借助 Identity-Aware Proxy (IAP),您可以管理对Google Cloud外部基于 HTTP 的应用的访问权限。这包括企业数据中心中的本地应用。
如需了解如何使用 IAP 保护本地应用,请参阅为本地应用设置 IAP。
简介
IAP 使用 IAP 本地连接器定位本地应用。On-Prem 连接器使用 Cloud Deployment Manager 模板创建执行以下操作所需的资源:托管 IAP On-Prem 连接器并将其部署到启用 IAP 的Google Cloud 项目,同时将经过身份验证和授权的请求转发到本地应用。
本地连接器会创建以下资源:
- 一个 Cloud Service Mesh 部署,充当本地应用的代理。
- 外部应用负载平衡器,用作请求的入站流量控制器。
- 路由规则。
部署可以采用多个 Cloud Service Mesh 后端服务,这些服务在一个外部应用负载平衡器后面运行。每个后端服务均会映射到单个本地应用。
部署 IAP 本地连接器并为新创建的本地连接器后端服务启用 IAP 后,IAP 可通过基于身份和基于上下文的 Identity and Access Management (IAM) 访问权限政策来保护应用。由于 IAM 访问政策在后端服务资源层级配置,因此您能够针对每个本地应用拥有不同的访问控制列表。这意味着只需要一个 Google Cloud项目即可管理对多个本地应用的访问权限。
在本地应用中使用 IAP 的工作原理
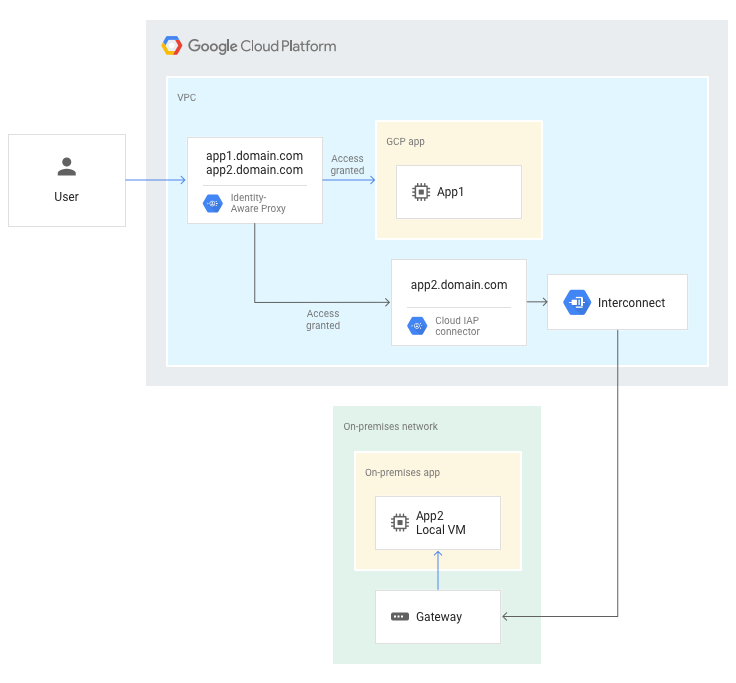
将请求发送到托管在 Google Cloud上的应用后,IAP 会对用户请求进行身份验证和授权。然后,IAP 会授予用户对 Google Cloud 应用的访问权限。
在请求发送到本地应用后,IAP 会对用户请求进行身份验证和授权。然后,IAP 会将请求路由到 IAP 本地连接器。IAP 本地连接器可通过混合连接网络端点组将请求从 Google Cloud 转发到本地网络。
下图显示了针对Google Cloud 应用 (app1) 和本地应用 (app2) 的网络请求的高级流量。
路由规则
配置 IAP 连接器部署时,您可以配置路由规则。这些规则会将进入 DNS 主机名入站点的经过身份验证和授权的网络请求路由到作为目的地的 DNS 主机名。
以下是为 IAP 连接器 Deployment Manager 模板定义的 routing 参数的示例。
routing: - name: hr mapping: - name: host source: www.hr-domain.com destination: hr-internal.domain.com - name: sub source: sheets.hr-domain.com destination: sheets.hr-internal.domain.com - name: finance mapping: - name: host source: www.finance-domain.com destination: finance-internal.domain.com
- 每个
routing名称对应一个由 Ambassador 创建的新 Compute Engine 后端服务资源。 mapping参数指定后端服务的 Ambassador 路由规则列表。- 路由规则的
source会映射到destination,其中source是进入Google Cloud的请求的网址,destination是对用户进行授权和身份验证后 IAP 将流量路由到的本地应用的网址。
下表演示了将传入请求从 www.hr-domain.com 路由到 hr-internal.domain.com 的示例规则:
| Compute Engine 后端服务 | 路由规则名称 | 来源 | 目的地 |
|---|---|---|---|
| hr | hr-host | www.hr-domain.com | hr-internal.domain.com |
| hr-sub | sheets.hr-domain.com | sheets.hr-internal.domain.com | |
| finance | finance-host | www.finance-domain.com | finance-internal.domain.com |
后续步骤
- 了解如何使用 IAP 保护本地应用的安全。
- 详细了解 IAP 的工作原理。

