPUT_DESTINATION_PORT <port> Moduledir %ROOT%\modules CacheDir %ROOT%\data Pidfile %ROOT%\data\nxlog.pid SpoolDir %ROOT%\data LogFile %ROOT%\data\nxlog.log <Input in_adcontext> Module im_file File "<Path_of_the_output_file>" DirCheckInterval 3600 PollInterval 3600 </Input> <Output out_chronicle_adcontext> Module om_tcp Host %ADCONTEXT_OUTPUT_DESTINATION_ADDRESS% Port %ADCONTEXT_OUTPUT_DESTINATION_PORT% </Output> <Route ad_context_to_chronicle> Path in_adcontext => out_chronicle_adcontext </Route>Mulai layanan NXLog di setiap sistem.
Mengonfigurasi penerusan di server pusat
Untuk informasi tentang cara menginstal dan mengonfigurasi forwarder di Linux, lihat Menginstal dan mengonfigurasi forwarder di Linux. Untuk informasi tentang cara menginstal dan mengonfigurasi forwarder di Microsoft Windows, lihat Menginstal dan mengonfigurasi forwarder di Microsoft Windows.
- Konfigurasikan sistem dengan zona waktu UTC.
- Instal penerusan Google Security Operations di server Microsoft Windows atau Linux pusat.
Konfigurasikan penerusan Google Security Operations untuk mengirim log ke Google Security Operations. Berikut adalah contoh konfigurasi penerus:
- syslog: common: enabled: true data_type: WINDOWS_AD batch_n_seconds: 10 batch_n_bytes: 1048576 tcp_address: 0.0.0.0:10518 connection_timeout_sec: 60
Format log Windows AD yang didukung
Parser AD Windows mendukung log dalam format JSON.
Log contoh Windows AD yang didukung
JSON:
{ "GivenName": "user1", "Surname": "itadmin", "UserPrincipalName": "user1.itadmin@testdhcp2.local", "Enabled": true, "SamAccountName": "user1.itadmin", "SID": { "BinaryLength": 28, "AccountDomainSid": { "BinaryLength": 24, "AccountDomainSid": "S-1-2-3", "Value": "S-1-2-3" }, "Value": "S-1-2-3-4000" }, "DistinguishedName": "CN=test,CN=Users,DC=testdhcp2,DC=local", "Name": "test", "ObjectClass": "user", "ObjectGuid": "4bde3f8d-8e9e-4ded-9d71-126ba9cd1300", "PropertyNames": [ "AccountExpirationDate", "accountExpires", "AccountLockoutTime", "AccountNotDelegated", "AllowReversiblePasswordEncryption", "AuthenticationPolicy", "AuthenticationPolicySilo", "BadLogonCount", "badPasswordTime", "badPwdCount", "c", "CannotChangePassword", "CanonicalName", "Certificates", "City", "CN", "co", "codePage", "Company", "CompoundIdentitySupported", "Country", "countryCode", "Created", "createTimeStamp", "Deleted", "Department", "Description", "DisplayName", "DistinguishedName", "Division", "DoesNotRequirePreAuth", "dSCorePropagationData", "EmailAddress", "EmployeeID", "EmployeeNumber", "Enabled", "facsimileTelephoneNumber", "Fax", "GivenName", "HomeDirectory", "HomedirRequired", "HomeDrive", "HomePage", "HomePhone", "Initials", "instanceType", "ipPhone", "isDeleted", "KerberosEncryptionType", "l", "LastBadPasswordAttempt", "LastKnownParent", "lastLogoff", "lastLogon", "LastLogonDate", "lastLogonTimestamp", "LockedOut", "lockoutTime", "logonCount", "logonHours", "LogonWorkstations", "mail", "Manager", "MemberOf", "MNSLogonAccount", "mobile", "MobilePhone", "Modified", "modifyTimeStamp", "msDS-SupportedEncryptionTypes", "msDS-User-Account-Control-Computed", "Name", "nTSecurityDescriptor", "ObjectCategory", "ObjectClass", "ObjectGUID", "objectSid", "Office", "OfficePhone", "Organization", "OtherName", "pager", "PasswordExpired", "PasswordLastSet", "PasswordNeverExpires", "PasswordNotRequired", "physicalDeliveryOfficeName", "POBox", "PostalCode", "postOfficeBox", "PrimaryGroup", "primaryGroupID", "PrincipalsAllowedToDelegateToAccount", "ProfilePath", "ProtectedFromAccidentalDeletion", "pwdLastSet", "SamAccountName", "sAMAccountType", "ScriptPath", "sDRightsEffective", "ServicePrincipalNames", "SID", "SIDHistory", "SmartcardLogonRequired", "sn", "st", "State", "StreetAddress", "Surname", "telephoneNumber", "Title", "TrustedForDelegation", "TrustedToAuthForDelegation", "UseDESKeyOnly", "userAccountControl", "userCertificate", "userParameters", "UserPrincipalName", "uSNChanged", "uSNCreated", "whenChanged", "whenCreated", "wWWHomePage" ], "AddedProperties": [], "RemovedProperties": [], "ModifiedProperties": [], "PropertyCount": 123, "AccountExpirationDate": null, "accountExpires": 0, "AccountLockoutTime": "\\/Date(1631175863106)\\/", "AccountNotDelegated": true, "AllowReversiblePasswordEncryption": false, "AuthenticationPolicy": [], "AuthenticationPolicySilo": [], "BadLogonCount": 3, "badPasswordTime": 132756494631068585, "badPwdCount": 3, "c": "IN", "CannotChangePassword": false, "CanonicalName": "testdhcp2.local/Users/test", "Certificates": [], "City": "Ahmedabad", "CN": "test", "co": "India", "codePage": 0, "Company": "user", "CompoundIdentitySupported": [ false ], "Country": "IN", "countryCode": 356, "Created": "\\/Date(1628229355000)\\/", "createTimeStamp": "\\/Date(1628229355000)\\/", "Deleted": null, "Department": "it", "Description": "itadmin", "DisplayName": "user1", "Division": "test", "DoesNotRequirePreAuth": false, "dSCorePropagationData": [ "\\/Date(1631191510000)\\/", "\\/Date(-11644473600000)\\/" ], "EmailAddress": "user@dummy.local", "EmployeeID": null, "EmployeeNumber": null, "facsimileTelephoneNumber": "12345678", "Fax": "12345678", "HomeDirectory": "\\\\\\\\DHCP-AD01\\\\ADContext", "HomedirRequired": false, "HomeDrive": "G:", "HomePage": "www.test.com", "HomePhone": "123456789", "Initials": "user1", "instanceType": 4, "ipPhone": "1121", "isDeleted": null, "KerberosEncryptionType": [ 0 ], "l": "ahmedabad", "LastBadPasswordAttempt": "\\/Date(1631175863106)\\/", "LastKnownParent": null, "lastLogoff": 0, "lastLogon": 132756492460689244, "LastLogonDate": "\\/Date(1631175025098)\\/", "lastLogonTimestamp": 132756486250985369, "LockedOut": false, "lockoutTime": 132756494631068585, "logonCount": 2, "logonHours": [ 0, 0, 248, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 7, 0, 0, 0, 0, 0, 0 ], "LogonWorkstations": null, "mail": "user@dummy.local", "Manager": "CN=Administrator,CN=Users,DC=testdhcp2,DC=local", "MemberOf": [ "CN=Netwrix Auditor Client Users,CN=Users,DC=dnstest2,DC=local", "CN=Netwrix Auditor Administrators,CN=Users,DC=dnstest2,DC=local", "CN=Group Policy Creator Owners,CN=Users,DC=dnstest2,DC=local", "CN=Domain Admins,CN=Users,DC=dnstest2,DC=local", "CN=Enterprise Admins,CN=Users,DC=dnstest2,DC=local", "CN=Schema Admins,CN=Users,DC=dnstest2,DC=local", "CN=Remote Desktop Users,CN=Builtin,DC=dnstest2,DC=local", "CN=Administrators,CN=Builtin,DC=dnstest2,DC=local" ], "MNSLogonAccount": false, "mobile": "923456789", "MobilePhone": "823456789", "Modified": "\\/Date(1631277960000)\\/", "modifyTimeStamp": "\\/Date(1631277960000)\\/", "msDS-SupportedEncryptionTypes": 0, "msDS-User-Account-Control-Computed": 0, "nTSecurityDescriptor": { "AccessRightType": { "Module": "System.DirectoryServices.dll", "Assembly": "System.DirectoryServices, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a", "TypeHandle": "System.RuntimeTypeHandle", "DeclaringMethod": null, "BaseType": "System.Enum", "UnderlyingSystemType": "System.DirectoryServices.ActiveDirectoryRights", "FullName": "System.DirectoryServices.ActiveDirectoryRights", "AssemblyQualifiedName": "System.DirectoryServices.ActiveDirectoryRights, System.DirectoryServices, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a", "Namespace": "System.DirectoryServices", "GUID": "f65acb9b-4c77-33ff-8523-43e9cc2c5798", "IsEnum": true, "GenericParameterAttributes": null, "IsSecurityCritical": false, "IsSecuritySafeCritical": false, "IsSecurityTransparent": true, "IsGenericTypeDefinition": false, "IsGenericParameter": false, "GenericParameterPosition": null, "IsGenericType": false, "IsConstructedGenericType": false, "ContainsGenericParameters": false, "StructLayoutAttribute": "System.Runtime.InteropServices.StructLayoutAttribute", "Name": "ActiveDirectoryRights", "MemberType": 32, "DeclaringType": null, "ReflectedType": null, "MetadataToken": 33554438, "GenericTypeParameters": "", "DeclaredConstructors": "", "DeclaredEvents": "", "DeclaredFields": "Int32 value__ System.DirectoryServices.ActiveDirectoryRights Delete System.DirectoryServices.ActiveDirectoryRights ReadControl System.DirectoryServices.ActiveDirectoryRights WriteDacl System.DirectoryServices.ActiveDirectoryRights WriteOwner System.DirectoryServices.ActiveDirectoryRights Synchronize System.DirectoryServices.ActiveDirectoryRights AccessSystemSecurity System.DirectoryServices.ActiveDirectoryRights GenericRead System.DirectoryServices.ActiveDirectoryRights GenericWrite System.DirectoryServices.ActiveDirectoryRights GenericExecute System.DirectoryServices.ActiveDirectoryRights GenericAll System.DirectoryServices.ActiveDirectoryRights CreateChild System.DirectoryServices.ActiveDirectoryRights DeleteChild System.DirectoryServices.ActiveDirectoryRights ListChildren System.DirectoryServices.ActiveDirectoryRights Self System.DirectoryServices.ActiveDirectoryRights ReadProperty System.DirectoryServices.ActiveDirectoryRights WriteProperty System.DirectoryServices.ActiveDirectoryRights DeleteTree System.DirectoryServices.ActiveDirectoryRights ListObject System.DirectoryServices.ActiveDirectoryRights ExtendedRight", "DeclaredMembers": "Int32 value__ System.DirectoryServices.ActiveDirectoryRights Delete System.DirectoryServices.ActiveDirectoryRights ReadControl System.DirectoryServices.ActiveDirectoryRights WriteDacl System.DirectoryServices.ActiveDirectoryRights WriteOwner System.DirectoryServices.ActiveDirectoryRights Synchronize System.DirectoryServices.ActiveDirectoryRights AccessSystemSecurity System.DirectoryServices.ActiveDirectoryRights GenericRead System.DirectoryServices.ActiveDirectoryRights GenericWrite System.DirectoryServices.ActiveDirectoryRights GenericExecute System.DirectoryServices.ActiveDirectoryRights GenericAll System.DirectoryServices.ActiveDirectoryRights CreateChild System.DirectoryServices.ActiveDirectoryRights DeleteChild System.DirectoryServices.ActiveDirectoryRights ListChildren System.DirectoryServices.ActiveDirectoryRights Self System.DirectoryServices.ActiveDirectoryRights ReadProperty System.DirectoryServices.ActiveDirectoryRights WriteProperty System.DirectoryServices.ActiveDirectoryRights DeleteTree System.DirectoryServices.ActiveDirectoryRights ListObject System.DirectoryServices.ActiveDirectoryRights ExtendedRight", "DeclaredMethods": "", "DeclaredNestedTypes": "", "DeclaredProperties": "", "ImplementedInterfaces": "System.IComparable System.IFormattable System.IConvertible", "TypeInitializer": null, "IsNested": false, "Attributes": 