The Google Cloud console, Google Cloud CLI, and REST API all display error messages when a user tries to access a resource that they don't have permission to access. When a user encounters a permission error, they can request access to the resource. This generates an email that's sent to your organization's technical Essential Contact.
When the administrator clicks the link in the generated email, they're directed to the policy remediation summary. Administrators can also access the policy remediation summary by clicking View troubleshooting details on a permission error message and then clicking Policy Troubleshooter. This page describes the request details, including the requesting principal, resource, and the permissions that the principal is requesting.
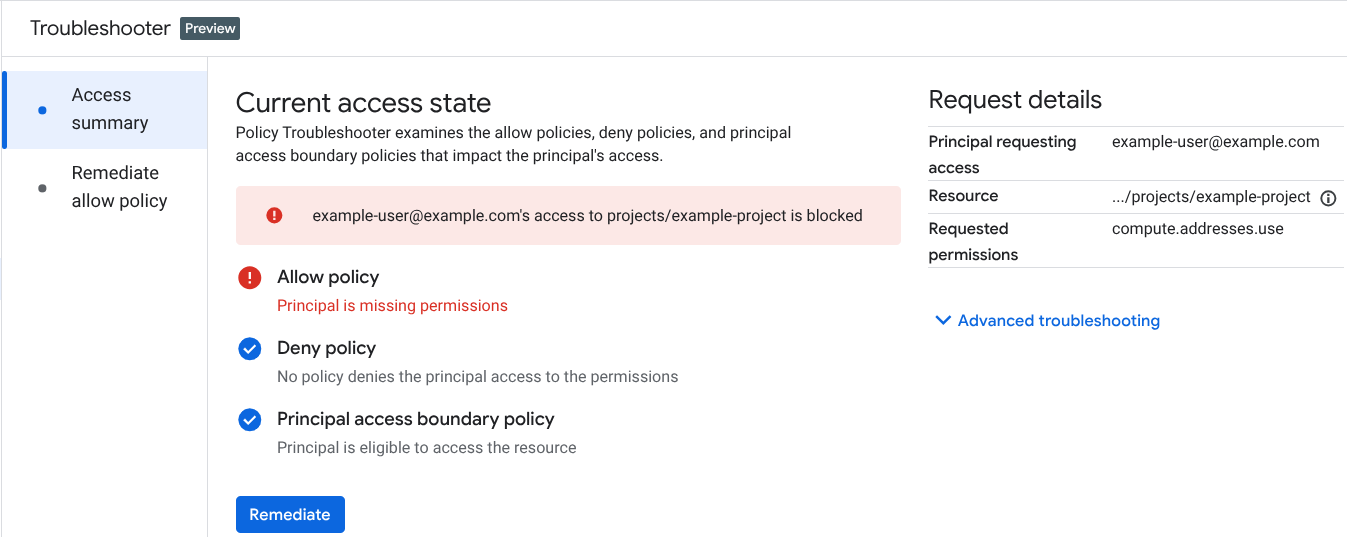

The Current access state section summarizes the results for each policy type (specifically, allow policies, deny policies, and principal access boundary policies) and states the overall outcome. The outcome indicates whether the principal can access the resource, according to the relevant policies.
You can get more information about the policies that are blocking the user's access by clicking Advanced troubleshooting.
Click Remediate to view options for remediating that user's access issues. To learn the different ways that you can resolve permission errors caused by each of the different policy types using the Google Cloud console, see the following:
- Remediate allow policy permission errors
- Remediate deny policy permission errors
- Remediate principal access boundary permission errors
Remediate allow policy
The Remediate allow policy page shows the permissions that the user is missing. To resolve access blocked by an allow policy, you can either grant that user access or create a Privileged Access Manager entitlement for the user. After you create the entitlement, the user can request it to access the resource.
