批准 Access Approval 请求
本文档介绍了如何批准 Access Approval 请求。
准备工作
请确保您了解概览页面中的概念。
将项目、文件夹或组织的“Access Approval Approver”(
roles/accessapproval.approver) IAM 角色授予您希望能够执行批准操作的主账号。您可以向单个用户、服务账号或 Google 群组授予“访问权限审批批准者”IAM 角色。如果您使用的是自定义签名密钥,还必须向资源的 Access Approval 服务账号授予 Cloud KMS CryptoKey Signer/Verifier (
roles/cloudkms.signerVerifier) IAM 角色。如果您使用的是 Google 管理的签名密钥,则无需提供任何其他权限。如需了解如何授予 IAM 角色,请参阅授予单个角色。
配置设置以接收通知
您可以通过以下方式接收 Access Approval 请求:
- 通过电子邮件接收请求。
- 通过 Pub/Sub 接收请求。
您可以按照设置电子邮件和 Pub/Sub 通知中的说明,同时选择这两种选项。
批准 Access Approval 请求
将部分用户注册为审批人后,这些用户会收到所有访问权限请求。
控制台
如需使用Google Cloud 控制台批准 Access Approval 请求,请执行以下操作:
如需查看所有待处理的审批请求,请前往 Google Cloud 控制台中的 Access Approval 页面。
如果您已选择通过电子邮件接收访问权限审批请求,也可以点击发送给您的电子邮件中带有批准请求的链接,前往此页面。
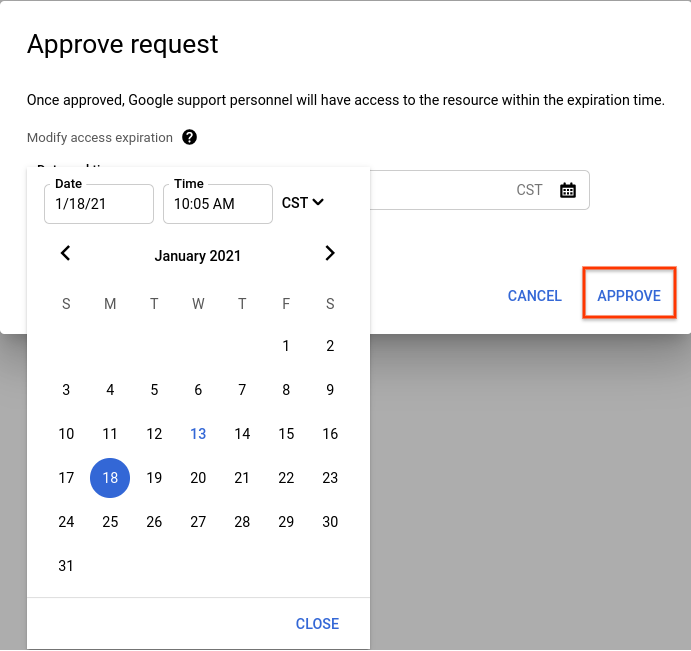
如要批准申请,请点击批准。
您也可以选择拒绝请求。拒绝请求是可选操作,因为即使您不拒绝请求,访问也会被拒绝。
如果您未在 14 天内或在请求到期前批准 Google 员工的访问权限请求,系统会自动拒绝该请求。
在随即打开的对话框中,选择您希望访问权限失效的日期和时间。
选择批准以批准在设定的到期日期和时间之前的访问权限。
可选:如需在批准请求后验证其签名,请按照验证请求签名中的步骤操作。
cURL
如需使用 c网址 批准 Access Approval 请求,请执行以下操作:
- 从 Pub/Sub 消息中获取
approvalRequest名称。 进行 API 调用以批准或拒绝该
approvalRequest。# HTTP POST request with empty body (an effect of using -d '') # service-account-credential.json is attained by going to the # IAM -> Service Accounts menu in the cloud console and creating # a service account. curl -H "$(oauth2l header --json service-account-credentials.json cloud-platform)" \ -d '' https://accessapproval.googleapis.com/v1/projects/<var>PROJECT_ID</var>/approvalRequests/<var>APPROVAL_REQUEST_ID</var>:approve您可以使用以下任一选项回复请求:
操作 影响 Google 访问状态 :approve批准请求。 在批准前处于已拒绝状态,在批准后处于已批准状态。 :dismiss拒绝要批准的请求。我们建议您关闭访问权限请求,而不是不采取任何措施。拒绝访问请求后,Google 员工会进行跟进。 在拒绝前处理已拒绝状态,在拒绝后处于已拒绝状态。 无操作 Google 员工访问仍被拒绝。经过 requestedExpiration时间之后,Google 员工需要发出新请求来访问资源。在未采取任何操作之前处于已拒绝状态,在到期时间之后处于已拒绝状态。
您批准请求后,请求状态会更改为 Approved。具有与批准范围相匹配的特征的任何 Google 员工都可以在批准的时间范围内进行访问。这些匹配的特征包括相同的理由、位置或办公桌位置。
Access Approval 不会向请求访问权限的 Google 员工提供任何 IAM 角色或任何新权限。
如果您不批准 Google 员工的访问请求,Google 员工将被拒绝访问。拒绝请求只会将其从待处理请求列表中移除。如果您未能拒绝批准请求,则访问将继续被拒绝。
启用后,Access Transparency 会记录您批准的对客户数据的所有访问。
在批准到期或访问理由不再有效之前,Google 员工可以访问相应资源。例如,如果 Google 员工请求访问的支持请求已关闭,访问权限就会到期。