257, "IsVisible": true, "IsNotPublic": false, "IsPublic": true, "IsNestedPublic": false, "IsNestedPrivate": false, "IsNestedFamily": false, "IsNestedAssembly": false, "IsNestedFamANDAssem": false, "IsNestedFamORAssem": false, "IsAutoLayout": true, "IsLayoutSequential": false, "IsExplicitLayout": false, "IsClass": false, "IsInterface": false, "IsValueType": true, "IsAbstract": false, "IsSealed": true, "IsSpecialName": false, "IsImport": false, "IsSerializable": true, "IsAnsiClass": true, "IsUnicodeClass": false, "IsAutoClass": false, "IsArray": false, "IsByRef": false, "IsPointer": false, "IsPrimitive": false, "IsCOMObject": false, "HasElementType": false, "IsContextful": false, "IsMarshalByRef": false, "GenericTypeArguments": "", "CustomAttributes": "[System.FlagsAttribute()]" }, "AccessRuleType": { "Module": "System.DirectoryServices.dll", "Assembly": "System.DirectoryServices, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a", "TypeHandle": "System.RuntimeTypeHandle", "DeclaringMethod": null, "BaseType": "System.Security.AccessControl.ObjectAccessRule", "UnderlyingSystemType": "System.DirectoryServices.ActiveDirectoryAccessRule", "FullName": "System.DirectoryServices.ActiveDirectoryAccessRule", "AssemblyQualifiedName": "System.DirectoryServices.ActiveDirectoryAccessRule, System.DirectoryServices, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a", "Namespace": "System.DirectoryServices", "GUID": "0db7ea8c-53d9-3d6d-8b09-bb209cf0d0ae", "IsEnum": false, "GenericParameterAttributes": null, "IsSecurityCritical": false, "IsSecuritySafeCritical": false, "IsSecurityTransparent": true, "IsGenericTypeDefinition": false, "IsGenericParameter": false, "GenericParameterPosition": null, "IsGenericType": false, "IsConstructedGenericType": false, "ContainsGenericParameters": false, "StructLayoutAttribute": "System.Runtime.InteropServices.StructLayoutAttribute", "Name": "ActiveDirectoryAccessRule", "MemberType": 32, "DeclaringType": null, "ReflectedType": null, "MetadataToken": 33554445, "GenericTypeParameters": "", "DeclaredConstructors": "Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.DirectoryServices.ActiveDirectorySecurityInheritance) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.Guid, System.DirectoryServices.ActiveDirectorySecurityInheritance) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.DirectoryServices.ActiveDirectorySecurityInheritance, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.Guid, System.DirectoryServices.ActiveDirectorySecurityInheritance, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, Int32, System.Security.AccessControl.AccessControlType, System.Guid, Boolean, System.Security.AccessControl.InheritanceFlags, System.Security.AccessControl.PropagationFlags, System.Guid)", "DeclaredEvents": "", "DeclaredFields": "", "DeclaredMembers": "System.DirectoryServices.ActiveDirectoryRights get_ActiveDirectoryRights() System.DirectoryServices.ActiveDirectorySecurityInheritance get_InheritanceType() Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.DirectoryServices.ActiveDirectorySecurityInheritance) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.Guid, System.DirectoryServices.ActiveDirectorySecurityInheritance) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.DirectoryServices.ActiveDirectorySecurityInheritance, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AccessControlType, System.Guid, System.DirectoryServices.ActiveDirectorySecurityInheritance, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, Int32, System.Security.AccessControl.AccessControlType, System.Guid, Boolean, System.Security.AccessControl.InheritanceFlags, System.Security.AccessControl.PropagationFlags, System.Guid) System.DirectoryServices.ActiveDirectoryRights ActiveDirectoryRights System.DirectoryServices.ActiveDirectorySecurityInheritance InheritanceType", "DeclaredMethods": "System.DirectoryServices.ActiveDirectoryRights get_ActiveDirectoryRights() System.DirectoryServices.ActiveDirectorySecurityInheritance get_InheritanceType()", "DeclaredNestedTypes": "", "DeclaredProperties": "System.DirectoryServices.ActiveDirectoryRights ActiveDirectoryRights System.DirectoryServices.ActiveDirectorySecurityInheritance InheritanceType", "ImplementedInterfaces": "", "TypeInitializer": null, "IsNested": false, "Attributes": 1048577, "IsVisible": true, "IsNotPublic": false, "IsPublic": true, "IsNestedPublic": false, "IsNestedPrivate": false, "IsNestedFamily": false, "IsNestedAssembly": false, "IsNestedFamANDAssem": false, "IsNestedFamORAssem": false, "IsAutoLayout": true, "IsLayoutSequential": false, "IsExplicitLayout": false, "IsClass": true, "IsInterface": false, "IsValueType": false, "IsAbstract": false, "IsSealed": false, "IsSpecialName": false, "IsImport": false, "IsSerializable": false, "IsAnsiClass": true, "IsUnicodeClass": false, "IsAutoClass": false, "IsArray": false, "IsByRef": false, "IsPointer": false, "IsPrimitive": false, "IsCOMObject": false, "HasElementType": false, "IsContextful": false, "IsMarshalByRef": false, "GenericTypeArguments": "", "CustomAttributes": "" }, "AuditRuleType": { "Module": "System.DirectoryServices.dll", "Assembly": "System.DirectoryServices, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a", "TypeHandle": "System.RuntimeTypeHandle", "DeclaringMethod": null, "BaseType": "System.Security.AccessControl.ObjectAuditRule", "UnderlyingSystemType": "System.DirectoryServices.ActiveDirectoryAuditRule", "FullName": "System.DirectoryServices.ActiveDirectoryAuditRule", "AssemblyQualifiedName": "System.DirectoryServices.ActiveDirectoryAuditRule, System.DirectoryServices, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a", "Namespace": "System.DirectoryServices", "GUID": "4ad0312a-2ed0-3526-97ec-f9c6f310c5e0", "IsEnum": false, "GenericParameterAttributes": null, "IsSecurityCritical": false, "IsSecuritySafeCritical": false, "IsSecurityTransparent": true, "IsGenericTypeDefinition": false, "IsGenericParameter": false, "GenericParameterPosition": null, "IsGenericType": false, "IsConstructedGenericType": false, "ContainsGenericParameters": false, "StructLayoutAttribute": "System.Runtime.InteropServices.StructLayoutAttribute", "Name": "ActiveDirectoryAuditRule", "MemberType": 