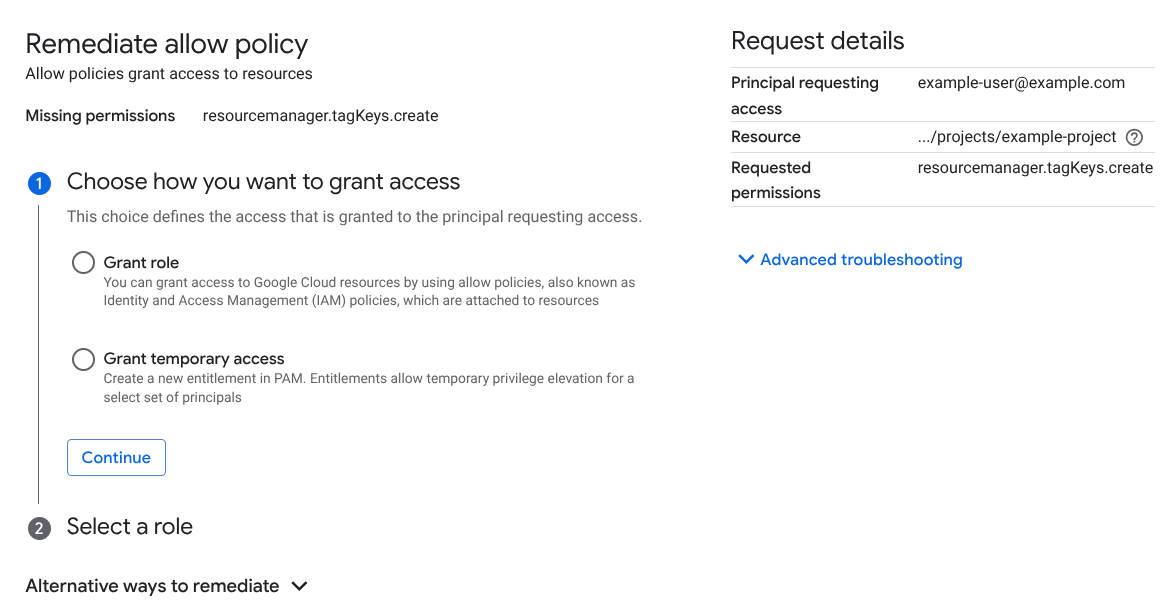

To grant the user access, do the following:
- Select Grant role.
- Click Continue.
- Select an applicable role to view details about that role.
- Click Grant access.
To create a new Privileged Access Manager entitlement, do the following:
- Select Grant temporary access.
- Click the applicable role to grant to view details about that role.
Click Create entitlement.
In the Create a new entitlement pane, enter the details for the entitlement:
- Enter a name for the new entitlement.
- Select the maximum duration of the grant.
- Click Next.
- Optionally add more requesters for this entitlement.
- Click Next.
- Add at least one principal to approve entitlement requests or select Activate access without approvals.
- Click Next.
- Optionally enter the email addresses of any administrators that you want to notify.
- Click Done, and then click Create entitlement.
For more information about Privileged Access Manager, see Create entitlements in Privileged Access Manager.
If there isn't one role that contains all of the permissions required by the user, no roles or entitlements are suggested.
For alternative methods of remediating the user's access, see Resolve allow policy permission errors.
Remediate deny policy
Deny policies are attached to a Google Cloud organization, folder, or project. A deny policy contains deny rules, which identify principals and list the permissions that the principals can't use.
The Remediate deny policy page shows the deny policy that prevents the user from using the permission and suggests several methods for remediating the user's access.
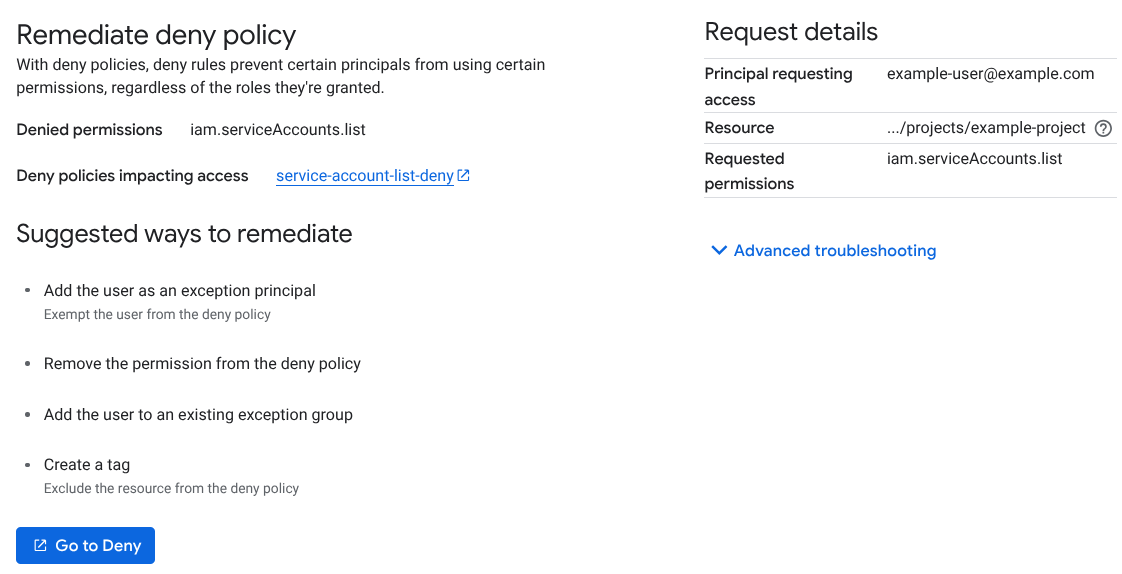

The suggested methods for remediating access requests related to deny policies include the following:
Exempt the user from the deny policy.
