Insights uses per-project service accounts to access resources in the customer project—such as audio and transcript files in your Google Cloud storage bucket—during analysis. Each project's service account is automatically created the first time you access any user resources. By default, the service account is automatically given some default access—such as Google Cloud storage access—to the project.
After you create your first conversation, you should see the service account
permissions in your project's IAM settings. If you accidentally remove or don't see the
service account permissions, then you can manually give it access to the correct permissions. The account
always has the form service-<project_number>@gcp-sa-contactcenterinsights.iam.gserviceaccount.com.
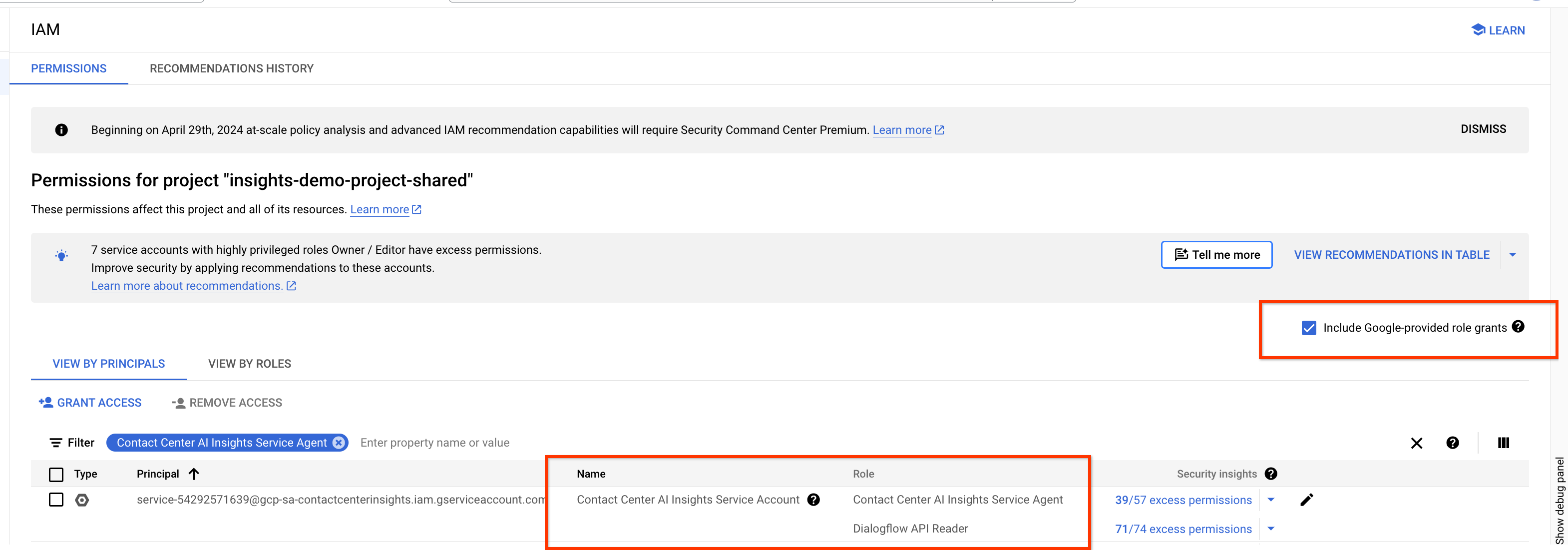
To change an account's permissions manually, navigate to the IAM panel of the Insights console and give that user the contactcenterinsights.serviceAgent permission. The service account can also be given fine-grained permissions, though too many of these can lead to instability.
If you see an error message like the following, first verify that your Insights service account exists in your IAM configuration.
"message": "IAM permission 'dialogflow.participants.suggest' on 'projects/<project>/locations/global/conversations/fake_conversation_id/participants/fake_participant_id' denied."
Then, make sure Include Google-provided role grants is checked:
Audio export
To export audio from Agent Assist or Dialogflow to Insights, verify that service-<project_number>@gcp-sa-dialogflow.iam.gserviceaccount.com has the dialogflow.serviceAgent role.
Manual service agent creation
You can create the Conversational Insights service agent with the following command:
gcloud beta services identity create --service=contactcenterinsights.googleapis.com --project=<project_id>