32, "DeclaringType": null, "ReflectedType": null, "MetadataToken": 33554453, "GenericTypeParameters": "", "DeclaredConstructors": "Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.DirectoryServices.ActiveDirectorySecurityInheritance) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.Guid, System.DirectoryServices.ActiveDirectorySecurityInheritance) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.DirectoryServices.ActiveDirectorySecurityInheritance, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.Guid, System.DirectoryServices.ActiveDirectorySecurityInheritance, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, Int32, System.Security.AccessControl.AuditFlags, System.Guid, Boolean, System.Security.AccessControl.InheritanceFlags, System.Security.AccessControl.PropagationFlags, System.Guid)", "DeclaredEvents": "", "DeclaredFields": "", "DeclaredMembers": "System.DirectoryServices.ActiveDirectoryRights get_ActiveDirectoryRights() System.DirectoryServices.ActiveDirectorySecurityInheritance get_InheritanceType() Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.DirectoryServices.ActiveDirectorySecurityInheritance) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.Guid, System.DirectoryServices.ActiveDirectorySecurityInheritance) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.DirectoryServices.ActiveDirectorySecurityInheritance, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, System.DirectoryServices.ActiveDirectoryRights, System.Security.AccessControl.AuditFlags, System.Guid, System.DirectoryServices.ActiveDirectorySecurityInheritance, System.Guid) Void .ctor(System.Security.Principal.IdentityReference, Int32, System.Security.AccessControl.AuditFlags, System.Guid, Boolean, System.Security.AccessControl.InheritanceFlags, System.Security.AccessControl.PropagationFlags, System.Guid) System.DirectoryServices.ActiveDirectoryRights ActiveDirectoryRights System.DirectoryServices.ActiveDirectorySecurityInheritance InheritanceType", "DeclaredMethods": "System.DirectoryServices.ActiveDirectoryRights get_ActiveDirectoryRights() System.DirectoryServices.ActiveDirectorySecurityInheritance get_InheritanceType()", "DeclaredNestedTypes": "", "DeclaredProperties": "System.DirectoryServices.ActiveDirectoryRights ActiveDirectoryRights System.DirectoryServices.ActiveDirectorySecurityInheritance InheritanceType", "ImplementedInterfaces": "", "TypeInitializer": null, "IsNested": false, "Attributes": 1048577, "IsVisible": true, "IsNotPublic": false, "IsPublic": true, "IsNestedPublic": false, "IsNestedPrivate": false, "IsNestedFamily": false, "IsNestedAssembly": false, "IsNestedFamANDAssem": false, "IsNestedFamORAssem": false, "IsAutoLayout": true, "IsLayoutSequential": false, "IsExplicitLayout": false, "IsClass": true, "IsInterface": false, "IsValueType": false, "IsAbstract": false, "IsSealed": false, "IsSpecialName": false, "IsImport": false, "IsSerializable": false, "IsAnsiClass": true, "IsUnicodeClass": false, "IsAutoClass": false, "IsArray": false, "IsByRef": false, "IsPointer": false, "IsPrimitive": false, "IsCOMObject": false, "HasElementType": false, "IsContextful": false, "IsMarshalByRef": false, "GenericTypeArguments": "", "CustomAttributes": "" }, "AreAccessRulesProtected": false, "AreAuditRulesProtected": false, "AreAccessRulesCanonical": true, "AreAuditRulesCanonical": true }, "ObjectCategory": "CN=Person,CN=Schema,CN=Configuration,DC=testdhcp2,DC=local", "ObjectGUID": "4bde3f8d-8e9e-4ded-9d71-126ba9cd1300", "objectSid": { "BinaryLength": 28, "AccountDomainSid": { "BinaryLength": 24, "AccountDomainSid": "S-1-2-3", "Value": "S-1-2-3" }, "Value": "S-1-2-3-4000m" }, "Office": "db office", "OfficePhone": "91-123456789", "Organization": null, "OtherName": null, "pager": "234567890", "PasswordExpired": false, "PasswordLastSet": "\\/Date(1631174951326)\\/", "PasswordNeverExpires": false, "PasswordNotRequired": false, "physicalDeliveryOfficeName": "db office", "POBox": "dummy", "PostalCode": "380015", "postOfficeBox": [ "dummy" ], "PrimaryGroup": "CN=Domain Users,CN=Users,DC=testdhcp2,DC=local", "primaryGroupID": 513, "PrincipalsAllowedToDelegateToAccount": [], "ProfilePath": null, "ProtectedFromAccidentalDeletion": false, "pwdLastSet": 132756485513268133, "sAMAccountType": 805306368, "ScriptPath": null, "sDRightsEffective": 15, "ServicePrincipalNames": [], "SIDHistory": [], "SmartcardLogonRequired": false, "sn": "itadmin", "st": "Gujarat", "State": "Gujarat", "StreetAddress": "1,user street ,dummy,dummy", "telephoneNumber": "91-123456789", "Title": "it admin", "TrustedForDelegation": false, "TrustedToAuthForDelegation": false, "UseDESKeyOnly": false, "userAccountControl": 1049088, "userCertificate": [], "userParameters": null, "uSNChanged": 57594, "uSNCreated": 32800, "whenChanged": "\\/Date(1631277960000)\\/", "whenCreated": "\\/Date(1628229355000)\\/", "wWWHomePage": "www.test.com" }
