É possível usar as condições do IAM para conceder acesso a portas de estações de trabalho individuais. Isso é útil para compartilhar acesso limitado a portas de estações de trabalho individuais. Por exemplo, é possível usar as condições do IAM para conceder acesso a um servidor de demonstração em execução em uma porta de estação de trabalho.
O Cloud Workstations é compatível com o atributo destination.port IAM Conditions.
Para mais informações sobre as condições do IAM, consulte os artigos a seguir:
Antes de começar
Antes de conceder acesso a portas individuais da estação de trabalho, você precisa ter o papel de
Administrador de políticas do Cloud Workstations
(roles/workstations.policyAdmin) na estação de trabalho.
Verificar os papéis do IAM na estação de trabalho
Verifique se você tem os papéis Usuário do Cloud Workstations (roles/workstations.user) e
Administrador de políticas do Cloud Workstations (roles/workstations.policyAdmin)
na estação de trabalho. Caso contrário, peça ao administrador do Cloud Workstations da sua organização para conceder esses papéis a você na estação de trabalho.
Iniciar um servidor de demonstração na estação de trabalho
Inicie e conecte-se às suas estações de trabalho usando o guia Iniciar estação de trabalho. Execute o seguinte comando na estação de trabalho para iniciar um servidor de demonstração em uma porta da estação de trabalho.
python3 -m http.server WORKSTATIONS_PORT
Substitua:
WORKSTATIONS_PORT: a porta em que o servidor de demonstração vai detectar. Por exemplo, use 8081.
Atualizar a política condicional do IAM da estação de trabalho
Para conceder acesso a uma porta de estação de trabalho, use o console do Google Cloud ou o comando
iam policies da CLI gcloud.
Console
Para conceder acesso condicional à estação de trabalho:
No Google Cloud console, navegue até a página Cloud Workstations > Workstations.
Encontre sua estação de trabalho, clique no menu de opções more_vertMais e selecione Adicionar usuários.
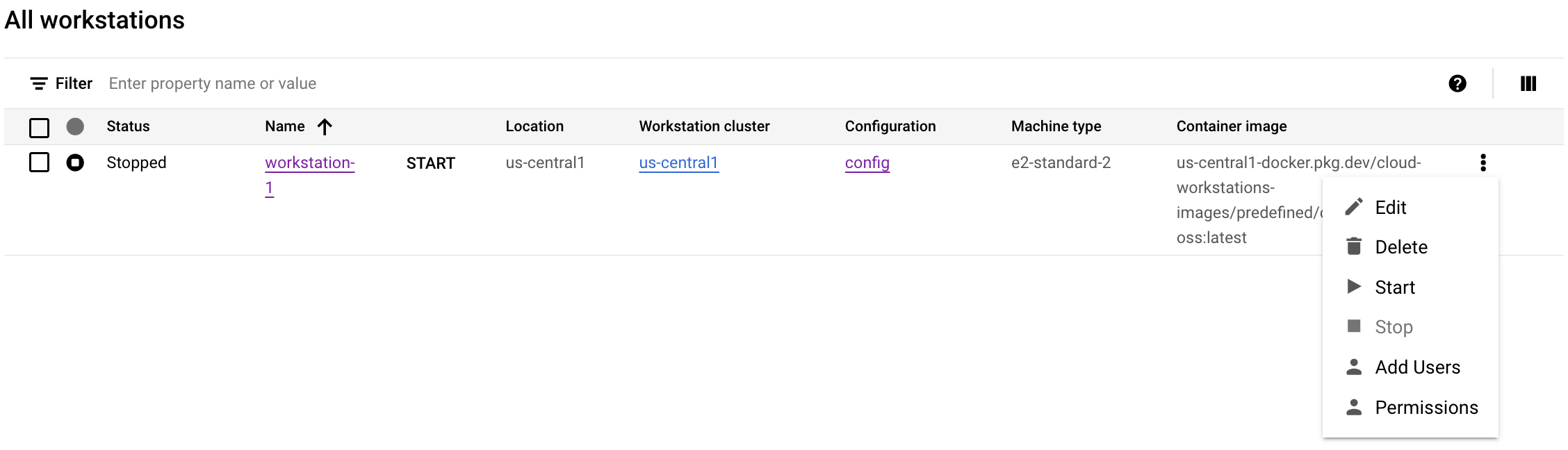
Para conceder acesso condicional, insira o e-mail do principal. Por exemplo,
222larabrown@gmail.com.Confira se Usuário do Cloud Workstations está selecionado como uma função.