Remove the permission from the deny policy.
Create a tag to exclude the resource from the deny policy.
Remediate principal access boundary
By default, principals are eligible to access any Google Cloud resource. However, if they're subject to any principal access boundary policy, then they're only eligible to access the resources listed in the principal access boundary policies that they're subject to. In these cases, a principal access boundary policy might prevent a principal from accessing a resource.
The Remediate principal access boundary page shows the principal access boundary policy that prevents the user from accessing the resource and suggests several methods for remediating the user's access.
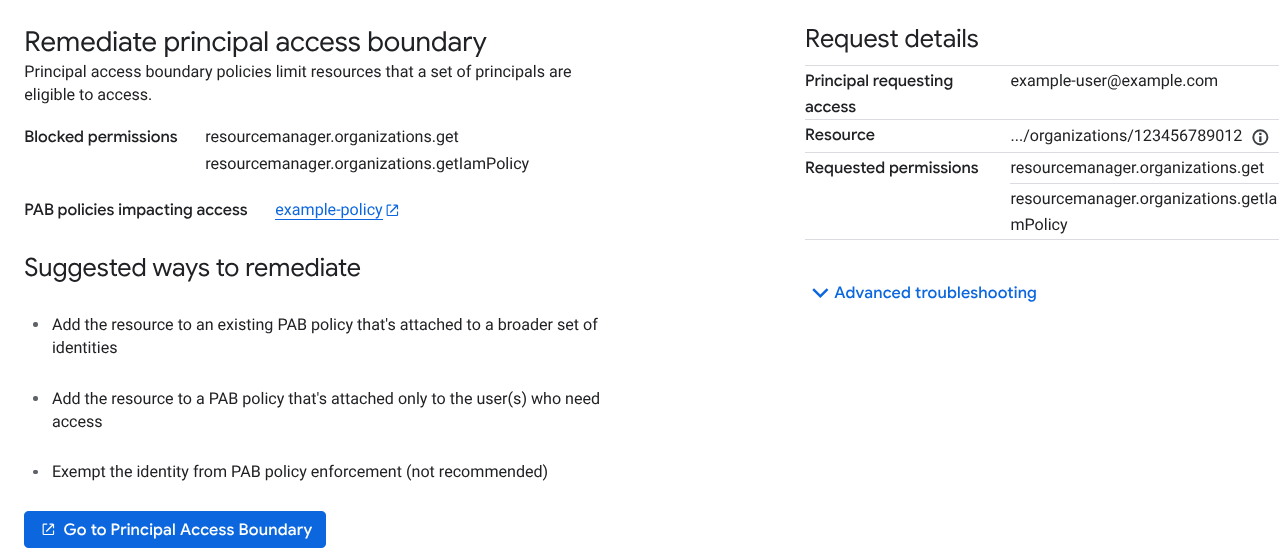

The suggested methods for remediating access requests related to principal access boundary policies include the following:
Add the resource to an existing principal access boundary policy attached to a broader set of identities.
Add the resource to a principal access boundary policy that's attached to the user who needs access.
Not recommended: exempt the identity from principal access boundary enforcement.
What's next
- Use the permissions reference or the predefined roles reference to determine which role to grant to a user who is missing permissions.
- Read about the other Policy Intelligence tools, which help you understand and manage your policies to proactively improve your security configuration.