Referensi pemetaan kolom: kolom log perangkat ke kolom UDM
Bagian ini menjelaskan cara parser memetakan kolom log asli ke kolom Model Data Terpadu.
Referensi pemetaan kolom: WINDOWS_AD
Tabel berikut mencantumkan kolom log dari jenis log WINDOWS_AD dan kolom UDM yang sesuai.
| Log field | UDM mapping | Logic |
|---|---|---|
|
metadata.entity_type |
If the ObjectClass log field value is equal to user or is empty, then the metadata.entity_type UDM field is set to USER. Else, if the ObjectClass log field value is equal to computer, then the metadata.entity_type UDM field is set to ASSET. |
ObjectGuid |
entity.user.product_object_id |
If the ObjectClass log field value is equal to user or is empty, then if the ObjectGuid log field value is not empty, then the ObjectGuid log field is mapped to the entity.user.product_object_id UDM field. Else, if the ObjectClass log field value is equal to computer, then if the ObjectGuid log field value is not empty, then the ObjectGuid log field is mapped to the entity.asset.product_object_id UDM field. |
whenCreated |
metadata.creation_timestamp |
If the ObjectClass log field value is equal to user or is empty, then if the whenCreated log field value is not empty, then when_created is extracted from the whenCreated log field using a Grok pattern, and mapped to the entity.asset.attribute.creation_time UDM field. Else, if the ObjectClass log field value is equal to computer, then if the whenCreated log field value is not empty, then when_created is extracted from the whenCreated log field using a Grok pattern, and mapped to the metadata.creation_timestamp UDM field. Else, timestamp tz_left tz_right is extracted from the whenCreated log field using a Grok pattern, and mapped to the entity.asset.attribute.creation_time UDM field. |
DisplayName |
entity.user.user_display_name |
If the ObjectClass log field value is equal to user or is empty, then if the DisplayName log field value is not empty, then the DisplayName log field is mapped to the entity.user.user_display_name UDM field. |
GivenName |
entity.user.first_name |
If the ObjectClass log field value is equal to user or is empty, then if the GivenName log field value is not empty, then the GivenName log field is mapped to the entity.user.first_name UDM field. |
SamAccountName |
entity.user.userid |
If the ObjectClass log field value is equal to user or is empty, then if the SamAccountName log field value is not empty, then the SamAccountName log field is mapped to the entity.user.userid UDM field. If the ObjectClass log field value is equal to computer, then the SamAccountName log field is mapped to the entity.asset.asset_id UDM field. |
EmployeeID |
entity.user.employee_id |
If the EmployeeID log field value is not empty, then the EmployeeID log field is mapped to the entity.user.employee_id UDM field.Else the employeeID.0 log field is mapped to the entity.user.employee_id UDM field. |
Title |
entity.user.title |
If the Title log field value is not empty, then the Title log field is mapped to the entity.user.title UDM field. |
Surname |
entity.user.last_name |
If the ObjectClass log field value is equal to user or is empty, then if the Surname log field value is not empty, then if the sn log field is mapped to the entity.user.last_name UDM field. Else if Surname log field value is not empty, then the Surname log field is mapped to the entity.user.last_name UDM field. |
Company |
entity.user.company_name |
If the ObjectClass log field value is equal to user or is empty, then if the Company log field value is not empty, then the Company log field is mapped to the entity.user.company_name UDM field. |
City |
entity.user.personal_address.city |
If the ObjectClass log field value is equal to user or is empty, then if the City log field value is not empty, then the City log field is mapped to the entity.user.personal_address.city UDM field. |
Department |
entity.user.department |
If the ObjectClass log field value is equal to user or is empty, then if the Department log field value is not empty, then the Department log field is mapped to the entity.user.department UDM field. |
|
entity.user.email_addresses |
If the ObjectClass log field value is equal to user or is empty, then if the EmailAddress log field value is not empty, then the EmailAddress log field is mapped to the entity.user.email_addresses UDM field. Else, if the mail log field value is not empty, then the mail log field is mapped to the entity.user.email_addresses UDM field. |
HomePhone |
entity.user.phone_numbers |
If the ObjectClass log field value is equal to user or is empty, then if the HomePhone log field value is not empty, then the HomePhone log field is mapped to the entity.user.phone_numbers UDM field. Else if the telephoneNumber log field value is not empty, then the telephoneNumber log field is mapped to the entity.user.phone_numbers UDM field.
If the ObjectClass log field value is equal to user or is empty, then if the MobilePhone log field value is not empty, then the MobilePhone log field is mapped to the entity.user.phone_numbers UDM field.
If the ObjectClass log field value is equal to user or is empty, then if the otherMobile log field value is not empty, then the otherMobile log field is mapped to the entity.user.phone_numbers UDM field. |
StreetAddress |
entity.user.personal_address.name |