Atualize a condição do IAM para conceder acesso específico à porta:
Clique em Adicionar condição do IAM.
Especifique um título como Porta WORKSTATIONS_PORT.
Na guia Editor da condição, insira a seguinte condição:
destination.port == WORKSTATIONS_PORT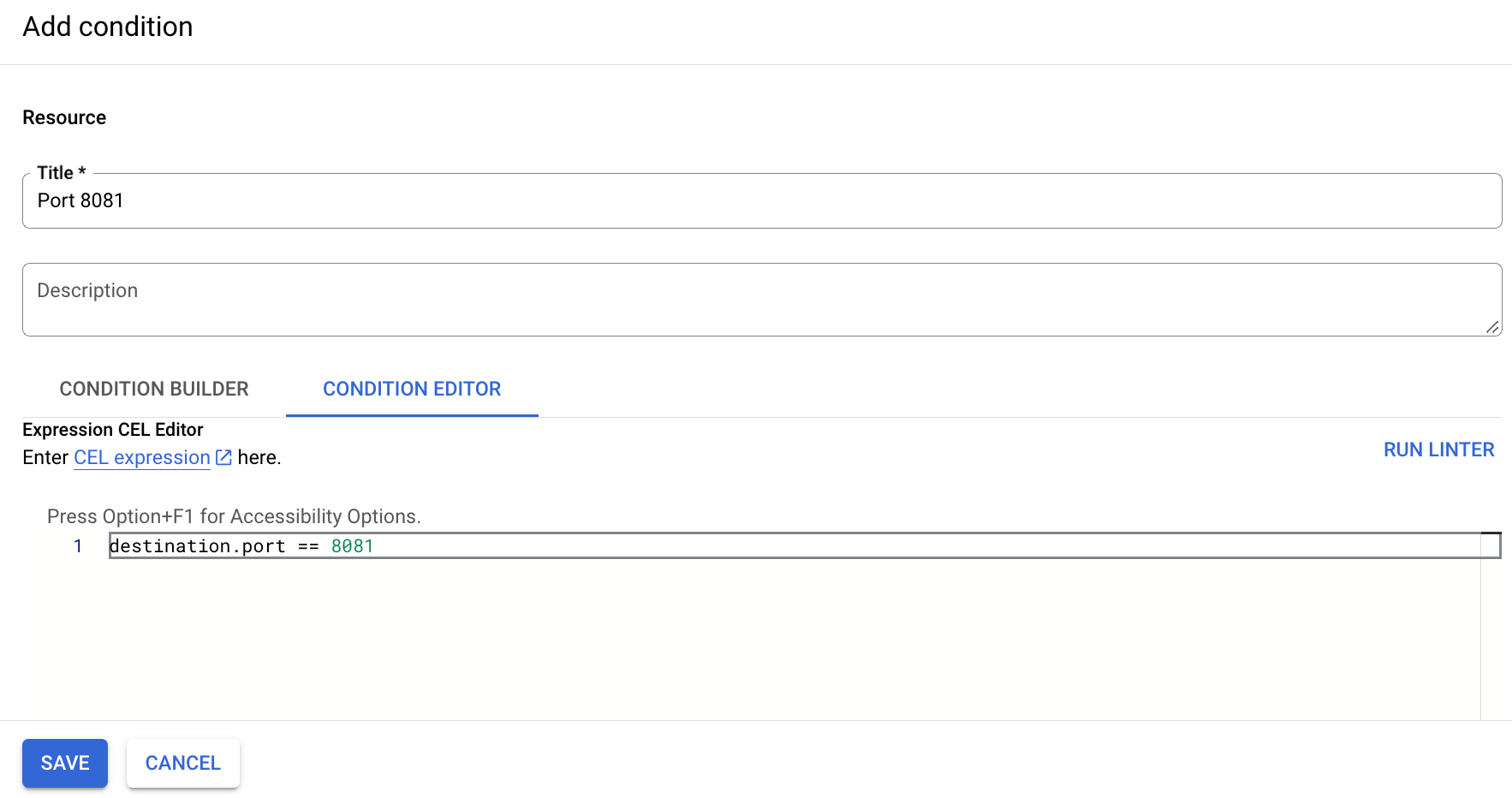
- Clique em Salvar para concluir a concessão de acesso condicional à porta específica ao principal.
