This page describes how Identity-Aware Proxy (IAP) handles TCP forwarding. To learn how to grant principals access to tunneled resources and how to create tunnels that route TCP traffic, see Using IAP for TCP forwarding.
Introduction
IAP's TCP forwarding feature lets you control who can access administrative services like SSH and RDP on your backends from the public internet. The TCP forwarding feature prevents these services from being openly exposed to the internet. Instead, requests to your services must pass authentication and authorization checks before reaching their target resource.
Exposing administrative services directly to the internet when running workloads in the cloud introduces risk. Forwarding TCP traffic with IAP lets you reduce that risk by allowing only authorized users to access these sensitive services.
Because this feature is specifically aimed at administrative services, it doesn't support load-balanced targets.
Calling the IAP TCP forwarding service isn't supported on mobile devices.
How IAP's TCP forwarding works
IAP's TCP forwarding feature lets users connect to arbitrary TCP ports on Compute Engine instances. For general TCP traffic, IAP creates a listening port on the local host that forwards all traffic to a specified instance. IAP then wraps all traffic from the client in HTTPS. Users can access the interface and port if they pass the authentication and authorization checks of the target resource's Identity and Access Management (IAM) policy.
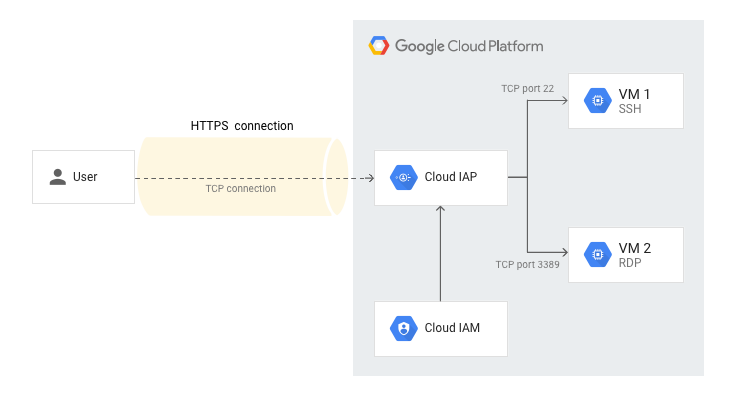
When you establish an SSH connection using gcloud compute ssh,
the command wraps the SSH connection inside HTTPS and forwards it to the remote instance
without requiring a listening port on the local host.
Enabling IAP on an administrative resource doesn't automatically block direct requests to the resource. IAP only blocks TCP requests that aren't from IAP TCP forwarding IPs to relevant services on the resource.
TCP forwarding with IAP doesn't require a public, routable IP address assigned to your resource. Instead, it uses internal IPs.
What's next
- Learn how to connect to TCP ports on instances and grant principals access to tunneled resources.