If the ObjectClass log field value is equal to user or is empty, then if the StreetAddress log field value is not empty, then the StreetAddress log field is mapped to the entity.user.personal_address.name UDM field. |
State |
entity.user.personal_address.state |
If the ObjectClass log field value is equal to user or is empty, then if the State log field value is not empty, then the State log field is mapped to the entity.user.personal_address.state UDM field. |
Country |
entity.user.personal_address.country_or_region |
If the ObjectClass log field value is equal to user or is empty, then if the Country log field value is not empty, then the Country log field is mapped to the entity.user.personal_address.country_or_region UDM field. |
Office |
entity.user.office_address.name |
If the ObjectClass log field value is equal to user or is empty, then if the Office log field value is not empty, then the Office log field is mapped to the entity.user.office_address.name UDM field. |
HomeDirectory |
entity.file.full_path |
If the ObjectClass log field value is equal to user or is empty, then if the HomeDirectory log field value is not empty, then the HomeDirectory log field is mapped to the entity.file.full_path UDM field. |
|
entity.user.managers.user_display_name |
If the ObjectClass log field value is equal to user or is empty, then if the Manager log field value is not empty, then manager_name is extracted from the Manager log field using a Grok pattern, and mapped to the entity.user.managers.user_display_name UDM field. |
|
entity.user.windows_sid |
If the SID.Value log field value is not empty, then the SID.Value field is mapped to the entity.user.windows_sid UDM field.Else, if the objectSid log field value is not empty, then the objectSid field is mapped to the entity.user.windows_sid UDM field.If the ObjectClass log field value is equal to user or is empty, then if the Manager log field value is not empty, then if Manager matches the regular expression pattern (S-\d-(\d+-){1,14}\d+), then the Manager log field is mapped to the entity.user.managers.windows_sid UDM field. Else, the Manager log field is mapped to the entity.user.managers.userid UDM field. |
|
relations.relationship |
If the ObjectClass log field value is equal to user or is empty, then if the MemberOf log field value is not empty, then for index in MemberOf, the relations.relationship UDM field is set to MEMBER. Else, if the ObjectClass log field value is equal to computer, then if the ManagedBy log field value is not empty, then the relations.relationship UDM field is set to ADMINISTERS.If the PrimaryGroup log field value is not empty, then group_name is extracted from the PrimaryGroup log field using a Grok pattern, if the group_name extracted field value is not empty, then the relations.relationship UDM field is set to MEMBER. |
|
relations.entity.group.group_display_name |
If the ObjectClass log field value is equal to user or is empty, then if the MemberOf log field value is not empty, then for index in MemberOf, group_name is extracted from the index using a Grok pattern and mapped to the relations.entity.group.group_display_name UDM field. If the PrimaryGroup log field value is not empty, then group_name is extracted from the PrimaryGroup log field using a Grok pattern and mapped to the relations.entity.group.group_display_name UDM field. |
|
relations.entity_type |
If the ObjectClass log field value is equal to user or is empty, then if the MemberOf log field value is not empty, then for index in MemberOf, the relations.entity_type UDM field is set to GROUP. Else, if the ObjectClass log field value is equal to computer, then if the ManagedBy log field value is not empty, then the relations.entity_type UDM field is set to ASSET.If the PrimaryGroup log field value is not empty, then group_name is extracted from the PrimaryGroup log field using a Grok pattern, if the group_name extracted field value is not empty, then the relations.entity_type UDM field is set to GROUP. |
|
relations.direction |
If the ObjectClass log field value is equal to user or is empty, then if the MemberOf log field value is not empty, then for index in MemberOf, the relations.direction UDM field is set to UNIDIRECTIONAL. Else, if the ObjectClass log field value is equal to computer, then if the ManagedBy log field value is not empty, then the relations.direction UDM field is set to UNIDIRECTIONAL.If the PrimaryGroup log field value is not empty, then group_name is extracted from the PrimaryGroup log field using a Grok pattern, if the group_name extracted field value is not empty, then the relations.direction UDM field is set to UNIDIRECTIONAL. |
|
relations.entity.user.user_display_name |
If the ObjectClass log field value is equal to computer, then if the ManagedBy log field value is not empty, then user_name is extracted from the ManagedBy log field using a Grok pattern and mapped to the relations.entity.user.user_display_name UDM field. |
proxyAddresses |
entity.user.group_identifiers |
If the ObjectClass log field value is equal to user or is empty, then for index in proxyAddresses the index is mapped to entity.user.group_identifiers UDM field. |
|
entity.user.attribute.labels[Bad Password Count] |