gcloud
Use o comando
workstations get-iam-policyda CLIgcloudpara receber a política do IAM da estação de trabalho. Esse comando gera a política no arquivo:/tmp/WORKSTATIONS_NAME.yaml. Se o arquivo existir, ele será substituído.gcloud workstations get-iam-policy WORKSTATIONS_NAME \ --cluster=WORKSTATIONS_CLUSTER_NAME \ --config=WORKSTATIONS_CONFIG_NAME \ --region=LOCATION \ --project=WORKSTATIONS_PROJECT_ID \ > /tmp/WORKSTATIONS_NAME.yamlSubstitua:
WORKSTATIONS_NAME: o nome da estação de trabalho.WORKSTATIONS_CONFIG_NAME: o nome da configuração da estação de trabalho.WORKSTATIONS_CLUSTER_NAME: o nome do cluster da estação de trabalho.LOCATION: o nome da região do cluster de estação de trabalho.WORKSTATIONS_PROJECT_ID: o ID do projeto do Cloud Workstations que contém sua estação de trabalho.
O formato YAML da política é baixado para
/tmp/WORKSTATIONS_NAME.yaml:bindings: - members: - user:222larabrown@gmail.com role: roles/workstations.user etag: BwYdnV9Eg7Y= version: 1Para conceder acesso condicional a um principal, adicione a seguinte expressão de condição destacada ao arquivo de política que você baixou na etapa anterior.
Não modifique a ETag. Verifique se a versão está especificada como
3, já que essa política inclui o campocondition.Exemplo:
bindings: - members: - user:YOUR_ID role: roles/workstations.user - condition: expression: destination.port == WORKSTATIONS_PORT title: Port WORKSTATIONS_PORT members: - user:PRINCIPAL role: roles/workstations.user etag: BwYlui8uSXo= version: 3Substitua:
YOUR_ID: seu ID de login. Por exemplo,222larabrown@gmail.com.PRINCIPAL: o principal com quem você quer compartilhar o acesso à porta WORKSTATIONS_PORT da estação de trabalho. Por exemplo,baklavainthebalkans@gmail.com.WORKSTATIONS_PORT: a porta da estação de trabalho em que o servidor de demonstração está detectando.
Defina a política do IAM da estação de trabalho usando o comando
gcloudda CLIworkstations set-iam-policy.gcloud workstations set-iam-policy WORKSTATIONS_NAME \ --cluster=WORKSTATIONS_CLUSTER_NAME \ --config=WORKSTATIONS_CONFIG_NAME \ --region=LOCATION \ --project=WORKSTATIONS_PROJECT_ID \ /tmp/WORKSTATIONS_NAME.yamlSubstitua:
WORKSTATIONS_NAME: o nome da estação de trabalho.WORKSTATIONS_CONFIG_NAME: o nome da configuração da estação de trabalho.WORKSTATIONS_CLUSTER_NAME: o nome do cluster da estação de trabalho.LOCATION: o nome da região do cluster de estação de trabalho.WORKSTATIONS_PROJECT_ID: o ID do projeto do Cloud Workstations que contém sua estação de trabalho.
Depois que a política do IAM da estação de trabalho for atualizada, o principal poderá acessar a porta especificada da estação de trabalho.
Compartilhar o URL da estação de trabalho
O principal poderá acessar a porta especificada com o seguinte URL da estação de trabalho:
https://WORKSTATIONS_PORT-WORKSTATIONS_NAME.WORKSTATIONS_CLUSTER_NAME.cloudworkstations.dev
Os marcadores representam o seguinte:
WORKSTATIONS_PORT: a porta em que o servidor de demonstração está escutando.WORKSTATIONS_NAME: o nome da estação de trabalho.WORKSTATIONS_CLUSTER_NAME: o identificador do cluster gerado aleatoriamente.cloudworkstations.dev: o nome de domínio padrão de uma estação de trabalho.
O principal não poderá acessar outras portas da estação de trabalho a que não tem acesso.