If the ObjectClass log field value is equal to user or is empty, then if the badPwdCount log field value is not empty, then the entity.user.attribute.labels.key UDM field is set to Bad Password Count and the badPwdCount log field is mapped to the entity.user.attribute.labels.value UDM field. |
LastBadPasswordAttempt |
entity.user.last_bad_password_attempt_time |
If the ObjectClass log field value is equal to user or is empty, then if the LastBadPasswordAttempt log field value is not empty, then last_bad_password_attempt is extracted from the LastBadPasswordAttempt log field using a Grok pattern and mapped to the entity.user.last_bad_password_attempt_time UDM field. Else, if the ObjectClass log field value is equal to computer, then last_bad_password_attempt is extracted from the LastBadPasswordAttempt log field using a Grok pattern and mapped to the entity.user.last_bad_password_attempt_time UDM field. |
AccountExpirationDate |
entity.user.account_expiration_time |
If the ObjectClass log field value is equal to user or is empty, then if the AccountExpirationDate log field value is not empty, then account_expiration_date is extracted from the AccountExpirationDate log field using a Grok pattern and mapped to the entity.user.account_expiration_time UDM field. Else, if the ObjectClass log field value is equal to computer, then if the AccountExpirationDate log field value is not empty, then account_expiration_date is extracted from the AccountExpirationDate log field using a Grok pattern and mapped to the entity.user.account_expiration_time UDM field. |
PasswordLastSet |
entity.user.last_password_change_time |
If the ObjectClass log field value is equal to user or is empty, then if the PasswordLastSet log field value is not empty, then password_last_set is extracted from the PasswordLastSet log field using a Grok pattern and mapped to the entity.user.last_password_change_time UDM field. Else, if the ObjectClass log field value is equal to computer, then if the PasswordLastSet log field value is not empty, then password_last_set is extracted from the PasswordLastSet log field using a Grok pattern and mapped to the entity.user.last_password_change_time UDM field. |
PasswordNotRequired |
entity.user.attribute.labels[Password Not Required] |
If the ObjectClass log field value is equal to user or is empty, then if the PasswordNotRequired log field value is not empty, then the PasswordNotRequired log field is mapped to the entity.user.attribute.labels.value UDM field. If the ObjectClass log field value is equal to computer, then if the PasswordNotRequired log field value is not empty, then the PasswordNotRequired log field is mapped to the entity.asset.attribute.labels.value UDM field. |
ServicePrincipalNames |
entity.user.attribute.labels[Service Principal Names] |
If the ObjectClass log field value is equal to user or is empty, then if ServicePrincipalNames log field value is not empty, then for index in ServicePrincipalNames the index is mapped to the entity.user.attribute.labels.value UDM field.Else, if the ObjectClass log field value is equal to computer, then if ServicePrincipalNames log field value is not empty, then for index in ServicePrincipalNames, if index is equal to 0, then the index is mapped to the entity.user.attribute.labels.value UDM field. |
AccountLockoutTime |
entity.user.account_lockout_time |
If the ObjectClass log field value is equal to user or is empty, then if the AccountLockoutTime log field value is not empty, then account_lockout_time is extracted from the AccountLockoutTime log field using a Grok pattern and mapped to the entity.user.account_lockout_time UDM field. Else, if the ObjectClass log field value is equal to computer, then if the AccountLockoutTime log field value is not empty, then account_lockout_time is extracted from the AccountLockoutTime log field using a Grok pattern and mapped to the entity.user.account_lockout_time UDM field. |
whenChanged |
entity.asset.attribute.last_update_time |
If the ObjectClass log field value is equal to computer, then when_changed is extracted from the whenChanged log field using a Grok pattern, if whenChanged is not empty, then when_changed is mapped to the entity.asset.attribute.last_update_time UDM field.Else, timestamp and timezone is extracted from whenChanged log field using a Grok pattern and tz_left and tz_right is extracted from the timezone using a Grok pattern and timestamp tz_left tz_right is mapped to entity.asset.attribute.creation_time UDM field. |
DNSHostName |
entity.asset.hostname |
If the ObjectClass log field value is equal to computer, then if the DNSHostName log field value is not empty, then the DNSHostName log field is mapped to the entity.asset.hostname UDM field. |
countryCode |
entity.asset.location.country_or_region |
If the ObjectClass log field value is equal to computer, then if the countryCode log field value is not empty, then the countryCode log field is mapped to the entity.asset.location.country_or_region UDM field. |
|
entity.asset.platform_software.platform |
If the ObjectClass log field value is equal to computer, then if the OperatingSystem log field value is not empty, then if the OperatingSystem log field value matches the regular expression pattern (?i)windows, then the entity.asset.platform_software.platform UDM field is set to WINDOWS.Else, if the OperatingSystem log field value matches the regular expression pattern (?i)mac or the OperatingSystem log field value matches the regular expression pattern (?i)osx, then the entity.asset.platform_software.platform UDM field is set to MAC.Else, if the OperatingSystem log field value matches the regular expression pattern (?i)linux, then the entity.asset.platform_software.platform UDM field is set to LINUX. |
OperatingSystemVersion |
entity.asset.platform_software.platform_version |
If the ObjectClass log field value is equal to computer, then if the OperatingSystem log field value is not empty, then if the OperatingSystemVersion log field value is not empty, then OperatingSystem - OperatingSystemVersion is mapped to the entity.asset.platform_software.platform_version UDM field.Else if the OperatingSystemVersion log field value is not empty, then the OperatingSystemVersion log field is mapped to the entity.asset.platform_software.platform_version UDM field. |
OperatingSystemServicePack |
entity.asset.platform_software.platform_patch_level |
If the ObjectClass log field value is equal to computer, then if the OperatingSystemServicePack log field value is not empty, then the OperatingSystemServicePack log field is mapped to the entity.asset.platform_software.platform_patch_level UDM field. |
IPv4Address |
entity.asset.ip |
If the ObjectClass log field value is equal to computer, then if the IPv4Address log field value is not empty, then the IPv4Address log field is mapped to the entity.asset.ip UDM field. |
IPv6Address |
entity.asset.ip |
If the ObjectClass log field value is equal to computer, then if the IPv6Address log field value is not empty, then the IPv6Address log field is mapped to the entity.asset.ip UDM field. |
Location |
entity.asset.location.name |
If the ObjectClass log field value is equal to computer, then if the Location log field value is not empty, then the Location log field is mapped to the entity.asset.location.name UDM field. |
ObjectCategory |
entity.asset.category |
If the ObjectClass log field value is equal to computer, then if the ObjectCategory log field value is not empty, then object_category is extracted from the ObjectCategory log field using a Grok pattern, and mapped to the entity.asset.category UDM field. |
PasswordExpired |
entity.asset.attribute.labels[Password Expired] |
If the ObjectClass log field value is equal to computer, then if the PasswordExpired log field value is not empty, then the PasswordExpired log field is mapped to the entity.asset.attribute.labels.value UDM field.If the ObjectClass log field value is equal to user or is empty, then if the PasswordExpired log field value is not empty, then the PasswordExpired log field is mapped to the entity.user.attribute.labels.value UDM field. |
PasswordNeverExpires |
entity.asset.attribute.labels[Password Never Expires] |
If the ObjectClass log field value is equal to computer, then if the PasswordNeverExpires log field value is not empty, then the PasswordNeverExpires log field is mapped to the entity.asset.attribute.labels.value UDM field.If the ObjectClass log field value is equal to user or is empty, then if the PasswordNeverExpires log field value is not empty, then the PasswordNeverExpires log field is mapped to the entity.user.attribute.labels.value UDM field. |
|
entity.user.attribute.labels[Last Logon] |
If the ObjectClass log field value is equal to user or is empty, then if the lastLogon log field value is not equal to 0, then the entity.user.attribute.labels.key UDM field is set to Last Logon and the lastLogon log field is mapped to the entity.user.attribute.labels.value UDM field. If the ObjectClass log field value is equal to computer, then if the lastLogon log field value is not equal to 0, then the entity.asset.attribute.labels.key UDM field is set to Last Logon and the lastLogon log field is mapped to the entity.asset.attribute.labels.value UDM field. |
lastLogoff |
entity.asset.attribute.labels[Last Logoff] |
If the ObjectClass log field value is equal to computer, then if the lastLogoff log field value does not contain one of the following values, then the lastLogoff log field is mapped to the entity.asset.attribute.labels.value UDM field.
|
LastLogonDate |
entity.user.last_login_time |
If the ObjectClass log field value is equal to user or is empty, then if the LastLogonDate log field value is not empty, then last_logon_date is extracted from the LastLogonDate log field using a Grok pattern, and mapped to the entity.user.last_login_time UDM field.Else if the ObjectClass log field value is equal to computer,then if the LastLogonDate log field value is not empty, then last_logon_date is extracted from the LastLogonDate log field using a Grok pattern, and mapped to the entity.user.last_login_time UDM field. |
HomePage |
entity.url |
If the HomePage log field value is not empty, then the HomePage log field is mapped to the entity.url UDM field. |
|
entity.administrative_domain |
If the CanonicalName log field value is not empty, then domain_name is extracted from the CanonicalName log field using a Grok pattern, and mapped to the entity.administrative_domain UDM field. |
|
metadata.vendor_name |
The metadata.vendor_name UDM field is set to Microsoft. |
|
metadata.product_name |
The metadata.product_name UDM field is set to Windows Active Directory. |
Description |
metadata.description |
The Description log field is mapped to the metadata.description UDM field. |
Perlu bantuan lain? Dapatkan jawaban dari anggota Komunitas dan profesional Google SecOps.

